On the ‘Net: Big thinkers leave Cisco
The post On the ‘Net: Big thinkers leave Cisco appeared first on 'net work.
The post On the ‘Net: Big thinkers leave Cisco appeared first on 'net work.
The post On the ‘Net: You keep using that SDN word… appeared first on 'net work.
In networking we use many times different terms to define the same thing. MPLS tunnel label or transport label are just two of those. Not only transport and tunnel labels but also other terms are used to define the same thing which these labels provide. Let me explain first why and where MPLS tunnel label is […]
The post What is MPLS tunnel label and why it is used ? appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
This week, our readers have enjoyed Docker thought leadership on various topics. As we begin a new week, let’s recap our top 5 most-read blog posts for the week of July 17, 2016. Continue reading
 FatPipe Networks and Avaya combined data center SDN and SD-WAN into a single system.
FatPipe Networks and Avaya combined data center SDN and SD-WAN into a single system.
Check-out the new NSX-V Multi-site Options and Cross-VC NSX Design Guide
The goal of this design guide is to outline several NSX solutions available for multi-site data center connectivity before digging deeper into the details of the Cross-VC NSX multi-site solution. Learn how Cross-VC NSX enables logical networking and security across multiple vCenter domains/sites and how it provides enhanced solutions for specific use cases. No longer is logical networking and security constrained to a single vCenter domain. Cross-VC NSX use cases, architecture, functionality, design, and failure/recovery scenarios are discussed in detail.
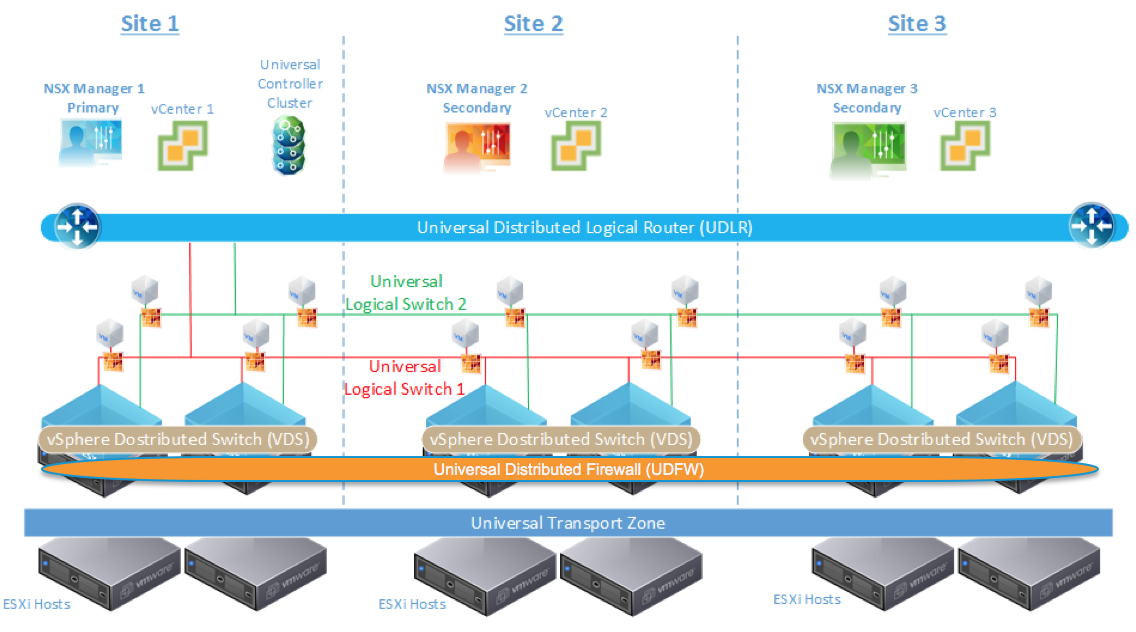
Cross-VC NSX: Logical Networking and Security Across vCenter Domains and Sites
Outlined briefly below are several important use cases that Cross-VC NSX enables in regards to Application Continuity. For additional details on Cross-VC NSX and multi-site data center solutions see the NSX-V Multi-site Options and Cross-VC NSX Design Guide.
Use Case 1: Workload Mobility
Since logical networking and security can span multiple vCenter domains and multiple sites, Cross-VC NSX allows for enhanced workload mobility which can not only span multiple sites but also multiple vCenter domains across Active-Active data centers. Workloads can now move between vCenter domains/sites on demand for tasks such as data center migration, data center Continue reading
The post Worth Reading: Protecting your assets appeared first on 'net work.
 Cloud shift affects IT spending directly and indirectly.
Cloud shift affects IT spending directly and indirectly.
The Packet Pushers talk with Jamie Wilson, senior network specialist at Live Nation UK, to talk about the networking involved in putting on live music festivals. The post Show 298: Listener Stories – Live Nation UK Rocks Networking appeared first on Packet Pushers.