My Personal Look Back on 2017
Continuing in a tradition I started early this year where I take a look back at the year that just passed, I’ve again been very fortunate to have had an amazing year, both in my professional and personal lives. Writing this post is my way of forcing myself to stop and take notice of what I was involved in (something I’m not very good at letting myself do in the moment) and also give readers a chance to see the “me” behind the scenes.
Let’s go through the list!
New Job
In January, I joined the CPOC team at Cisco based in Raleigh, North Carolina. This was  something I worked towards over the course of many months in 2016 and was offered the position in late 2016. Come January of 2017, I had fully transitioned from my prior role and was working full time for CPOC. This change set the stage for everything that happened in my professional life during 2017 and if my gut can be trusted, will end up being a major turning point in my career.
something I worked towards over the course of many months in 2016 and was offered the position in late 2016. Come January of 2017, I had fully transitioned from my prior role and was working full time for CPOC. This change set the stage for everything that happened in my professional life during 2017 and if my gut can be trusted, will end up being a major turning point in my career.
The first thing that we had to do as a result of this new job…
We’re Moving!
…was planning to uproot Continue reading
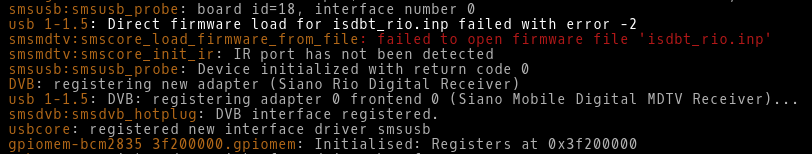
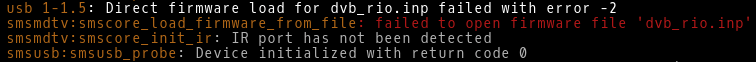

 Standards — once critical for achieving interoperability — have failed to adapt.
Standards — once critical for achieving interoperability — have failed to adapt. Several different groups are trying to bring order to multi-access edge computing.
Several different groups are trying to bring order to multi-access edge computing. Cost and efficiency benefits continue to battle familiarity.
Cost and efficiency benefits continue to battle familiarity. The combined product offers a single-pane of glass for management.
The combined product offers a single-pane of glass for management. I prior shared this post on the LinkedIN publishing platform and my personal blog at HumairAhmed.com. In my prior blog post, I discussed how with VMware Cloud on AWS (VMC on AWS) customers get the best of both worlds for their move to a Software Defined Data Center (SDDC) – the leading compute, storage, and network virtualization stack for...
I prior shared this post on the LinkedIN publishing platform and my personal blog at HumairAhmed.com. In my prior blog post, I discussed how with VMware Cloud on AWS (VMC on AWS) customers get the best of both worlds for their move to a Software Defined Data Center (SDDC) – the leading compute, storage, and network virtualization stack for... 