Worth Reading: Revisiting Internet Governance

The post Worth Reading: Revisiting Internet Governance appeared first on 'net work.
Control Plane Protection in Cisco IOS
How does Internet work - We know what is networking
CoPP – Control Plane Protection or better Control Plain Policing is the only option to make some sort of flood protection or QoS for traffic going to control plane. In the router normal operation the most important traffic is control plain traffic. Control plane traffic is traffic originated on router itself by protocol services running on it and destined to other router device on the network. In order to run properly, routers need to speak with each other. They speak with each other by rules defined in protocols and protocols are run in shape of router services. Examples for this
TeliaSonera Likes Its NFV Session Border Controller on COTS
 Metaswitch chalks up another service provider for the Perimeta SBC.
Metaswitch chalks up another service provider for the Perimeta SBC.
SSL Certificate signed by own CA
There are a lot of “how-to” on the Internet explaining the setup procedure. This is mainly a copy / paste example for those in a hurry :)
How to setup your own CA
SDN Myths Revisited
![]()
I had a great time at TECHunplugged a couple of weeks ago. I learned a lot about emerging topics in technology, including a great talk about the death of disk from Chris Mellor of the Register. All in all, it was a great event. Even with a presentation from the token (ring) networking guy:
I had a great time talking about SDN myths and truths and doing some investigation behind the scenes. What we see and hear about SDN is only a small part of what people think about it.
SDN Myths
Myths emerge because people can’t understand or won’t understand something. Myths perpetuate because they are larger than life. Lumberjacks and blue oxen clearing forests. Cowboys roping tornadoes. That kind of thing. With technology, those myths exist because people don’t want to believe reality.
SDN is going to take the jobs of people that can’t face the reality that technology changes rapidly. There is a segment of the tech worker populace that just moves from new job to new job doing the same old things. We leave technology behind all the time without a care in the world. But we worry when people can’t work on that technology.
Network Troubleshooting: Device Cleanup
In this video, Tony Fortunato explains how removing unnecessary protocols and services from desktops and other devices can make the job of network troubleshooting much easier.IT Monitoring & The Five Stages of Grief
Organizations often exhibit a series of behaviors when they implement IT monitoring systems that makes life difficult for IT pros doing the monitoring.Get ipSpace.net Subscription while Attending the Rome SDN/NFV Event
Reiss Romoli, the fantastic organizers of my SDN/NFV event in Rome, Italy in late October are offering you a free personal ipSpace.net subscription – a saving of $299 or approximately EUR 270.
All you have to do to qualify is (A) download and fill in the registration form, (B) send it to Reiss Romoli and (C) pay before attending the webinar.
Yeah, I know the PDF form says “fax it back” – everyone has to use the tools that work best in their environment.
Hope we'll meet in warm and sunny Rome in a few weeks!
Cisco Strikes a Blow Against Ransomware
 A $60M Angler Exploit Kit operation gets cut in half.
A $60M Angler Exploit Kit operation gets cut in half.
Arista Takes a Macro Approach to Physical & Virtual Network Security
 It's like microsegmentation, only more 'macro.'
It's like microsegmentation, only more 'macro.'
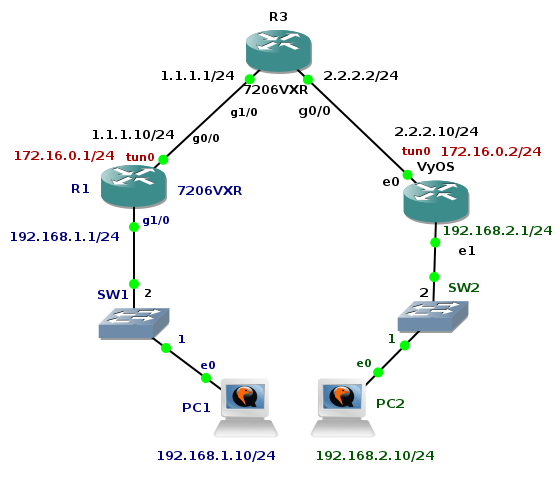
GRE over IPSec Tunnel Between Cisco and VyOS
The previous tutorial shown GRE tunnel configuration between Cisco router and Linux Core. The big advantage of GRE protocol is that itGRE over IPSec Tunnel Between Cisco and VyOS
The previous tutorial shown GRE tunnel configuration between Cisco router and Linux Core. The big advantage of GRE protocol is that it encapsulates L3 and higher protocols inside the GRE tunnel so routing updates and other multicast traffic can be successfully transferred over the tunnel. The main drawback of GRE protocol is the lack of built-in security. Data are transferred in plain-text over the tunnel and peers are not authenticated (no confidentiality). Tunneled traffic can be changed by attacker (no integrity checking of IP packets). For this reason GRE tunnel is very often used in conjunction with IPSec. Typically, GRE tunnel is encapsulated inside the IPSec tunnel and this model is called GRE over IPSec.
The tutorial shows configuration of OSPF routing protocol, GRE and IPSec tunnel on Cisco 7206 VXR router and appliance running VyOS network OS. Devices are running inside GNS3 lab an they are emulated by Dynamips (Cisco) and Qemu (VyOS).
Picture 1 - Topology
Note: VyOS installation is described here. You can easily build your own VyOS Qemu appliance using the Expect and Bash script shared in the article.
1. R3 Configuration
R3(config)# interface gigabitEthernet 1/0
R3(config-if)# ip address 1.1.1.1 255.255.255.0
R3(config-if)# no shutdown
R3(config-if)# interface gigabitEthernet 0/0
R3(config-if)# ip Continue reading
Juniper NXTWork 2015
Coming this November, Juniper has finally jumped into the Customer Summit bandwagon. This is something that has been asked for for many years now, a way for Juniper customers and advocates to get together and talk Juniper. This event will allow you to connect with your peers in the industry, meet current and potential […]
The post Juniper NXTWork 2015 appeared first on Fryguy's Blog.
Manchester, UK: CloudFlare’s 63rd data center

Our new point of presence in Manchester, UK brings the CloudFlare network to 63 points of presence across 33 countries. In other words, the sun never sets across the CloudFlare network. Our data center in Manchester also admits the United Kingdom into a small club of countries with more than one CloudFlare data center, including the US, China, Japan, Australia, Germany, and France.
As of yesterday, traffic from the majority of Internet users in Northern England is now mere milliseconds away. More importantly, our Manchester and London data centers allow for redundancy and content localization within the UK for all of our customers.
In homage
The city of Manchester has made more than its fair share of technical contributions over the years. It is the city where Rolls met Royce (their first car drove off the line of their Manchester factory in 1904), and is also home to the first modern computer. The computer, nicknamed "Baby", was built at The University of Manchester using technology developed for WWII communications equipment, and ran the world's first stored program at 11am on Monday 21st June, 1948.

It is fitting, then, that in the last three years there has been a concerted effort Continue reading