AT&T’s 5G Test Sites Cater to Different Types of Users
 Multiple vendors will use the test sites at the same time.
Multiple vendors will use the test sites at the same time.
 Multiple vendors will use the test sites at the same time.
Multiple vendors will use the test sites at the same time.
 Ixia collaborates with CORD Project; IBM releases new developer capabilities on Bluemix.
Ixia collaborates with CORD Project; IBM releases new developer capabilities on Bluemix.
A little over a year ago, Nick Sullivan talked about the beginning of the end for AES-CBC cipher suites, following a plethora of attacks on this cipher mode.
Today we can safely confirm that this prediction is coming true, as for the first time ever the share of AES-CBC cipher suites on Cloudflare’s edge network dropped below that of ChaCha20-Poly1305 suites, and is fast approaching the 10% mark.
Over the course of the last six months, AES-CBC shed more than 33% of its “market” share, dropping from 20% to just 13.4%.
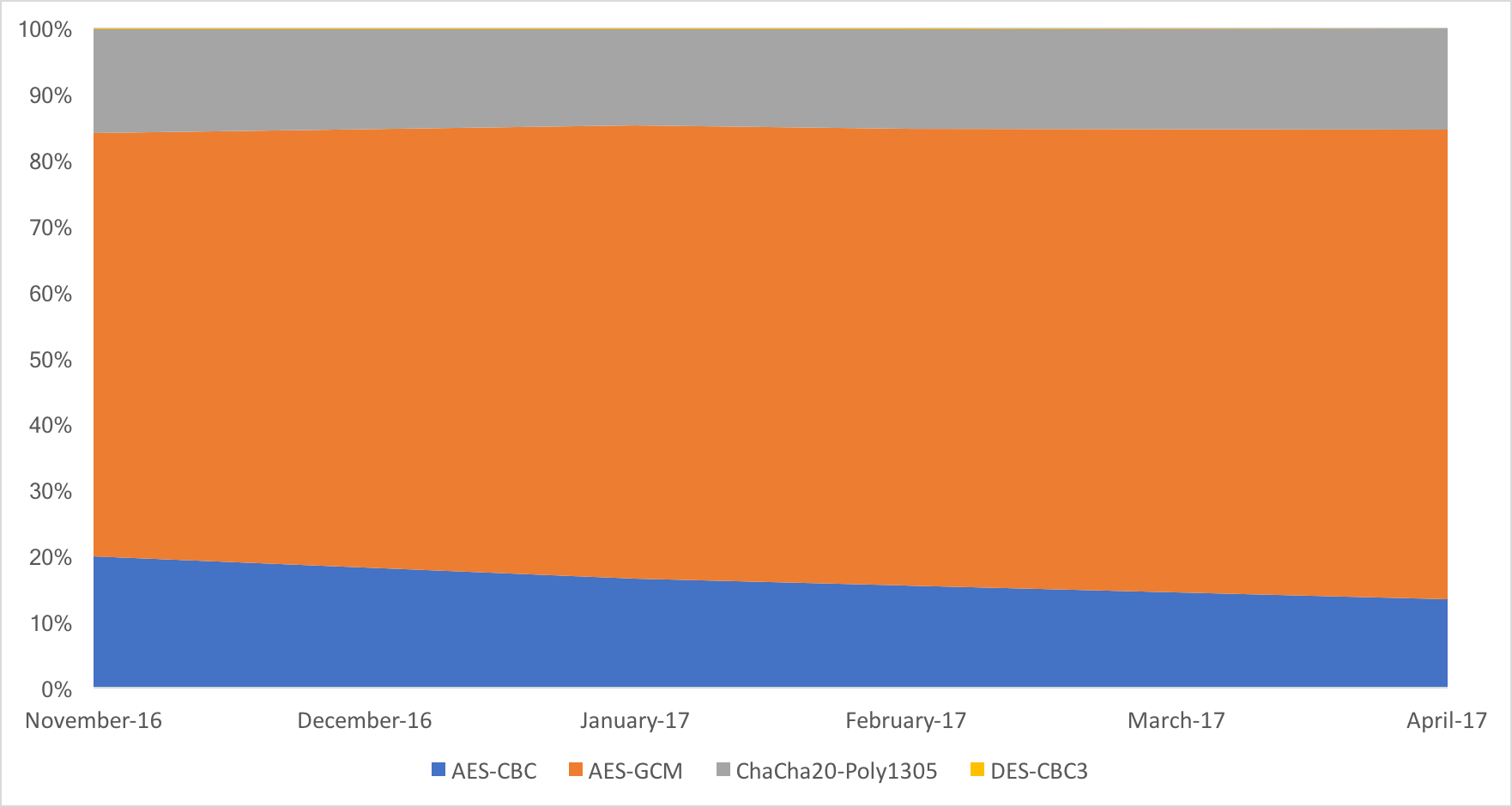
All of that share, went to AES-GCM, that currently encrypts over 71.2% of all connections. ChaCha20-Poly1305 is stable, with 15.3% of all connections opting for that cipher. Surprisingly 3DES is still around, with 0.1% of the connections.
The internal AES-CBC cipher suite breakdown as follows:
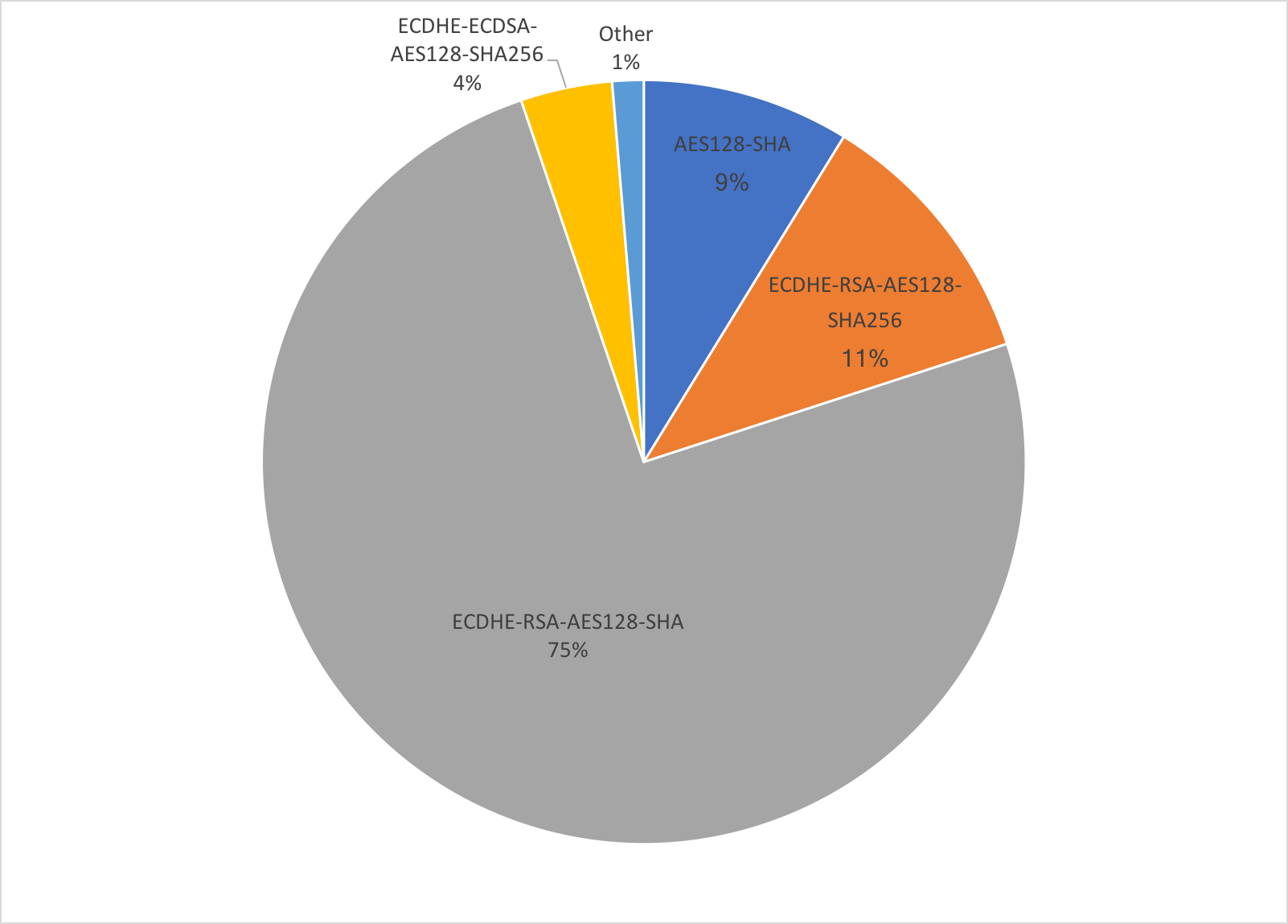
The majority of AES-CBC connections use ECDHE-RSA or RSA key exchange, and not ECDHE-ECDSA, which implies that we mostly deal with older clients.
In other good new, the use of ECDSA surpassed that of RSA at the beginning of the year. Currently more than 60% of all connections use Continue reading
Todays show is an AMA (Ask Me Anything). Greg and Ethan answer listener questions about professional development, staying relevant, and career regrets and successes. The post Show 336: Ethan & Greg Ask Me Anything Part 1 appeared first on Packet Pushers.
Hey, it's HighScalability time: