Making Your Wireless Guest Friendly

During the recent Virtualization Field Day 4, I was located at a vendor building and jumped on their guest wireless network. There are a few things that I need to get accomplished before the magic happens at a Tech Field Day event, so I’m always on the guest network quickly. It’s only after I take care of a few website related items that I settle down into a routine of catching up on email and other items. That’s when I discovered that this particular location blocked access to IMAP on their guest network. My mail client stalled out when trying to fetch messages and clear my outbox. I could log into Gmail just fine and send and receive while I was on-site. But my workflow depends on my mail client. That made me think about guest WiFi and usability.
Be Our (Limited) Guest
Guest WiFi is a huge deal for visitors to an office. We live in a society where ever-present connectivity is necessary. Email notifications, social media updates, and the capability to look up necessary information instantly have pervaded our lives. For those of us fortunate enough to still have an unlimited cellular data plan, our connectivity craving Continue reading
DDoS Attacks in the Wake of French Anti-terror Demonstrations
On January 15th, France’s chief information systems defense official, Adm. Arnaud Coustilliere, announced a sharp rise in online attacks against French web sites:
“Calling it an unprecedented surge, Adm. Arnaud Coustilliere, head of cyberdefense for the French military, said about 19,000 French websites had faced cyberattacks in recent days, …” [1].
As we’ve done in the recent past for North Korea [2], Hong-Kong [3], and Israel [4], we can leverage Arbor’s ATLAS initiative to observe how real world conflict is reflected in the digital realm. ATLAS receives anonymized Internet traffic and DDoS event data from over 330 participating Internet Service Providers worldwide. In particular, we are interested in DDoS attacks before and after Sunday, January 11th. As reported in [1],
“Coustilliere called the attacks a response to the massive demonstrations against terrorism that drew 3.7 million people into the streets Sunday across France.”
In order to gauge this response, we compare the DDoS attacks that took place between January 3rd and January 10th to the DDoS attacks that took place between January 11th and January 18th inclusive.
Attack Frequency
Between January 3rd and January 18th, a total of 11,342 Continue reading
That HP SDN App Store

December 2014 found me in Barcelona as a guest of HP at the “HP Discover” event. Nominally I went to see what was up in the world of networking, but as you can imagine with the breadth of products that HP produces, I found myself looking at all sorts of things. I’ll cover a few fun things in other posts, but I’ll start with a bit of networking because, well, this is MovingPackets after all.
HP SDN App Store
I mentioned the HP SDN App Store in a previous post about HP Openflow. One of the fears I raised was how an App Store would work in terms of support. Talking to a contact at HP made things a little clearer, and there’s actually quite a nice – and perhaps obvious – support plan for the Apps you can download. Effectively, there are three tiers of supported applications as I understand it, and a glance at the App Store shows that these are now called “Apps Circles”:
- App Circle 1: Apps that HP develops. These have full support direct from HP, as they are HP products, effectively.
- App Circle 2: Apps that are developed by HP AllianceOne partners Continue reading
News Analysis: Anuta NCX 4.0 Feature Updates for OpenStack, NFV, YANG
Anuta Networks’ NCX platform is for multi-vendor orchestration at scale. NCX fits in the SDN space, allowing operators to create service catalogs that can be deployed across a wide variety of gear from various networking vendors, including Cisco, Juniper, Brocade, and Ericsson. I co-hosted a webinar with a live demo of an earlier version […]Field Trip: Networking Field Day
Very excited to announce I was invited to participate in Networking Field Day #9. The first question is: What is Networking Day? Well it is an event where we (networkers) get to participate, listen, and interact with various different vendors. And I’ll be joining a great group, a few of which I’ve met at the […]Drums of cyberwar: North Korea’s cyber-WMDs
People ask me if today's NYTimes story changes my opinion that North Korea didn't do the Sony hack. Of course it doesn't. Any rational person can tell that the story is bogus. Indeed, such stories hint the government is hiding something.The story claims the NSA has thoroughly hacked North Korea since 2010, and that's what enabled the US government to tell who was responsible for the Sony hack. But if this were true, then we hacked first, and the Sony hack is retaliation -- meaning we had no justification for Obama's sanctions. But, if the story is false, then again sanctions against North Korea aren't justified, because we don't have the proof our government claims. True or false, this story means the U.S. sanctions against North Korea aren't justified.
The reason this story is nonsense is that it's not journalism. It relies almost entirely on anonymous sources in the government. These aren't anonymous whistle-blowers who fear retaliation, but government propagandists who don't want to be held accountable. The government exploits the New York Times, promising them exclusive breaking news in exchange for them publishing propaganda. This allows government to have a story that is simultaneous true and false, Continue reading
5 Network related things I am looking forward to in 2015
This blog is cross posted from my original blog found here Below is a list of the 5 network things I am looking forward to in 2015 (in no particular order). Analytics – Now this term has been around for … Continue readingWi-Fi: The jungle of the Unlisenced
This is a follow-up on the recently published Packet Pushers Show 221 – Marriott, Wifi, + the FCC with Glenn Fleishman & Lee Badman. Let me begin by stating my role in the ecospace: I am currently overseeing the expansion of broadband into Indianfield Co-operative Campground (indianfieldcampground.com) in the town of Salem (A less populous […]
Author information
vLAG Caveats in Brocade VCS Fabric
Brocade VCS fabric has one of the most flexible multichassis link aggregation group (LAG) implementation – you can terminate member links of an individual LAG on any four switches in the VCS fabric. Using that flexibility is not always a good idea.
2015-01-23: Added a few caveats on load distribution
Read more ...Docker Networking 101 – The defaults
 We’ve talked about docker in a few of my more recent posts but we haven’t really tackled how docker does networking. We know that docker can expose container services through port mapping, but that brings some interesting challenges along with it.
We’ve talked about docker in a few of my more recent posts but we haven’t really tackled how docker does networking. We know that docker can expose container services through port mapping, but that brings some interesting challenges along with it.
As with anything related to networking, our first challenge is to understand the basics. Moreover, to understand what our connectivity options are for the devices we want to connect to the network (docker(containers)). So the goal of this post is going to be to review docker networking defaults. Once we know what our host connectivity options are, we can spread quickly into advanced container networking.
So let’s start with the basics. In this post, I’m going to be working with two docker hosts, docker1 and docker2. They sit on the network like this…
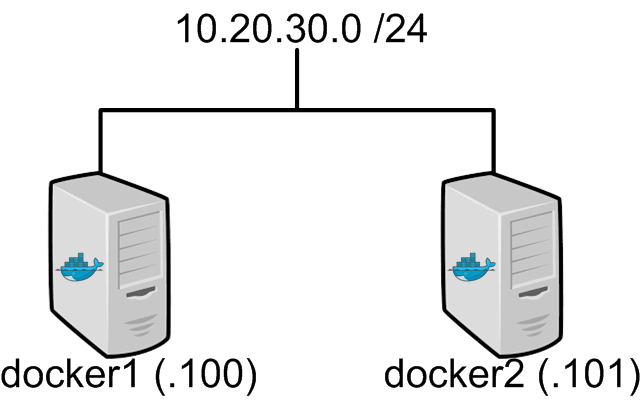
So nothing too complicated here. Two basic hosts with a very basic network configuration. So let’s assume that you’ve installed docker and are running with a default configuration. If you need instructions for the install see this. At this point, all I’ve done is configured a static IP on each host, configured a Continue reading
Free Chapter of “The Book of GNS3”
Hey Everyone! I wanted to release a quick note about a Free Chapter release from The Book of GNS3. The Book of GNS3 is written byValidation Testing Matters
A couple of weeks ago, a CLN Member Posted a question with the heading Does ASA drop active session.
The specific question was as follows–
I have a time based ACL configured on a Cisco ASA. I need to know if the active sessions are dropped by the ASA when the time limit is over.
For example, users are allowed to connect between 12 and 1 PM. If there are any active connections just before 1 PM then will they be dropped at 1 PM?
Many network and security administrators would blindly assume that a time-based ACL would block or allow traffic based on the time-range attached to the individual ACE. Having quite a lot of experience with the ASA, I was skeptical and assumed that any ongoing connections would continue to allow the flow of traffic. I decided to do a little testing and here is what I found.
- Viewing the ACL, the time based ACE (line in the ACL) switched from active to inactive about 60-70 seconds after I expected it to
- When testing with sessionized ICMP (fixup protocol icmp–to enable ICMP inspection), ICMP Echoes were blocked as soon as the ACE switched to inactive
- Testing with TCP, a connection through Continue reading
The Importance of Seeing Your Network Topology
by Alex Hoff, originally published on the Auvik blog As our product development adventure has unfolded over the past two years, we’veInteract with Ansible

Find Ansible on all of your favorite social networks and on the web.
LinkedIn (Group)
LinkedIn (Page)
Configuring a load balancer with VMware NSX
In the previous post a NAT has been configured to allow access from external networks: Now the edge router will act as a load balancer too: connection to the edge router with destination port 2222 will be balanced on both internal VM using the port 22. Go to “Networking & Security -> NSX Edges”, […]Configuring NAT and firewall on a NSX Edge Router
On a previous post the edge router has been connected to external network: In this post NAT and Firewall will be configured to allow SSH access to VM1 from external networks. Go to “Networking & Security -> NSX Edges”, double click on the edge router and follow “Manage -> NAT”. Add a DNAT role so […]But Does it Work?
When I was in the USAF, a long, long, time ago, there was a guy in my shop — Armand — who, no matter what we did around the shop, would ask, “but does it work?” For instance, when I was working on redoing the tool cabinet, with nice painted slots for each tool, he walked by — “Nice. But does it work?” I remember showing him where each tool fit, and how it would all be organized so we the pager went off at 2AM because the localizer was down (yet again), it would be easy to find that one tool you needed to fix the problem. He just shook his head and walked away. Again, later, I was working on the status board in the Group Readiness Center — the big white metal board that showed the current status of every piece of comm equipment on the Base — Armand walked by and said, “looks nice, but does it work?” Again, I showed him how the new arrangement was better than the old one. And again Armand just shook his head and walked away. It took me a long time to “get it” — to Continue reading
