Postman Wants to Be De Facto Standard for APIs
 Postman is geared towards internal applications and developer workflows.
Postman is geared towards internal applications and developer workflows.
Bringing Standards Development And Open Source Projects Together
The traditional standards-making process is transitioning to a collaborative effort with open source communities.
OpenStack SDN – Distributed Virtual Routing
In this post we’ll explore how DVR is implemented in OpenStack Neutron and what are some of its benefits and shortcomings.
Continue readingNetwork Automation RFP Requirements
After finishing the network automation part of a recent SDN workshop I told the attendees “Vote with your wallet. If your current vendor doesn’t support the network automation functionality you need, move on.”
Not surprisingly, the next question was “And what shall we ask for?” Here’s a short list of ideas, please add yours in comments.
Read more ...FCIP Cheat Sheet Released

Here is the FCIP Cheat Sheet however, There is not much detail and terms about FCIP really, it's a straight forward protocol.
If you found a bug or want new content to be added, please report it!
FCIP Cheat Sheet Released

Here is the FCIP Cheat Sheet however, There is not much detail and terms about FCIP really, it's a straight forward protocol.
All the best and please report in case of any bug.
Authenticated access to Kubernetes pods
When running a micro-services style application in a public cloud, one of the problems to solve is how to provide access to debug information. At Laserlike, we run our application stack on GKE. Most of the stack consists of golang Pods that run an HTTP listener that serves /debug and /metrics handlers.
For metrics scrapping we use prometheus; and grafana for visualization. Our grafana server is nodePort service behind a GCE Load Balancer which uses oauth2 based authentication for access. This still leaves a gap in terms of access to the pod debug information such as /debug/vars or /debug/pprof.
In order to address this gap, we created a simple HTTP proxy for kubernetes services and endpoints. We deploy this proxy behind a oauth2 authenticator which is then exposed via an external load balancer.
The service proxy uses the kubernetes client library in order to consume annotations on the service objects. For example, the following annotation, instructs the service proxy to expose the debug port of the endpoints of the specified service:
metadata:
annotations:
k8s-svc-proxy.local/endpoint-port: "8080"
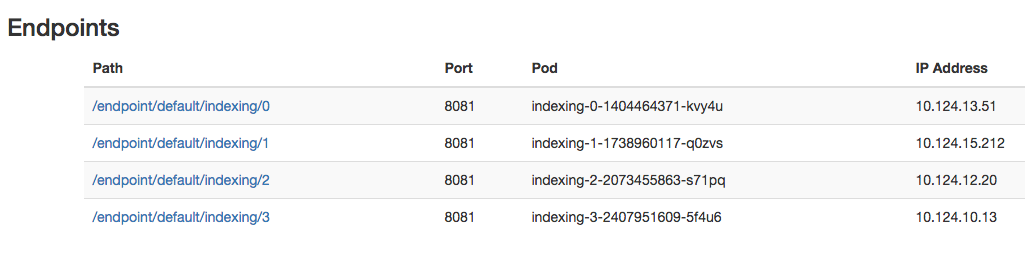
The landing page on the proxy then displays a set of endpoints:
Authenticated access to Kubernetes pods
When running a micro-services style application in a public cloud, one of the problems to solve is how to provide access to debug information. At Laserlike, we run our application stack on GKE. Most of the stack consists of golang Pods that run an HTTP listener that serves /debug and /metrics handlers.
For metrics scrapping we use prometheus; and grafana for visualization. Our grafana server is nodePort service behind a GCE Load Balancer which uses oauth2 based authentication for access. This still leaves a gap in terms of access to the pod debug information such as /debug/vars or /debug/pprof.
In order to address this gap, we created a simple HTTP proxy for kubernetes services and endpoints. We deploy this proxy behind a oauth2 authenticator which is then exposed via an external load balancer.
The service proxy uses the kubernetes client library in order to consume annotations on the service objects. For example, the following annotation, instructs the service proxy to expose the debug port of the endpoints of the specified service:
metadata:
annotations:
k8s-svc-proxy.local/endpoint-port: "8080"
The landing page on the proxy then displays a set of endpoints:

Cloud IT Infrastructure Spending Continues To Climb
IDC's Worldwide Quarterly Cloud IT Infrastructure Forecast nudges total IT budget spent on cloud to 36.9% in 2016.
Raising The Standard For Storage Memory Fabrics
People tend to obsess about processing when it comes to system design, but ultimately an application and its data lives in memory and anything that can improve the capacity, throughput, and latency of memory will make all the processing you throw at it result in useful work rather than wasted clock cycles.
This is why flash has been such a boon for systems. But we can do better, and the Gen-Z consortium announced this week is going to create a new memory fabric standard that it hopes will break down the barriers between main memory and other storage-class memories on …
Raising The Standard For Storage Memory Fabrics was written by Timothy Prickett Morgan at The Next Platform.