CloudFlare + WHMCS: Faster Websites For Your Customers
We’re at the cPanel Conference in Denver this week, so feel free to drop by our booth and say hello. It’s a great opportunity to connect with our partners and better understand their needs. We’re always trying to streamline our partners’ user experience, and we thought it would be a fitting time to walk through our recently updated WHMCS integration.
CloudFlare’s WHMCS 6.0 plugin lets hosting providers and registrars extend all the benefits of CloudFlare directly to their customers. You can offer your entire user base a global CDN with 62 points of presence, automatic web content optimization, basic DDoS protection, reputation-based threat protection, and much more with virtually no extra work.
These benefits are seamlessly integrated into your WHMCS client. All your customers need to do is click a button, and a new CloudFlare account will be configured for them.
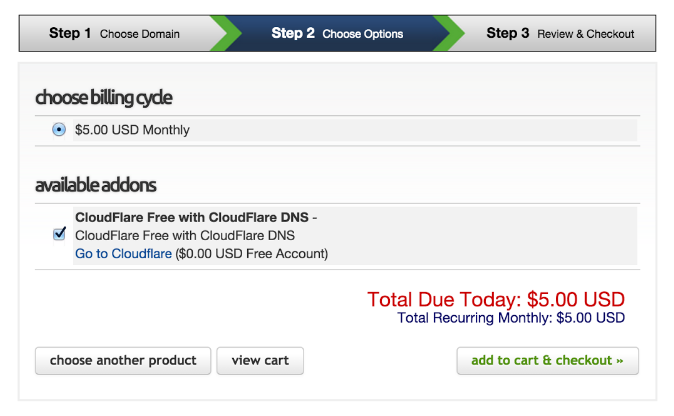
While signing up for an account on www.cloudflare.com only takes a few minutes, users do need to point the relevant DNS records to CloudFlare’s nameservers. Offerring a one-click solution via our WHMCS integration is a great opportunity for hosting providers and registrars to streamline the process for their customers.
Universal SSL with WHMCS
CloudFlare’s Universal Continue reading
Maybe with less hate
I wanted to point out President's rather great tweet in response to Ahmed Mohamed's totally-not-a-bomb:Cool clock, Ahmed. Want to bring it to the White House? We should inspire more kids like you to like science. It's what makes America great.— President Obama (@POTUS) September 16, 2015The reason this tweet is great is that it points out the great stupidity of the teachers/police, but by bringing Ahmed up rather than bringing them down. It brings all America up. Though the school/police did something wrong, the President isn't attacking them with hate.
The teachers/police were almost certainly racist, of course, but they don't see themselves that way. Attacking them with hate is therefore unlikely to fix anything. It's not going to change their behavior, because they think they did nothing wrong -- they'll just get more defensive. It's not going change the behavior of others, because everyone (often wrongly) believes they are part of the solution and not part of the problem.
Issues like Ahmed's deserve attention, but remember that reasonable people will disagree. Some believe the bigger issue is the racism. Other's believe that the bigger issue is the post 9/11 culture of ignorance and suspicion, where Continue reading
Former Cisco President Lloyd Boards Hyperloop as CEO
 Rob Lloyd seems to have landed on his feet after leaving Cisco.
Rob Lloyd seems to have landed on his feet after leaving Cisco.
Killer SDN Applications: A view in 2015
Whilst on the DLR in London earlier this year (2015) a set of thoughts came to light whilst pondering centralised decision making for part of a network. It’s not uncommon to hear “Product X is a great platform that just needs the killer app”. Why the DLR? No drivers, swipe-in-swipe-out ticketing and a well defined service. A train still takes you from A to B, but the whole service around it has completely changed to keep up with the requirements. Thought provoking stuff.
TL;DR
Many people talk about killer apps and are seemingly waiting for them to pop in to existence. This post goes someway to come to terms with the lack of emerging killer apps and why we’re one paradigm shift away from seeing it happen.
The Rub
I’ve said this a million times, but traditional networking skill sets view the network as a CLI that is linked to features. Separation of the monolith seems mad! Why separate something out when what we have today works? Well, that’s the key issue.
The IPEngineer Laws of Humans
Networking as we mostly know it today:
a) Is massively reliant on error prone humans
b) Humans are an expensive resource to have Continue reading
Docker Global Hack Day #3 Starts Today!
Docker Global Hack Day #3 starts today at 4 pm PDT with an awesome line-up of speakers for our kick-off event! Sign up for the livestream or join your local meetup group! Many local groups are organizing meetups to watch the livestream … ContinuedGet Docker on Demand for Amazon Web Services
Docker Trusted Registry, Docker Engine and Business Day Support available for a free 30 day trial to build, ship and run distributed applications in Amazon Web Services. Amazon Web Services (AWS) is a popular … ContinuedCitrix White Paper: Integrate SDN & ADNs
 The ultimate guide for ADN masters. Read the Citrix white paper for the latest on ADN integration models, use cases and best practices!
The ultimate guide for ADN masters. Read the Citrix white paper for the latest on ADN integration models, use cases and best practices!
5 Lessons and 8 Industry Changes Over 5 Years as Etsy CTO

Endings are often a time for reflection and from reflection often comes wisdom. That is the case for Kellan Elliott-McCrea, who recently announced he was leaving his job after five successful years as the CTO of Etsy. Kellan wrote a rather remarkable going away post: Five years, building a culture, and handing it off, brimming with both insight and thoughtful commentary.
This post is just a short gloss of the major points. He goes into more depth on each point, so please read his post.
The Five Lessons:
- Nothing we “know” about software development should be assumed to be true.
- Technology is the product of the culture that builds it.
- Software development should be thought of as a cycle of continual learning and improvement rather a progression from start to finish, or a search for correctness.
- You build a culture of learning by optimizing globally not locally.
- If you want to build for the long term, the only guarantee is change.
The Eight Industry Changes:
- Five years ago, continuous deployment was still a heretical idea.
- Five years ago, it was crazy to discuss that monitoring, testing, debugging, QA, staged releases, game days, user research, and prototypes Continue reading
vCPE Is a Hot NFV Use Case for Masergy
 Virtual customer premises equipment is one of several use cases for NFV, but the topic gets top billing at an NFV industry conference.
Virtual customer premises equipment is one of several use cases for NFV, but the topic gets top billing at an NFV industry conference.
Featured Use Case: IMTC & ONF Release First UC SDN Use Case & Open Standard NBI to Automate QoE
 IMTC and ONF issue the first UC SDN use case and standardized NBI specification, which enables applications to communicate performance needs to better optimize the underlying network using SDN.
IMTC and ONF issue the first UC SDN use case and standardized NBI specification, which enables applications to communicate performance needs to better optimize the underlying network using SDN.
How the Internet Really Works


Way back in April of 2014, I started a series over on Packet Pushers called “How the Internet Really Works.” This is a long series, but well worth reading if you want to try and get a handle around how the different companies and organizations that make up the ecosystem of the ‘net actually do what they do.
Overview
DNS Lookups
The Business Side of DNS (1)
The Business Side of DNS (2)
Reverse Lookups and Whois
DNS Security
Provider Peering Types
Provider Peering and Revenue Streams (1)
Provider Peering and Revenue Streams (2)
Standards Bodies
IETF Organizational Structure
The IETF Draft Process
Reality at the Mic (Inside the IETF, Part 1)
Reality at the Mic (Inside the IETF, Part 2)
Reality at the Mic (Inside the IETF, Part 3)
Internet Exchange Points
That Big Number Database in the Sky (IANA)
NOG World (Network Operator Groups)
The Internet Society
The slides that go with this set of posts are available on slideshare, as well. This set is in Ericsson format, but I have older sets in “vendor neutral” formatting, and even cisco formatting (imagine that!).
The post How the Internet Continue reading
Worth Reading: How we ended up with microservices


The post Worth Reading: How we ended up with microservices appeared first on 'net work.
Datanauts 009 – The Silo Series: Designing A vSwitch
Today, networks extend into hypervisors via vSwitches. Network engineers ignore vSwitches at their peril. At the same time, virtualization engineers ignore the physical network at theirs. Let’s work together to configure a vSwitch as good as it can be.
The post Datanauts 009 – The Silo Series: Designing A vSwitch appeared first on Packet Pushers.

