Network Virtualization and SDN Have to Go Beyond the Data Center — Learn Why With Avaya
 Avaya and SDxCentral dive into the recently released Network Virtualization Report on December 15th with a live webinar. Save your spot today!
Avaya and SDxCentral dive into the recently released Network Virtualization Report on December 15th with a live webinar. Save your spot today!
Stuff The Internet Says On Scalability For November 20th, 2015
Hey, it's HighScalability time:
- $24 billion: amount telcos make selling data about you; $500,000: cost of iOS zero day exploit; 50%: a year's growth of internet users in India; 72: number of cores in Intel's new chip; 30,000: Docker containers started on 1,000 nodes; 1962: when the first Cathode Ray Tube entered interplanetary space; 2x: cognitive improvement with better indoor air quality; 1 million: Kubernetes request per second;
- Quotable Quotes:
- Zuckerberg: One of our goals for the next five to 10 years is to basically get better than human level at all of the primary human senses: vision, hearing, language, general cognition.
- Sawyer Hollenshead: I decided to do what any sane programmer would do: Devise an overly complex solution on AWS for a seemingly simple problem.
- Marvin Minsky: Big companies and bad ideas don't mix very well.
- @mathiasverraes: Events != hooks. Hooks allow you to reach into a procedure, change its state. Events communicate state change. Hooks couple, events decouple
- @neil_conway: Lamport, trolling distributed systems engineers since 1998. Continue reading
Zürich, Switzerland: CloudFlare’s 69th data center

Grüetzi Zürich, our 5th point of presence (PoP) to be announced this week, and 69th globally! Located at the northern tip of Lake Zürich in Switzerland, the city of Zürich, often referred to as "Downtown Switzerland," is the largest city in the country. Following this expansion, traffic from Switzerland's seven million internet users to sites and apps using CloudFlare is now mere milliseconds away. Although best known to some for its chocolate and banks, Switzerland is home to many of the most significant developments prefacing the modern internet.
Vague but interesting
It was in 1989 that Tim Berners-Lee, a British scientist at CERN, the large particle physics laboratory near Geneva, Switzerland, invented the World Wide Web (WWW). Tim laid out his vision to meet the demand for automatic information-sharing between scientists in universities and institutes around the world in a memo titled, "Information Management: a Proposal". Amusingly, his initial proposal wasn't immediately accepted. In fact, his boss at the time noted that the proposal was, "vague but exciting" on the cover page.
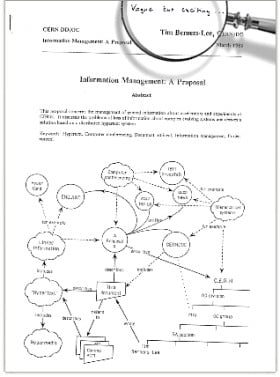
The first website at CERN—and in the world—was dedicated to the Continue reading
Show 264: Design & Build 8: NSX Deployment
NSX has become a popular option for data center network virtualization. If you do choose to go with NSX, what should you be thinking about? Our focus for today's show is what to consider when designing an NSX implementation, why planning is so essential, and what will change operationally once NSX is in production.
The post Show 264: Design & Build 8: NSX Deployment appeared first on Packet Pushers.
Video: Cumulus Linux Architecture
Do you want to know more about Cumulus Linux after learning what data center architectures it supports, what base technologies it uses, and how you can use it to simplify network configurations? It’s time to explore Cumulus Linux architecture (part 5 of the presentation Dinesh Dutt had during the Data Center Fabrics webinar).
Risky Business #390 — Crypto derpery abounds in wake of Paris attacks
In this week's feature interview we're checking in with FireEye's Jonathan Wrolstad. He's a threat intelligence guy at FireEye and they've just published a really interesting report about what a threat group is doing in terms of target recon. They're using marketing company tricks to recon all sorts of high value targets. It's very interesting stuff, and it's likely tied to the Russian state.
Install and configure GNS3 on Arch Linux
Most of the GNS3 (Linux) installation guides focus on the Debian-based or RedHat-based Linux distributions. What about us Archers?Google Cloud Goes Greene
 Diane Greene will not only run Google Cloud, but also Google's applications businesses.
Diane Greene will not only run Google Cloud, but also Google's applications businesses.
WiFi Calling Might Be a First NFV Use Case for Comcast
 Comcast could use NFV to bring in mobile revenues.
Comcast could use NFV to bring in mobile revenues.
vArmour Has a Plan for Multicloud Security
 A 5-step program for securing that pesky hybrid cloud.
A 5-step program for securing that pesky hybrid cloud.
Cloud Builders: Building Networks for Third Era Cloud Environments
It’s no secret that network architecture is evolving to address the new needs and requirements of the Third Era of IT. This is happening for a reason. There is a trifecta of events affecting the industry: new requirements, new application architectures and new consumption models.
What all this reveals is that a new IT landscape has arrived – the Third Platform, where applications and service offerings define IT rather than the opposite.
The need of businesses to drive new application development, change, and deployment is changing the consumption models for IT so radically that for the first time the industry is prioritizing consumption of an entire service over individual infrastructure silos. It’s quickly becoming apparent that IT will increasingly be consumed as service offerings whether delivered through private or public cloud providers (SaaS, IaaS and PaaS).
The Changing Nature of the Private Cloud
Cloud enables rapid scaling; both up and down, of compute and storage capacity and facilitates agility for the introduction of new services and applications as well as resource alignment to the changing needs of the business. Public cloud has been the most prevalent adoption model to date, however we see a growing trend where organizations are Continue reading
Special Report on Network Virtualization is Live!
 Download your free copy today!
Download your free copy today!
Facebook Developing 100 Gigabit Ethernet Switch
Engineers at social networking giant say they're working on a faster version of their Wedge data center switch.CloudFlare launches India data centers in Mumbai, Chennai and New Delhi

India is home to 400 million Internet users, second only to China, and will add more new users this year than any other country in the world. CloudFlare protects and accelerates 4 million websites, mobile apps and APIs, and is trusted by over 10,000 new customers each day. Combine these forces, and we are positioned to connect hundreds of millions of Indian users with the millions of internet applications they use each day.
Today, we accelerate this momentum with the announcement of three new points of presence (PoPs) in Mumbai, Chennai and New Delhi. These new sites represent the 66th, 67th and 68th data centers respectively across our global network.
We’ve come a long way
The beginnings of the “internet” in India as we know it started in 1986 when the country launched ERNET (the Education and Research Network). Six years later, a 64 Kbps digital leased line was commissioned from the National Centre for Software Technology in Mumbai to UUNet in Virginia to connect India with the rest of the internet. By comparison, a single port on our router in each of Mumbai, Chennai and New Delhi has nearly 160,000 times the capacity today.
The pace of progress has Continue reading

