Nexus 9K –ACI Mode – PART 1
SDN is the Buzzword for Network Guys, How is it related to Nexus 9k in API mode. Let’s Start with SDN to understand the co–relation between SDN and Nexus 9K (ACI Mode). To understand SDN in network terms, SDN does decoupling of control plane and data Plane, thus decision making now done at centralized […]Webinars in This Week
The spring craziness is still in full swing – we’ll have three webinars this week (a first) and I was so busy I didn’t even have time to write about them. Let’s fix that.
Data Center Updates on Monday is the second part of server virtualization, virtual machines and containers update to Data Center 3.0 webinar. We covered virtual machines in the last session (April 25th), this time we’ll talk about containers.
David Barroso (now at Fastly) will talk about NAPALM in Ansible on Tuesday.
Read more ...Learning Python: Week3 (Conditionals and For Loops) -Part 3
As discussed in post ( https://crazyrouters.wordpress.com/2017/02/25/learning-python-kirk-byers-python-course/ ) , i will be sharing the my learning on weekly basis as course continues. This will not only motivate me but also help others who are in phase of learning python 3. This post will focus on Week 3 (Conditionals and For Loops) .This post will focus on […]Savvius Insight and the use of Elastic
Last week Savvius announced upgraded versions of its Insight network visibility appliances. These have the usual performance and capacity increases you’d expect, and fill a nice gap in the market.
But the bit that was most interesting to me was the use of an on-board Elastic stack, with pre-built Kibana dashboards for visualizing network data, e.g.:
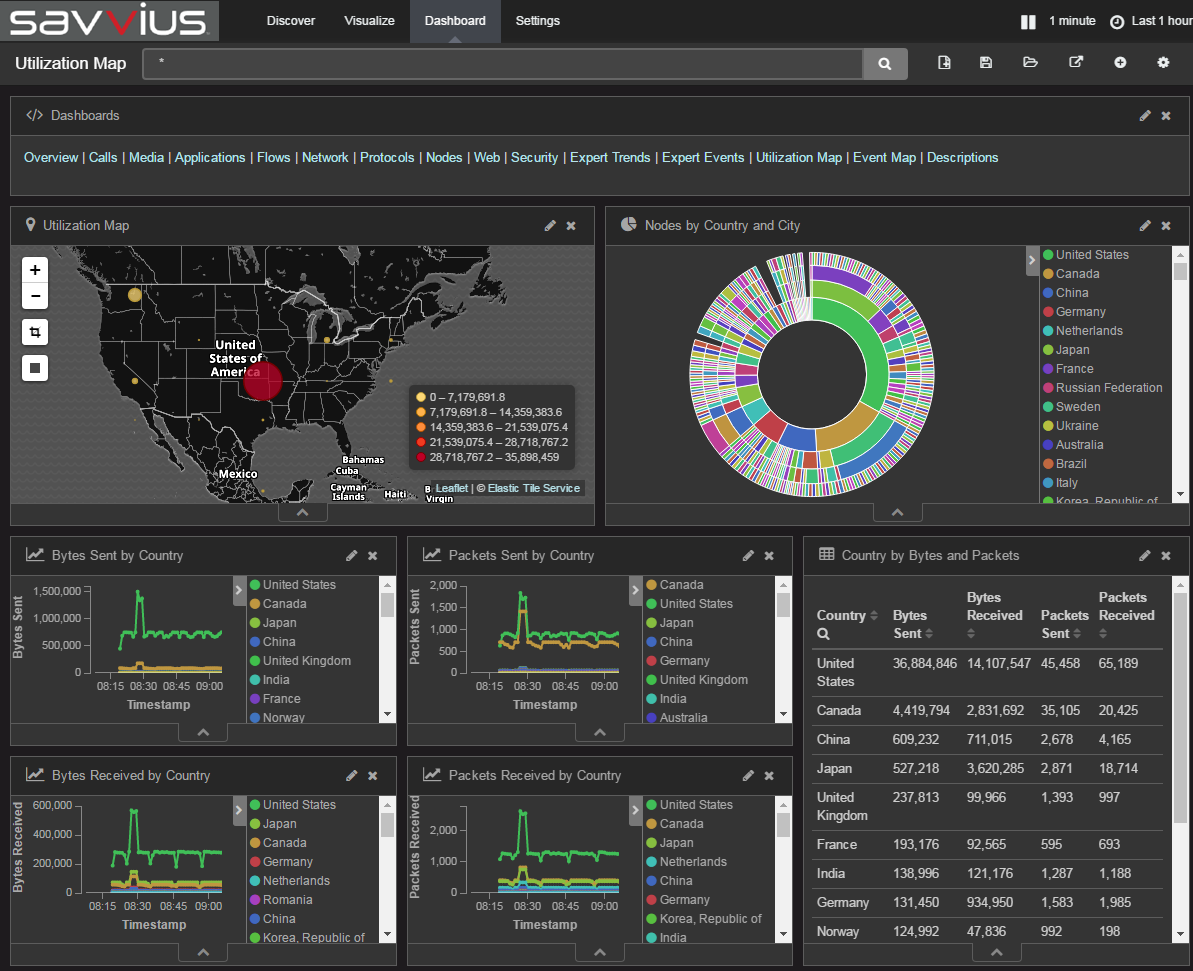
Historically the only way we could realistically create these sorts of dashboards and systems was using Splunk. I’m a big fan of Splunk, but it has a problem: Cost. Especially if you’re trying to analyze large volumes of network data. You might be able to make Splunk pricing work for application data, but network data volumes are often just too large.
Savvius has previously included a Splunk forwarder, to make it easier to get data from their systems into Splunk. But Elastic has reached the point where Splunk is no longer needed. It’s viable for companies like Savvius to ship with a built-in Elastic stack setup.
There’s nothing stopping people centralizing the data either. You can modify the setup on the Insight appliance to send data to a central Elastic setup, and you can copy the Kibana dashboards, and create your own Continue reading
Savvius Insight and the use of Elastic
Last week Savvius announced upgraded versions of its Insight network visibility appliances. These have the usual performance and capacity increases you’d expect, and fill a nice gap in the market.
But the bit that was most interesting to me was the use of an on-board Elastic stack, with pre-built Kibana dashboards for visualizing network data, e.g.:
Historically the only way we could realistically create these sorts of dashboards and systems was using Splunk. I’m a big fan of Splunk, but it has a problem: Cost. Especially if you’re trying to analyze large volumes of network data. You might be able to make Splunk pricing work for application data, but network data volumes are often just too large.
Savvius has previously included a Splunk forwarder, to make it easier to get data from their systems into Splunk. But Elastic has reached the point where Splunk is no longer needed. It’s viable for companies like Savvius to ship with a built-in Elastic stack setup.
There’s nothing stopping people centralizing the data either. You can modify the setup on the Insight appliance to send data to a central Elastic setup, and you can copy the Kibana dashboards, and create your own Continue reading
Building a legacy search engine for a legacy protocol
Building a legacy search engine for a legacy protocol
IPv6 Trends, SixXS Sunset and Project Planning
Native IPv6 availability continues to increase, leading to the sunset of SixXS services. But it looks like we don’t like starting any major IPv6 rollouts around Christmas/New Years, but instead start going into production from April onwards.
SixXS Sunset
In March 2017, the SixXS team announced that they are closing down all services in June 2017:
SixXS will be sunset in H1 2017. All services will be turned down on 2017-06-06, after which the SixXS project will be retired. Users will no longer be able to use their IPv6 tunnels or subnets after this date, and are required to obtain IPv6 connectivity elsewhere, primarily with their Internet service provider.
SixXS has provided a free IPv6 tunnel broker service for years, allowing people to get ‘native’ IPv6 connectivity even when their ISP didn’t offer it. A useful service in the early days of IPv6, when ISPs were dragging the chain.
But this is a Good Thing that it is now closing down. It’s closing down because their mission has been achieved, and people no longer require tunnel broker services. IPv6 is now widely available in many countries, and not just from niche ISPs. Mainstream ISPs such as Comcast in Continue reading
IPv6 Trends, SixXS Sunset and Project Planning
Native IPv6 availability continues to increase, leading to the sunset of SixXS services. But it looks like we don’t like starting any major IPv6 rollouts around Christmas/New Years, but instead start going into production from April onwards.
SixXS Sunset
In March 2017, the SixXS team announced that they are closing down all services in June 2017:
SixXS will be sunset in H1 2017. All services will be turned down on 2017-06-06, after which the SixXS project will be retired. Users will no longer be able to use their IPv6 tunnels or subnets after this date, and are required to obtain IPv6 connectivity elsewhere, primarily with their Internet service provider.
SixXS has provided a free IPv6 tunnel broker service for years, allowing people to get ‘native’ IPv6 connectivity even when their ISP didn’t offer it. A useful service in the early days of IPv6, when ISPs were dragging the chain.
But this is a Good Thing that it is now closing down. It’s closing down because their mission has been achieved, and people no longer require tunnel broker services. IPv6 is now widely available in many countries, and not just from niche ISPs. Mainstream ISPs such as Comcast in Continue reading
Big Bang For The Buck Jump With Volta DGX-1
One of the reasons why Nvidia has been able to quadruple revenues for its Tesla accelerators in recent quarters is that it doesn’t just sell raw accelerators as well as PCI-Express cards, but has become a system vendor in its own right through its DGX-1 server line. The company has also engineered new adapter cards specifically aimed at hyperscalers who want to crank up the performance on their machine learning inference workloads with a cheaper and cooler Volts GPU.
Nvidia does not break out revenues for the DGX-1 line separately from other Tesla and GRID accelerator product sales, but we …
Big Bang For The Buck Jump With Volta DGX-1 was written by Timothy Prickett Morgan at The Next Platform.
Cisco DevNet Preps IT For Programmable Networks
At Interop ITX, Cisco's Susie Wee provided an update on the company's DevNet program.
Worth Reading: The introspective Ouroborus
Introspection can be lethal for a writer. Then again, so can water if you drink too much. If you can moderate your intake, it sustains you. —Arc
The post Worth Reading: The introspective Ouroborus appeared first on rule 11 reader.
Show 340: OpenFlow, Fabrics & Network Virtualization
Todays Weekly Show is a wide-ranging discussion on OpenFlow (and what happened to it), network disaggregation, & network virtualization. Our guest Wes Felter and the Packet Pushers explore the current state of networking and speculate about where the industry is going. The post Show 340: OpenFlow, Fabrics & Network Virtualization appeared first on Packet Pushers.
Pockethernet – A Smartphone-Enabled Cable/Link/IP Tester
I saw an advertisement for Pockethernet a few months ago and it looked pretty impressive; €167.23 (~$179 based on xe.com‘s published exchange rates at the time of writing) for a 200 gram rechargeable device offering 10/100/1000 Ethernet and cable testing features such as:
- A cable tester (wiremapping, TDR fault detection, PoE testing, BER and an analog toner)
- Link analyzer (speed, duplex, VLAN tags, CDP/LLDP, traffic detection)
- IP analyzer (DHCP, DNS, HTTP, ICMP ping)
- Report generation
Over all, Pockethernet sounded like something I needed to look into more closely.

Pockethernet
Pockethernet started off with the assistance of a crowdfunding campaign on Indiegogo, raising $185,000 of their $50,000 target. Unusually for an electronic device, Pockethernet is manufactured in Hungary, which was nice to see. Unboxing the Pockethernet I was surprised (but pleased) to discover that the device is packaged in a soft, zipped carry case.

The box also contains a small User Guide, and inside the case is the Pockethernet tester, an adaptor, a short Ethernet cable and a short USB charging cable. There’s also a strip of blue velcro which will be useful to hold the tester in place if needed.

As it turns out, keeping the Pockethernet Continue reading