Show 295: Simplifying Network Operations With Cisco Meraki (Sponsored)
On todays sponsored episode we talk with Cisco Meraki about simplifying network operations, explore Merakis full product portfolio, and discover why its not just for SMBs. The post Show 295: Simplifying Network Operations With Cisco Meraki (Sponsored) appeared first on Packet Pushers.
Stuff The Internet Says On Scalability For July 1st, 2016
Hey, it's HighScalability time:
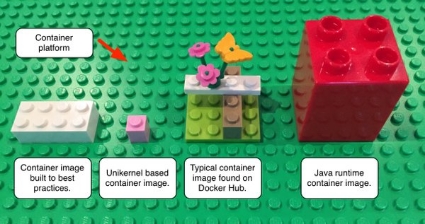
If you can't explain it with Legos then you don't really understand it.
- 700 trillion: more pixels in Google's Satellite Map; 9,000km: length of new undersea internet cable from Oregon to Japan; 60 terabits per second: that undersea internet cable again; 12%: global average connection speed increase; 76%: WeChat users who spend more than 100RMB ($15) per month; 5 liters: per day pay in beer for Pyramid workers; 680: number of rubber bands it takes to explode a watermelon; 1,000: new Amazon services this year; $15 billion: amount Uber has raised; 7 million: # of feather on on each bird in Piper; 5.8 million: square-feet in Tesla Gigafactory; 2x: full-duplex chip could double phone-network data capacity;
- Quotable Quotes:
- @hyc_symas: A shame everyone is implementing on top of HTTP today. Contemporary "protocol design" is a sick joke.
- @f3ew: Wehkamp lost dev and accept environments 5 days before launch. Shit happens. 48 hours to recovery. #devopsdays
- Greg Linden: Ultimately, [serverless computing] this is a good thing, making compute more efficient by allowing more overlapping workloads Continue reading
Worth Reading: Open season
The post Worth Reading: Open season appeared first on 'net work.
Cloud Native Security Paradigm Shift
 Exciting time is ahead for the cloud security industry.
Exciting time is ahead for the cloud security industry.
Zenly + Docker 1.12 + 1M teenagers
Zenly is a mobile app that helps you locate your friends in real time. Recently the Zenly app reached the million registered users mark — and half of them signed up in the last three months.
In the words of Steeve Morin, VP Engineering of Zenly, “Behold, the power of teenagers.”
 The rapid growth in users, traffic and data points generated posed new challenges for the Zenly team.
The rapid growth in users, traffic and data points generated posed new challenges for the Zenly team.
As one of the early users of Docker 1.12, the Zenly team shared their experience during the keynote presentation at DockerCon US 2016 in Seattle.
Here is the story as told by Steeve, JB Daildo and Corentin Kerisit:
The sudden growth of traffic has been both amazing and a real challenge to scale, not on our production stack, but our analytics pipeline as our app started to generate half a billion events a day and counting. Our analytics stack was starting to experience failures due to scaling issues, the costs were rising with how we were running the cluster in the cloud and our 6 person team was challenged in supporting it while also building, scaling and supporting the Zenly app.
What we wanted was to Continue reading