JUNIPER QFX10K | EVPN-VXLAN | MAC LEARNING VERIFICATION | SINGLE-HOMED ENDPOINT
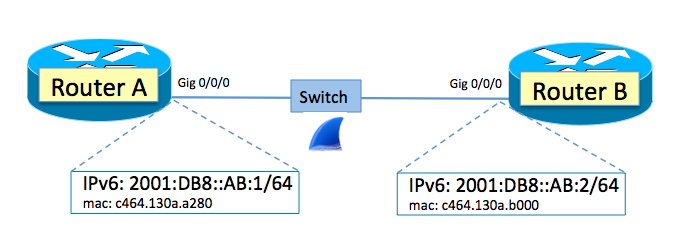
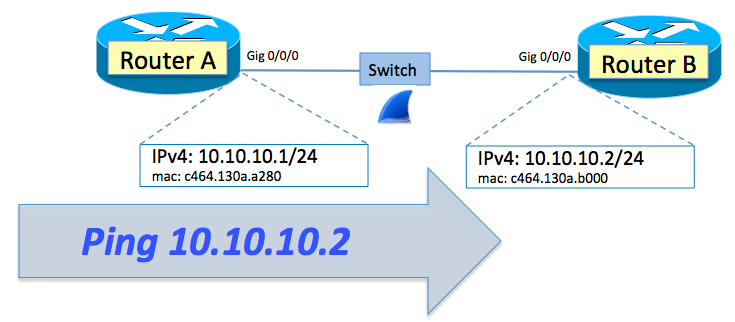
This article is all about EVPN-VXLAN and Juniper QFX technology. I’ve been working with this tech quite a lot over the past few months and figured it would be useful to share some of my experiences. This particular article is probably going to be released in 2 or 3 parts and is focused specifically on the MAC learning process and how to verify behaviour. The first post focuses on a single-homed endpoint connected to the fabric via a single leaf switch. The second part will look at a multihomed endpoint connected via two leaf switches that are utilising the EVPN multihoming feature. And, lastly, the third part will focus on Layer 3 Virtual Gateway at the QFX10k Spine switches. The setup I’m using is based on Juniper vQFX for spine and leaf functions with a vSRX acting as a VR device. I also have a Linux host that is connected to a single leaf switch.
Overview
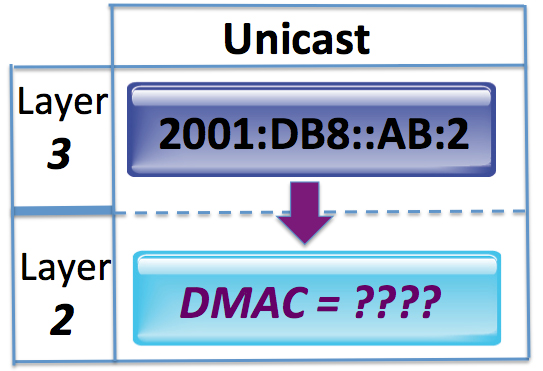
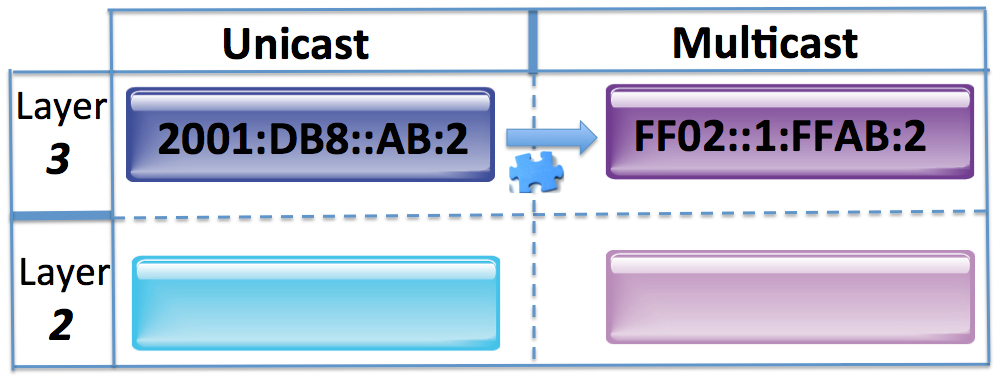
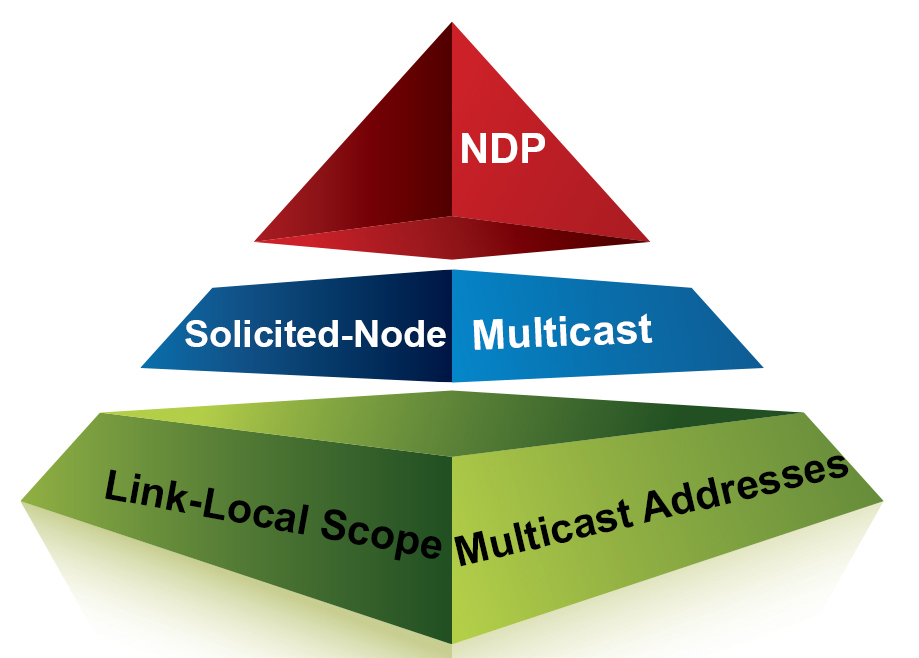
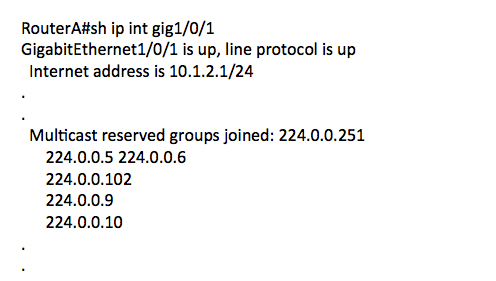
When verifying and troubleshooting EVPN-VXLAN it can become pretty difficult to figure out exactly how the control plane and data plane are programmed and how to verify behaviours. You’ll find yourself looking at various elements such as the MAC table, EVPN database, EVPN routing Continue reading


 The market's IT director felt like he "was held hostage" to some of the T1 agreements.
The market's IT director felt like he "was held hostage" to some of the T1 agreements. The company’s 2015 Wise.io acquisition serves as the foundation for its ML expertise.
The company’s 2015 Wise.io acquisition serves as the foundation for its ML expertise. ETSI NFV endeavors to make VNFs as open as possible.
ETSI NFV endeavors to make VNFs as open as possible. Companies can mix and match connectivity for different site types while maintaining a single network.
Companies can mix and match connectivity for different site types while maintaining a single network. The repository acts like a package manager to ease serverless deployments.
The repository acts like a package manager to ease serverless deployments.