Senate delays vote on NSA phone records dragnet
A controversial program allowing the U.S. National Security Agency to collect millions of domestic telephone records expired Sunday night after the Senate failed to vote on a bill to extend the authority for the surveillance.The Senate, meeting on Sunday as provisions of the counterterrorism Patriot Act were hours from expiring, voted on a so-called cloture to limit debate and move toward a vote on the USA Freedom Act, a bill that would rein in the NSA’s bulk collection of U.S. telephone records while allowing the agency to collect records in a more targeted manner.The 77-17 vote for cloture on the USA Freedom Act sets up a final vote on the bill, but the Senate isn’t likely to take action before Tuesday.To read this article in full or to leave a comment, please click here
 Jennifer Rexford and Nick McKeown have kicked off what could be the next generation of SDN.
Jennifer Rexford and Nick McKeown have kicked off what could be the next generation of SDN. Very very happy to pass on to you that VIRL supports packet capturing now!!! Tossed together a quick ~12minute youtube.
Very very happy to pass on to you that VIRL supports packet capturing now!!! Tossed together a quick ~12minute youtube.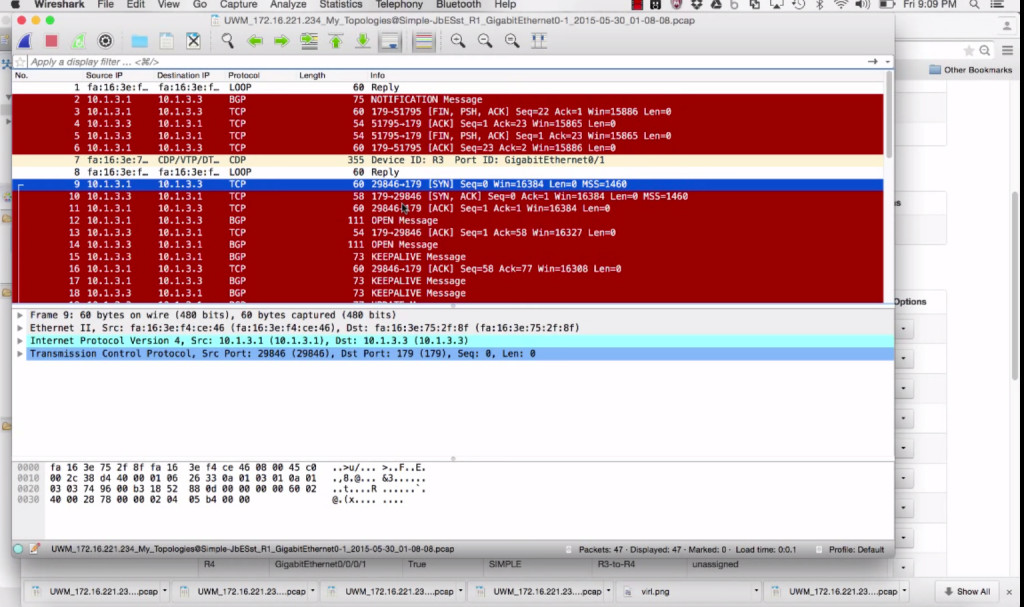
 Executive moves at Cisco and Ruckus, new training at Juniper, and a DevOps-minded monitoring startup.
Executive moves at Cisco and Ruckus, new training at Juniper, and a DevOps-minded monitoring startup. Learn how to virtualize performance monitoring in NFV environments, virtualize the customer edge, and create dynamic interconnects. Sign up now for the Accedian DemoFriday!
Learn how to virtualize performance monitoring in NFV environments, virtualize the customer edge, and create dynamic interconnects. Sign up now for the Accedian DemoFriday!