IDG Contributor Network: Mainframes and mobile: What powers your mobile banking?
As someone who lives and breathes mainframes, I often forget that people who aren't part of this world don't always believe some of the truths that I believe to be self-evident. One common way that I raise eyebrows is when I tell my fellow technologists that mainframes are perfect for supporting mobile applications. In fact, it is almost guaranteed to invoke skepticism. So let me just say it again: mainframes and mobile are a perfect combination.At first glance, it's easy to see why this might be somewhat incongruous. Mainframes have been around for more than half a century, and for most of their history the idea of small, portable devices was the stuff of science fiction. When laptops, smartphones and tablets (and, more recently, intelligent wearables) came on the scene they were truly revolutionary because they fulfilled the long-standing promise of truly portable computing. So what role could "Big Iron" possibly play in a world of increasingly smaller devices?To read this article in full or to leave a comment, please click here
 By now, we all know the benefits of SDN, but what about its challenges? New research lays out the expectations of IT professionals.
By now, we all know the benefits of SDN, but what about its challenges? New research lays out the expectations of IT professionals.

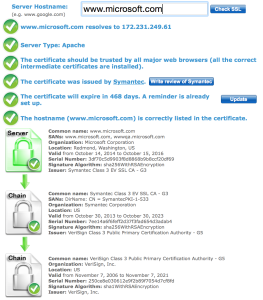
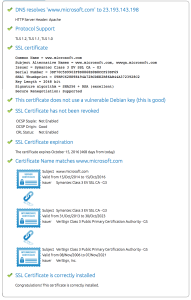
 Steel ORCA has eventual plans for Avaya's Fx architecture for SDN.
Steel ORCA has eventual plans for Avaya's Fx architecture for SDN.