Bharti Airtel’s Chairman Sees 5G Slicing as a Solution to Net Neutrality Debate
 He promised on behalf of the “mobile operator fraternity” that they will never throttle speeds.
He promised on behalf of the “mobile operator fraternity” that they will never throttle speeds.
 He promised on behalf of the “mobile operator fraternity” that they will never throttle speeds.
He promised on behalf of the “mobile operator fraternity” that they will never throttle speeds.
A few weeks ago, I set out to the beautiful city of Vancouver’s convention center, along with a boatload of rocket turtles and a stellar team. It was a great time with a wonderful scenic view of the ocean. I’ve been at Cumulus a few months now, but I can’t help but enjoy looking around, seeing the friends I’ve made in the industry, and the friends and companies Cumulus has worked with over the years. It is exciting to have thousands of people coming together at OpenStack Summit Vancouver to work on a shared goal.

This year, we were lucky enough to have our very own Pete Lumbis take the stage with David Iles of Mellanox to present our joint solution around the latest SDN revolution, which is centered on creating efficient virtualized data center networks using VXLAN & EVPN.
In the next few paragraphs, I’ll share some highlights of the event, some photos, and a recap of that exact discussion. There was a lot to learn and discover, and I’m excited to share the details.
On our first day, lots of things were going on — we Continue reading
Training with INE will not only keep you team on the cutting edge of the industry’s leading networking technologies, it will also put you on the path to becoming a Cisco Partner; a tangible way to show clients that you’re on the forefront of Cisco technologies and training. Cisco registered partners enjoy access to a wide variety of Cisco channel partner tools and are eligible to apply for Cisco certifications and specializations.
There are three levels of certification that a team can achieve; Cisco Select, Premier and Gold. Each level requires certain prerequisites, which INE’s industry-leading network training can provide. The three types of certifications are:

For more information contact our training advisors at [email protected] or by phone at +1-877-224-8987 or +1-775-862-4344 (outside the U.S.)
It is safe to say that VMware would have been perfectly happy if Docker containers had never been invented. …
A Tale Of Two – Well, Three Or Four – Kubernetes was written by Timothy Prickett Morgan at .
Today's IPv6 Buzz podcast tackles the slow uptake of v6 in the enterprise, and how that might affect IoT, cloud, and network programmability strategies.
The post IPv6 Buzz 003: IPv6 In The Enterprise appeared first on Packet Pushers.
 In addition to storing video data for pre-game preparation and game-time decision making, Datrium DVX will also support the scouting database used for serving statistics on college and NFL players in real-time on draft day.
In addition to storing video data for pre-game preparation and game-time decision making, Datrium DVX will also support the scouting database used for serving statistics on college and NFL players in real-time on draft day.
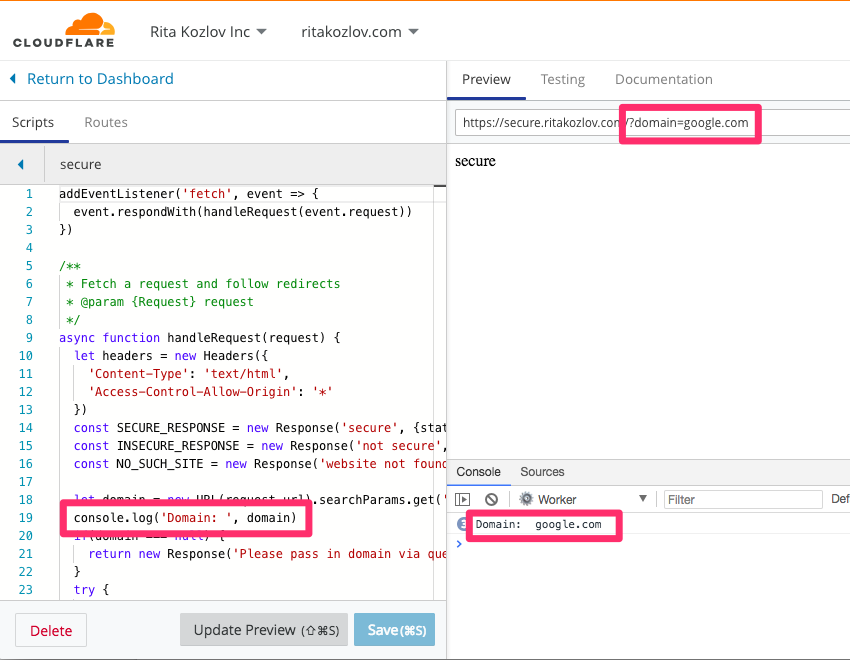
In preparation for Chrome’s Not Secure flag, which will update the indicator to show Not Secure when a site is not accessed over https, we wanted people to be able to test whether their site would pass. If you read our previous blog post about the existing misconceptions around using https, and preparing your site, you may have noticed a small fiddle, allowing you to test which sites will be deemed “Secure”. In preparation for the blog post itself, one of our PMs approached me asking for help making this fiddle come to life. It was a simple ask: we need an endpoint which runs logic to see if a given domain will automatically redirect to https.
The logic and requirements turned out to be very simple:
Make a serverless API endpoint
Input: domain (e.g. example.com)
Output: “secure” / “not secure”
Logic:
if http://example.com redirects to https://example.com
Return “secure”
Else
Return “not secure”
One additional requirement here was that we needed to follow redirects all the way; sites often redirect to http://www.example.com first, and only then redirect to https. That is an additional line of code I was prepared to handle.
I’ve done some Continue reading
 AT&T’s Andre Fuetsch will head the group’s board, which is made up of delegates from 12 operators.
AT&T’s Andre Fuetsch will head the group’s board, which is made up of delegates from 12 operators.
 The report includes a glossary of edge computing terms and definitions that is being funneled into The Linux Foundation.
The report includes a glossary of edge computing terms and definitions that is being funneled into The Linux Foundation.
3 people sent me their feedbacks after they pass February 2018 CCDE Practical/Lab exam. Exam result was announced on May 2018 (2 to 3 months after according to new CCDE Practical exam result policy) but I couldn’t find a chance to share their results on the website. I can’t count anymore how …
Continue reading "3 people passed CCDE Practical/Lab exam on February 2018 from my class"
The post 3 people passed CCDE Practical/Lab exam on February 2018 from my class appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
3 people sent me their feedbacks after they pass February 2018 CCDE Practical/Lab exam. Exam result was announced on May 2018 (2 to 3 months after according to new CCDE Practical exam result policy) but I couldn’t find a chance to share their results on the website. I can’t count anymore how …
Continue reading "3 people passed CCDE Practical/Lab exam on February 2018 from my class"
The post 3 people passed CCDE Practical/Lab exam on February 2018 from my class appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
3 people sent me their feedbacks after they pass February 2018 CCDE Practical/Lab exam. Exam result was announced on May 2018 (2 to 3 months after according to new CCDE Practical exam result policy) but I couldn’t find a chance to share their results on the website. I can’t count anymore how […]
The post 3 people passed CCDE Practical/Lab exam on February 2018 from my class appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
 This brings its total to $39 million. Kleiner Perkins led the funding round with participation from Battery Ventures, Dell Technologies Capital, TenEleven Ventures, and Vertical Venture Partners.
This brings its total to $39 million. Kleiner Perkins led the funding round with participation from Battery Ventures, Dell Technologies Capital, TenEleven Ventures, and Vertical Venture Partners.
 The company’s SDN technology was chosen by CoreSite Realty to help its customers connect to public and private clouds and to adjust bandwidth as needed.
The company’s SDN technology was chosen by CoreSite Realty to help its customers connect to public and private clouds and to adjust bandwidth as needed.
 The company's platform helps developers to automate their application deployment to Kubernetes in as little as 10 minutes and is more Kubernetes-centric than Spinnaker.
The company's platform helps developers to automate their application deployment to Kubernetes in as little as 10 minutes and is more Kubernetes-centric than Spinnaker.