Cloudflare goes InterPlanetary – Introducing Cloudflare’s IPFS Gateway


Today we’re excited to introduce Cloudflare’s IPFS Gateway, an easy way to access content from the InterPlanetary File System (IPFS) that doesn’t require installing and running any special software on your computer. We hope that our gateway, hosted at cloudflare-ipfs.com, will serve as the platform for many new highly-reliable and security-enhanced web applications. The IPFS Gateway is the first product to be released as part of our Distributed Web Gateway project, which will eventually encompass all of our efforts to support new distributed web technologies.
This post will provide a brief introduction to IPFS. We’ve also written an accompanying blog post describing what we’ve built on top of our gateway, as well as documentation on how to serve your own content through our gateway with your own custom hostname.
Quick Primer on IPFS

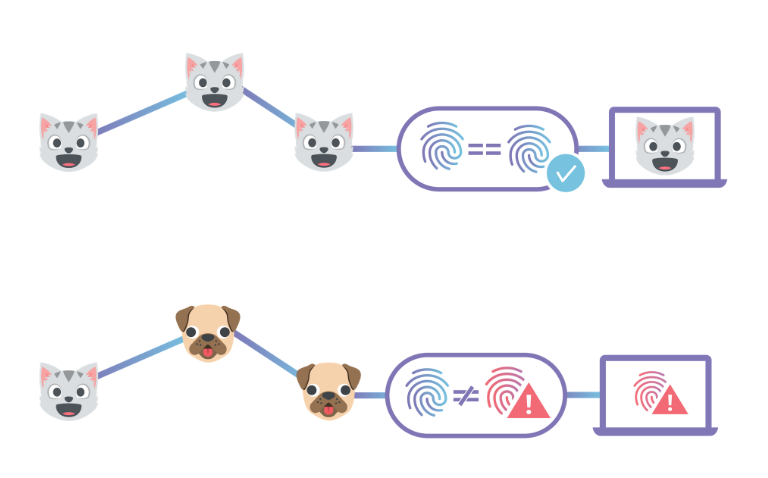
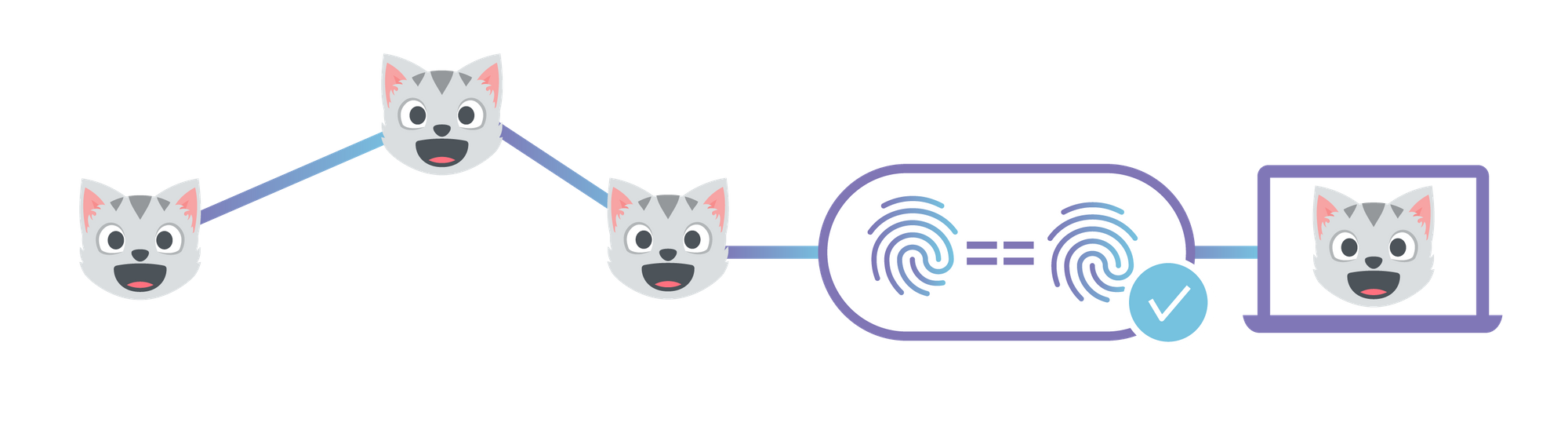
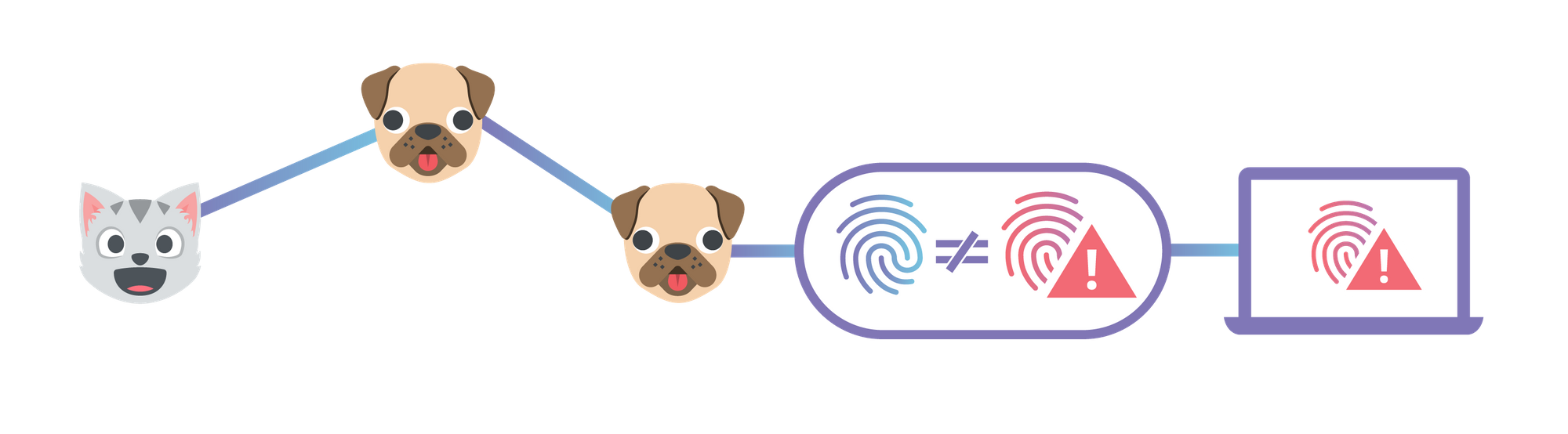
Usually, when you access a website from your browser, your browser tracks down the origin server (or servers) that are the ultimate, centralized repository for the website’s content. It then sends a request from your computer to that origin server, wherever it is in the world, and that server sends the content back to your computer. This system has served the Internet well for decades, Continue reading

 The SDN company hired Cisco's Avinash Parwaney as VP of engineering.
The SDN company hired Cisco's Avinash Parwaney as VP of engineering.




 Virtualization is the key to making new 5G use cases a reality, according to top tech chiefs at U.S. wireless operators.
Virtualization is the key to making new 5G use cases a reality, according to top tech chiefs at U.S. wireless operators.