Worth Reading: MP-TCP in Hybrid Access Networks
Wouldn’t it be nice if your home router (CPE) could use DSL (or slow-speed fibre) and LTE connection at the same time? Even better: run a single TCP session over both links? The answer to both questions is YES, of course it could do that, if only your service provider would be interested in giving you that option.
We solved similar problems with multilink PPP in the networking antiquity, today you could use a CPE with an MP-TCP proxy combined with a Hybrid Access Gateway in the service provider network. For more details, read the excellent Increasing broadband reach with Hybrid Access Networks article by prof. Olivier Bonaventure and his team.
Worth Reading: MP-TCP in Hybrid Access Networks
Wouldn’t it be nice if your home router (CPE) could use DSL (or slow-speed fibre) and LTE connection at the same time? Even better: run a single TCP session over both links? The answer to both questions is YES, of course it could do that, if only your service provider would be interested in giving you that option.
We solved similar problems with multilink PPP in the networking antiquity, today you could use a CPE with an MP-TCP proxy combined with a Hybrid Access Gateway in the service provider network. For more details, read the excellent Increasing broadband reach with Hybrid Access Networks article by prof. Olivier Bonaventure and his team.
The unreasonable effectiveness of radio
Light and radio transmissions are the same thing, just using different frequencies.
How is it reasonable that I can transmit with a radio using the energy of a low energy light bulb (10 watts), and easily chat with someone 1800km away?
Even if you imagine a perfectly dark world, where the only light bulb is a 10W bulb in Sweden; How is it even possible that this could be seen in Italy? It’s not even a spotlight! It’s only vaguely aimed away from east-west, in favour of up, north, and south.
My little light bulb (radio) could be seen in (approximately) all of Europe. ~750 million people potentially could have received it at the same time. With 10 watts.
“Blink blink” — All of Europe can see my little lightbulb.
And this isn’t some specialized super duper antenna, nor was it set up by an expert, fine tuning everything. I just put up the antenna in a PVC pipe and connected it. We can’t even credit fancy computers digging signals out of the noise. This was not FT8, this was PSK31. I’m sure voice would also have worked.
I also used FT8 with these same 10W to check off Continue reading
Heavy Networking 691: Why OOB Infrastructure Is Critical For IT Ops & Automation With ZPE Systems (Sponsored)
On today’s Heavy Networking podcast, we look at how sponsor ZPE Systems is rethinking Out-Of-Band management for automated, NetOps-driven infrastructure. This includes tasks like device staging, deployments, upgrades, and more. And you don’t just have to take ZPE’s word for it; we also talk to a customer who’s using the products to run a retail business with a lean networking team that supports more than fifty sites.Heavy Networking 691: Why OOB Infrastructure Is Critical For IT Ops & Automation With ZPE Systems (Sponsored)
On today’s Heavy Networking podcast, we look at how sponsor ZPE Systems is rethinking Out-Of-Band management for automated, NetOps-driven infrastructure. This includes tasks like device staging, deployments, upgrades, and more. And you don’t just have to take ZPE’s word for it; we also talk to a customer who’s using the products to run a retail business with a lean networking team that supports more than fifty sites.
The post Heavy Networking 691: Why OOB Infrastructure Is Critical For IT Ops & Automation With ZPE Systems (Sponsored) appeared first on Packet Pushers.
Tia Hopkins on Why the Modern Infrastructure Needs New Resiliency Ideas
In her Network Resilience Boot Camp keynote address, eSentire’s Tia Hopkins discuss why businesses today must re-examine their network resiliency strategies and implement new approaches.Don’t Let the Cybersecurity Trust Mark Become Like Food Labeling
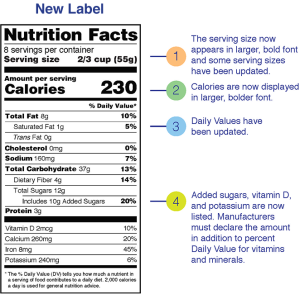
I got several press releases this week talking about the newest program from the US Federal government for cybersecurity labeling. This program is something designed to help consumers understand how secure IoT devices are and the challenges that can be faced trying to keep your network secure from the large number of smart devices that are being implemented today. Consumer Reports has been pushing for something like this for a while and lauded the move with some caution. I’m going to take it a little further. We need to be very careful about this so it doesn’t become as worthless as the nutrition labels mandated by the government.
Absolute Units
Having labels is certainly better than not having them. Knowing how much sugar a sports drink has is way more helpful than when I was growing up and we had to guess. Knowing where to find that info on a package means I’m not having to go find it somewhere on the Internet1. However, all is not sunshine and roses. That’s because of the way that companies choose to fudge their numbers.
Food companies spent a lot of time trying to work the numbers on those nutrition labels for Continue reading
AI Is A Modest – But Important – Slice Of TSMC’s Business
Given the exorbitant demand for compute and networking for running Ai workloads and the dominance of Taiwan Semiconductor Manufacturing Co in making the compute engine chips and providing the complex packaging for them, you would think that the world’s largest foundry would be making money hands over fist in the second quarter. …
The post AI Is A Modest – But Important – Slice Of TSMC’s Business first appeared on The Next Platform.
AI Is A Modest – But Important – Slice Of TSMC’s Business was written by Timothy Prickett Morgan at The Next Platform.
Permitting: The Next Big Enterprise Broadband Challenge
It is ISPs vs. local government with providers waiting for broadband permit approvals that can add costs and delays for enterprise network expansion.Hedge 187: Buffer Bloat with Bjørn T

Buffer bloat causes permanent delay at multiple points along the path between a server and client—but it is hard to measure and resolve. Bjørn Teigen joins Tom and Russ on this episode of the Hedge to discuss the problem, solutions based in routers, and research into how to solve the problem at the host. You can find Bjørn’s recent paper in this area here, and he blogs here.
Migration Coordinator – In Place Migration Modes
In the first part of this blog series, we took a high level view of all the modes that are available with Migration Coordinator, a fully GSS supported tool built into NSX that enables migrating from NSX from vSphere to NSX (NSX-T).
The second blog in this series, will take a closer look at the available options for in-place migrations, along with the pros and cons of each approach.
NSX for vSphere: Fixed Topology
This mode was the very first mode introduced with migration coordinator in the NSX 2.4 release. This mode supports migrating configuration and workloads to NSX, using the same hosts that are running NSX for vSphere. It only needs extra capacity to run the NSX appliances such as the Managers and Edges.
Locating the mode: Marked in red below.

NSX Prep
- Installation: NSX manager and Edges
- Configuration: None
Pros:
- Workload Migration: Built in
- Bridging: Built in
Cons:
- Customization options: None
- Timing workload migration: No control
- Supported topologies: Only 5
Distributed Firewall, Host and Workload
This mode is useful when the requirement is to migrate only Distributed Firewall configuration.
Locating the mode
This mode is under the “Advanced Migration Modes” marked in red below.

NSX Prep:
Optimizing Network Performance using Topology Aware Routing with Calico eBPF and Standard Linux dataplane
In this blog post, we will explore the concept of Kubernetes topology aware routing and how it can enhance network performance for workloads running in Amazon. We will delve into topology aware routing and discuss its benefits in terms of reducing latency and optimizing network traffic flow. In addition, we’ll show you how to minimize the performance impact of overlay networking, using encapsulation only when necessary for communication across availability zones. By doing so, we can enhance network performance by optimizing the utilization of resources based on network topology.
Understanding Topology Aware Routing
Kubernetes clusters are being deployed more often in multi-zone environments. The nodes that make up the cluster are spread across availability zones. If one availability zone is having problems, the nodes in the other availability zones will keep working, and your cluster will continue to provide service for your customers. While this helps to ensure high availability, it also results in increased latency for inter-zone workload communication and can result in inter-zone data transfer costs.
Under normal circumstances, when traffic is directed to a Kubernetes Service, it evenly distributes requests among the pods that support it. Those pods can be spread across nodes in different zones. Topology Continue reading
Ethernet Consortium Shoots For 1 Million Node Clusters That Beat InfiniBand
Here we go again. Some big hyperscalers and cloud builders and their ASIC and switch suppliers are unhappy about Ethernet, and rather than wait for the IEEE to address issues, they are taking matters in their own hands to create what will ultimately become an IEEE standard that moves Ethernet forward in a direction and speed of their choosing. …
The post Ethernet Consortium Shoots For 1 Million Node Clusters That Beat InfiniBand first appeared on The Next Platform.
Ethernet Consortium Shoots For 1 Million Node Clusters That Beat InfiniBand was written by Timothy Prickett Morgan at The Next Platform.