Keeping The Blue Waters Supercomputer Busy For Three Years
After years of planning and delays after a massive architectural change, the Blue Waters supercomputer at the National Center for Supercomputing Applications at the University of Illinois finally went into production in 2013, giving scientists, engineers and researchers across the country a powerful tool to run and solve the most complex and challenging applications in a broad range of scientific areas, from astrophysics and neuroscience to biophysics and molecular research.
Users of the petascale system have been able to simulate the evolution of space, determine the chemical structure of diseases, model weather, and trace how virus infections propagate via air …
Keeping The Blue Waters Supercomputer Busy For Three Years was written by Jeffrey Burt at The Next Platform.


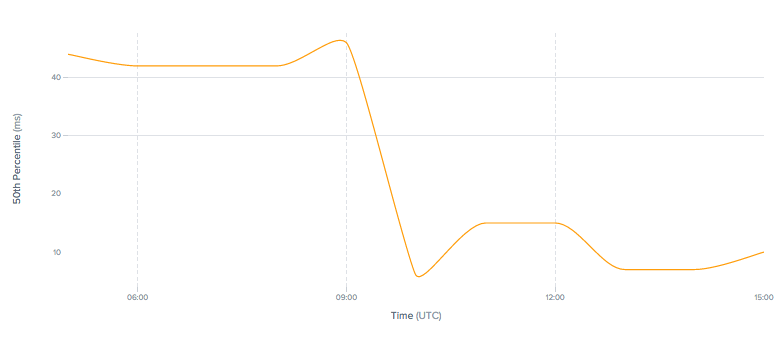 Latency (ms) decreases 6x for UCOM Internet user in Yerevan to Cloudflare. Source:
Latency (ms) decreases 6x for UCOM Internet user in Yerevan to Cloudflare. Source: 
 The new funding brings Innovium’s total financing to $90 million.
The new funding brings Innovium’s total financing to $90 million. It’s based on the Linux Foundation’s Hyperledger open source effort.
It’s based on the Linux Foundation’s Hyperledger open source effort. MVNOs could rent the access layer from the operator but deploy their own VNFs.
MVNOs could rent the access layer from the operator but deploy their own VNFs. It's eliminated the need for Avaya’s Open Network Adapter.
It's eliminated the need for Avaya’s Open Network Adapter.