Network Break 425: Microsoft Adds Security Copilot To AI Squadron; Samsung Stung By ChatGPT Leaks
This week's Network Break examines Security Copilot, the latest AI-infused assistant in Microsoft's growing arsenal; discusses optical advancements from Arelion and Infinera that sent 400Gb wavelengths over 1,800 kilometers; examine a news report that claims Tesla workers shared "highly invasive" images recorded by vehicle cameras; plus even more tech news.Network Break 425: Microsoft Adds Security Copilot To AI Squadron; Samsung Stung By ChatGPT Leaks
This week's Network Break examines Security Copilot, the latest AI-infused assistant in Microsoft's growing arsenal; discusses optical advancements from Arelion and Infinera that sent 400Gb wavelengths over 1,800 kilometers; examine a news report that claims Tesla workers shared "highly invasive" images recorded by vehicle cameras; plus even more tech news.
The post Network Break 425: Microsoft Adds Security Copilot To AI Squadron; Samsung Stung By ChatGPT Leaks appeared first on Packet Pushers.
Kubernetes Security And Networking 6: Kubernetes CVEs – Video
This video looks at various Kubernetes vulnerabilities and their severity scores to help you understand how to evaluate CVEs so you can prioritize remediation. It also shows different options and sources of CVEs. You can subscribe to the Packet Pushers’ YouTube channel for more videos as they are published. It’s a diverse a mix of […]
The post Kubernetes Security And Networking 6: Kubernetes CVEs – Video appeared first on Packet Pushers.
VyOS DDoS mitigation
Real-time flow analytics on VyOS describes how to install real-time analytics based on sFlow and the sFlow-RT analytics engine. This article extends the example to show how to automatically mitigate DDoS attacks using flow analytics combined with BGP Remotely Triggered Black Hole (RTBH) / Flowspec.vyos@vyos:~$ add container image sflow/ddos-protectFirst, download the sflow/ddos-protect image.
vyos@vyos:~$ mkdir -m 777 /config/sflow-rtCreate a directory to store persistent container state.
set container network sflowrt prefix 192.168.1.0/24Define an internal network to connect to container. Currently VyOS BGP does not allow direct connections to local addresses (e.g. 127.0.0.1), so we need to put controller on its own network so the router can connect and receive DDoS mitigation BGP RTBH / Flowspec controls.
set container name sflow-rt image sflow/ddos-protect set container name sflow-rt host-name sflow-rt set container name sflow-rt arguments '-Dddos_protect.router=192.168.1.1 -Dddos_protect.enable.flowspec=yes' set container name sflow-rt environment RTMEM value 200M set container name sflow-rt memory 0 set container name sflow-rt volume store source /config/sflow-rt set container name sflow-rt volume store destination /sflow-rt/store set container name sflow-rt network sflowrt address 192.168.1.2
Configure a container to run the image. The Continue reading
Startup Radar: Kumorai Tackles Multi-Cloud Infrastructure Automation
Kumorai is a startup that aims to simplify the deployment and operation of compute, networking, and security infrastructure across public clouds. The company says its SaaS application provides a no-code environment where IT pros can use a visual interface to assemble infrastructure components such as compute, VPCs and vNets, Transit Gateways, and firewalls, and then […]
The post Startup Radar: Kumorai Tackles Multi-Cloud Infrastructure Automation appeared first on Packet Pushers.
How DPUs, IPUs, and CXL Can Improve Data Center Power Efficiency
DPU, IPU, and CXL technologies that offload switching and networking tasks from server CPUs have the potential to significantly improve data center power efficiency.VPP – Monitoring
About this series
Ever since I first saw VPP - the Vector Packet Processor - I have been deeply impressed with its performance and versatility. For those of us who have used Cisco IOS/XR devices, like the classic ASR (aggregation service router), VPP will look and feel quite familiar as many of the approaches are shared between the two.
I’ve been working on the Linux Control Plane [ref], which you can read all about in my series on VPP back in 2021:
- [Part 1]: Punting traffic through TUN/TAP interfaces into Linux
- [Part 2]: Mirroring VPP interface configuration into Linux
- [Part 3]: Automatically creating sub-interfaces in Linux
- [Part 4]: Synchronize link state, MTU and addresses to Linux
- [Part 5]: Netlink Listener, synchronizing state from Linux to VPP
- [Part 6]: Observability with LibreNMS and VPP SNMP Agent
- [Part 7]: Productionizing and reference Supermicro fleet at IPng
With this, I can make a regular server running Linux use VPP as kind of a software ASIC for super fast forwarding, filtering, NAT, and so on, while keeping control of the interface state (links, addresses and routes) itself. With Continue reading
Notes from IETF116
The IETF had its 116th meeting in Yokohama, Japan in the last week of March. Here’s some notes I made from some of the working group sessions I attended that I found to be of interest.Cloud Notes: Azure Application Gateway
https://codingpackets.com/blog/cloud-notes-azure-application-gateway
Heavy Networking 673: Multicast DNS Gone Wild On Your WLAN
You know all those Apple and other IoT devices connected to your wireless network? Lots of them run apps that discover services on your network via multicast DNS (mDNS). All of that mDNS traffic can have a significant impact on your WLAN’s performance. On today's Heavy Networking we talk with guest Bryan Ward who has actually measured the impact of mDNS on a production wireless network to see what would happen if he let mDNS traffic run wild.Heavy Networking 673: Multicast DNS Gone Wild On Your WLAN
You know all those Apple and other IoT devices connected to your wireless network? Lots of them run apps that discover services on your network via multicast DNS (mDNS). All of that mDNS traffic can have a significant impact on your WLAN’s performance. On today's Heavy Networking we talk with guest Bryan Ward who has actually measured the impact of mDNS on a production wireless network to see what would happen if he let mDNS traffic run wild.
The post Heavy Networking 673: Multicast DNS Gone Wild On Your WLAN appeared first on Packet Pushers.
Technology Short Take 167
Welcome to Technology Short Take #167! This Technology Short Take is a tad shorter than the typical one; I’ve been busy recently and my intake volume of content has gone down, thus resulting in fewer links to share with all of you! I opted to go ahead and publish a shorter Technology Short Take instead of making everyone wait around for a longer one. In any case, here’s hoping that I’ve included something useful for you!
Networking
- Jeff McLaughlin discusses what he calls the “war on expertise.”
- Ivan Pepelnjak has some very useful and very applicable information on VRF-aware DHCP relaying.
- Michał Iwańczuk shares some information on EVPN inline mode in NSX-T.
- Harikrishnan T wraps up a 4-part series on stateful active-active gateways in NSX. Links to the previous three posts are embedded in the article.
Servers/Hardware
- Manoj Kumar provides a beginner’s guide to Trusted Platform Module (TPM).
Security
- GitHub recently had to change their RSA SSH host key; be sure to check out the details.
- Google warns users about exploitable flaws in popular Android phones.
- Rory McCune examines some container security fundamentals that arise from the fact that “containers are just processes.”
Cloud Computing/Cloud Management
- Laurent Continue reading
Turning WiFi into a Thick Yellow Cable
The “beauty” (from an attacker perspective) of the original shared-media Ethernet was the ability to see all traffic sent to other hosts. While it’s trivial to steal someone else’s IPv4 address, the ability to see their traffic allowed you to hijack their TCP sessions without the victim being any wiser (apart from the obvious session timeout). Really smart attackers could go a step further, insert themselves into the forwarding path, and inject extra payload into unencrypted sessions.
A recently-discovered WiFi vulnerability brought us back to that wonderful world.
Turning WiFi into a Thick Yellow Cable
The “beauty” (from an attacker perspective) of the original shared-media Ethernet was the ability to see all traffic sent to other hosts. While it’s trivial to steal someone else’s IPv4 address, the ability to see their traffic allowed you to hijack their TCP sessions without the victim being any wiser (apart from the obvious session timeout). Really smart attackers could go a step further, insert themselves into the forwarding path, and inject extra payload into unencrypted sessions.
A recently-discovered WiFi vulnerability brought us back to that wonderful world.
The Evolving Role of VPN Security in the Era of Hybrid Work
Can organizations evolve and “rebrand” the VPN to emphasize the continued importance of this network security tool?Project Calico wants to hear from you! The 2023 Calico Open Source Adoption Survey
Project Calico is made possible thanks to you—thank you for your ongoing support of Project Calico, and for being an essential part of our growing open-source community. To improve Calico, we want to hear from you.
That’s why we’ve created the 2023 Calico Open Source Adoption Survey, a 16-question survey designed specifically to help us gather your feedback and insights.
Why take this survey?
Not only will this be a chance to share extensive feedback, your input will actually help us prioritize future development efforts and ensure that we are addressing the most pressing needs of the community. We want to make sure that Project Calico continues to be the best possible solution for networking and security in Kubernetes and container environments.
We know that your time is valuable, but we believe that your feedback is essential to our success. We hope that you will take a few moments to complete the survey and share your thoughts with us.
Thank you again for your continued support, and we look forward to hearing from you soon.
The post Project Calico wants to hear from you! The 2023 Calico Open Source Adoption Survey appeared first on Tigera.
Dictionary: Gish Gallop
 Defeating misinformation and misidrection in sales and vendor meetings
Defeating misinformation and misidrection in sales and vendor meetings
Introducing Calico Runtime Threat Defense—The most extensive security coverage for containers and Kubernetes
Containerized applications are complex, which is why an effective container security strategy is difficult to design and execute. As digitalization continues to push applications and services to the cloud, bad actors’ attack techniques have also become more sophisticated, which further challenges container security solutions available on the market.
Despite the discussion around agent vs agentless in the cloud security landscape and which type of solution is better, the most valuable solution is one that provides a wide breadth of coverage. Calico is unique as it is already installed as part of the underlying platform and provides the dataplane for a Kubernetes cluster. When Calico Cloud or Calico Enterprise is deployed, security and observability capabilities can be enabled on top of these core components. We provide a simple plug-and-play active security solution that focuses on securing workloads and the Kubernetes platform with the least amount of complexity and configuration.
Runtime attack vectors
Cloud-native applications are susceptible to many attack vectors. We have broken them down to eight, as seen in the following illustration:
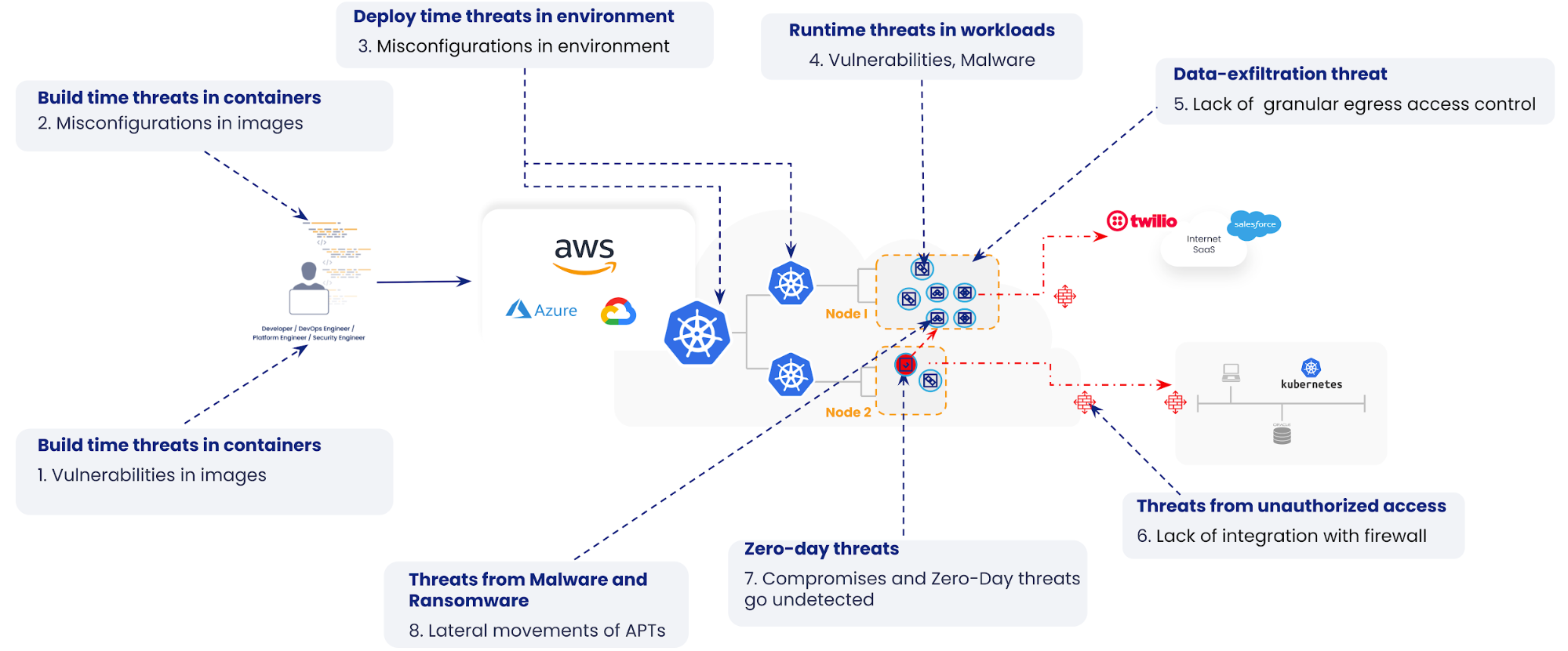
In previous blogs, we have explained how the use of vulnerability management, zero-trust workload security, and microsegmentation can help reduce the Continue reading

