OpenContrail Becomes Tungsten Fabric, Plans Next Release in May
 Juniper Networks will be one of the biggest consumers of Tungsten Fabric, but the name change helps distinguish it from Contrail.
Juniper Networks will be one of the biggest consumers of Tungsten Fabric, but the name change helps distinguish it from Contrail.
 Juniper Networks will be one of the biggest consumers of Tungsten Fabric, but the name change helps distinguish it from Contrail.
Juniper Networks will be one of the biggest consumers of Tungsten Fabric, but the name change helps distinguish it from Contrail.
 Telefónica collaborates with Microsoft Azure on IoT; B.Yond joins the Linux Foundation Deep Learning Foundation; Openwave Mobility launched a 5G telco cloud database.
Telefónica collaborates with Microsoft Azure on IoT; B.Yond joins the Linux Foundation Deep Learning Foundation; Openwave Mobility launched a 5G telco cloud database.
 The SD-WAN API leverages and extends Cisco's SD-WAN and its network monitoring platform by isolating problems using underlay and overlay network data.
The SD-WAN API leverages and extends Cisco's SD-WAN and its network monitoring platform by isolating problems using underlay and overlay network data.
It’s been 5 months since WTDC17 concluded and I had time to reflect on the outcomes of the conference and the experience itself. WTDC sets the ITU’s development agenda and in Argentina last October over 1000 government delegates from close to 135 countries gathered during the two-week period. They were there to discuss a range of issues and shape the development sector’s priorities for the next four years. For me, it was a trip of many firsts: my first experience as an observer participating in a multilateral conference; my first trip to South America; and, as a visually impaired person, the eighteen hours flight duration was my first such experience.
To recall, I was a member of the Internet Society delegation as a Fellow. For me, the two motivators to apply for the fellowship opportunity were: first, the theme for WTDC17 (“ICTs for Sustainable Development Goals”) and possibility to make a difference. Second, my quest to learn even more about Internet Governance processes and to participate in the discussions.
WTDC17 had a packed agenda that included ceremonial events marking the 25th Anniversary of the Development Sector and side events on a range of Sustainable Development Goal (SDG) topics.
 The security startup, founded by former Juniper, Fortinet, Barracuda, and Aerohive executives, exited stealth mode with its AI-based breach detection platform.
The security startup, founded by former Juniper, Fortinet, Barracuda, and Aerohive executives, exited stealth mode with its AI-based breach detection platform.
 The platform allows companies to better manage data that must remain on premises due to compliance, security, or latency reasons.
The platform allows companies to better manage data that must remain on premises due to compliance, security, or latency reasons.
 The FCC wants to ban any spending from the Universal Service Fund on networking equipment that could pose a security threat.
The FCC wants to ban any spending from the Universal Service Fund on networking equipment that could pose a security threat.
Hey, it's HighScalability time:

Programmable biology - engineered cells execute programmable multicellular full-adder logics. (Programmable full-adder computations)
If you like this sort of Stuff then please support me on Patreon. And I'd appreciate if you would recommend my new book—Explain the Cloud Like I'm 10—to anyone who needs to understand the cloud (who doesn't?). I think they'll learn a lot, even if they're already familiar with the basics.
Alright, we know you’re hungry for more Cumulus goodness, so we’ve cooked up something new that we think will satiate your appetite for awesome technical content. It’s the perfect mix of one part technical deep-dive, one part fun and just a pinch of silliness. The wait is over — our latest project is hot, fresh and ready to serve!
Okay, enough teasing. Today we’re introducing the new Cumulus Networks video series “Cooking with Cumulus!”
“Wait, what does cooking have to do with networking??” you may think to yourself. Glad you asked. You may already know JR Rivers as the CTO and co-founder of Cumulus Networks, but did you know he’s also a master of the culinary arts? Here at the Mountain View office, we know it’s the start of a good day when JR brings in his homemade food to share. From chocolate chip cookies to paella, we’ve approved (and enjoyed) his many recipes. So, we decided that we wanted to share that gift with the rest of the Cumulus community by combining two of JR’s greatest passions — networking and cooking. The resulting brain child was a video series where we put two networking nerds in a Continue reading
RFC 8360, Resource Public Key Infrastructure (RPKI) Validation Reconsidered, is now published in the RFC libraries.
Resource Public Key Infrastructure (RPKI) aims to improve the security of the Internet routing system, specifically the Border Gateway Protocol (BGP), by establishing a hierarchy of trust for BGP routes. Today, most organizations simply trust that routing updates they get are sent by authorized senders. This is how bad actors and misconfigurations can cause massive routing issues. With RPKI, the receiving organization can verify that the sending organization is authorized to send the routing update.
RPKI works by issuing X.509-based resource certificates to holders of IP addresses and AS numbers to prove assignment of these resources. These certificates are issued to Local Internet Registries (LIRs) by one of the five Regional Internet Registries (RIRs) who allocate and assign these resources in their service regions.
In the IETF, participants have been discussing issues that may arise when resources move across registries. The problem happens when a subordinate certificate “over-claims” resources compared to its parent. According to the standard validation procedure specified in RFC 6487, the whole branch beneath would be invalidated. The closer to Continue reading
In this Network Collective short take, Eyvonne discusses the role of a sales engineer. She highlights the value sales engineers can bring to enterprises and outlines some ways you can get the most out of your relationship with your vendor or VAR sales engineer.
The post Short Take – In Defense of Sales Engineers appeared first on Network Collective.
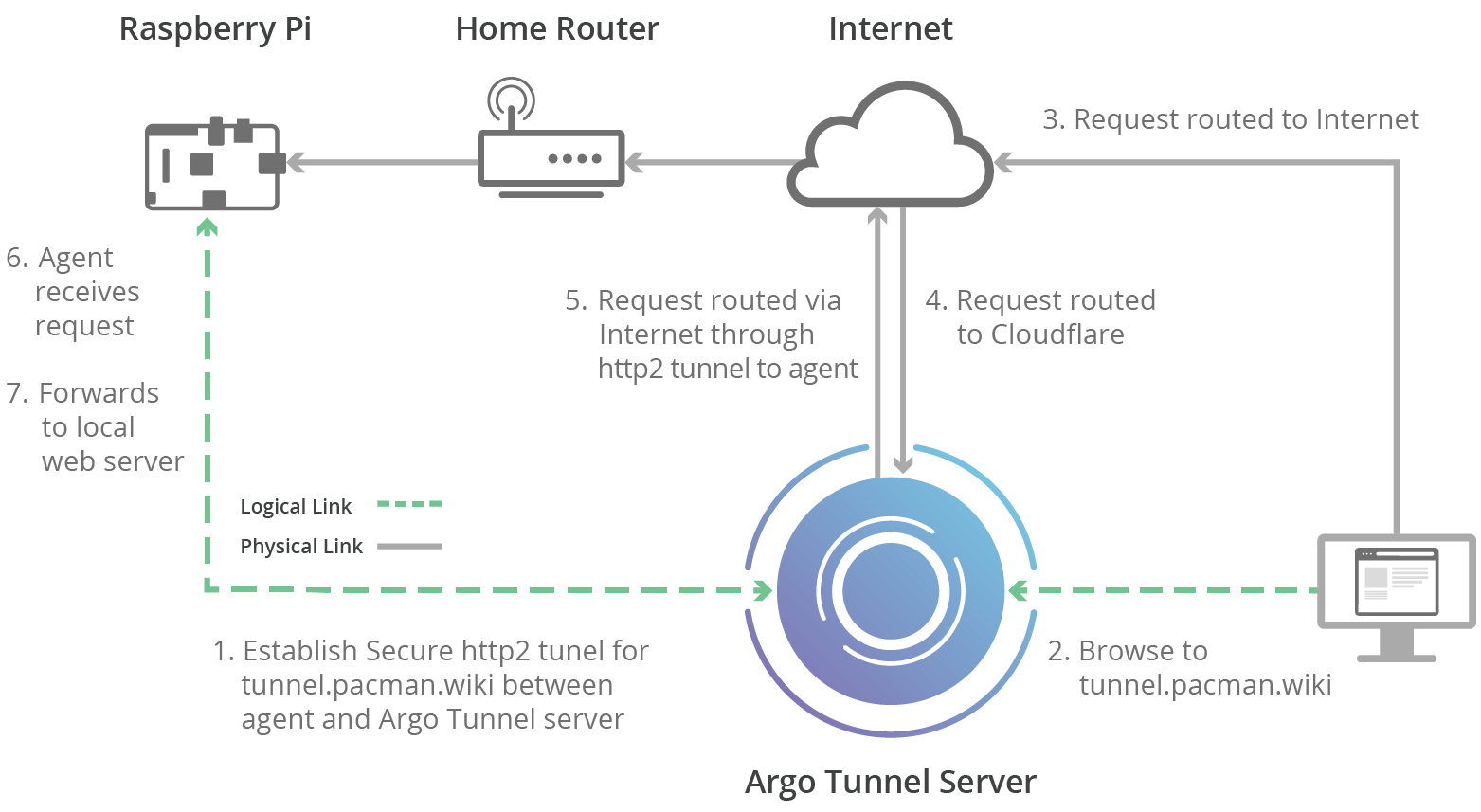
Yesterday Cloudflare launched Argo Tunnel. In the words of the product team:
Argo Tunnel exposes applications running on your local web server, on any network with an Internet connection, without adding DNS records or configuring a firewall or router. It just works.
Once I grokked this, the first thing that came to mind was that I could actually use one of my Raspberry Pi's sitting around to serve a website, without:
Ooooh... so exciting.
I'll assume you already have a Raspberry Pi with Raspbian on it.
Plug the Pi into your router. It should now have an IP address. Look that up in your router’s admin UI:
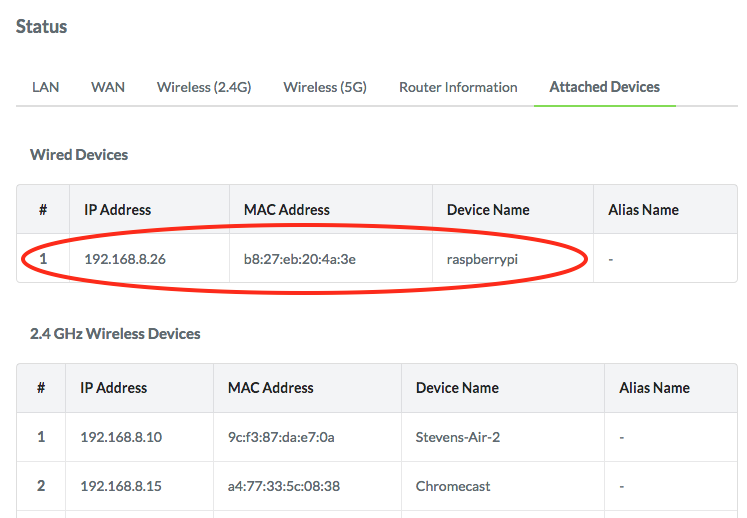
OK, that's promising. Let's connect to that IP using the default pi/raspberry credentials:
$ ssh 192.168.8.26 -l pi
[email protected]'s password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Mar 18 23:24:11 2018 from Continue readingA look at how the new 802.11ad WiFi standard compares with its predecessors, 802.11ac and 802.11ax.
A look at how the new 802.11ad WiFi standard compares with its predecessors, 802.11ac and 802.11ax.
In the second half of his Networks, Buffers and Drops webinar JR Rivers focused on end systems: what tools could you use to measure end-to-end TCP throughput, or monitor performance of an individual socket or the whole TCP stack?
You’ll need at least free ipSpace.net subscription to watch the video.