DDoS Attacks in the Wake of French Anti-terror Demonstrations
On January 15th, France’s chief information systems defense official, Adm. Arnaud Coustilliere, announced a sharp rise in online attacks against French web sites:
“Calling it an unprecedented surge, Adm. Arnaud Coustilliere, head of cyberdefense for the French military, said about 19,000 French websites had faced cyberattacks in recent days, …” [1].
As we’ve done in the recent past for North Korea [2], Hong-Kong [3], and Israel [4], we can leverage Arbor’s ATLAS initiative to observe how real world conflict is reflected in the digital realm. ATLAS receives anonymized Internet traffic and DDoS event data from over 330 participating Internet Service Providers worldwide. In particular, we are interested in DDoS attacks before and after Sunday, January 11th. As reported in [1],
“Coustilliere called the attacks a response to the massive demonstrations against terrorism that drew 3.7 million people into the streets Sunday across France.”
In order to gauge this response, we compare the DDoS attacks that took place between January 3rd and January 10th to the DDoS attacks that took place between January 11th and January 18th inclusive.
Attack Frequency
Between January 3rd and January 18th, a total of 11,342 Continue reading


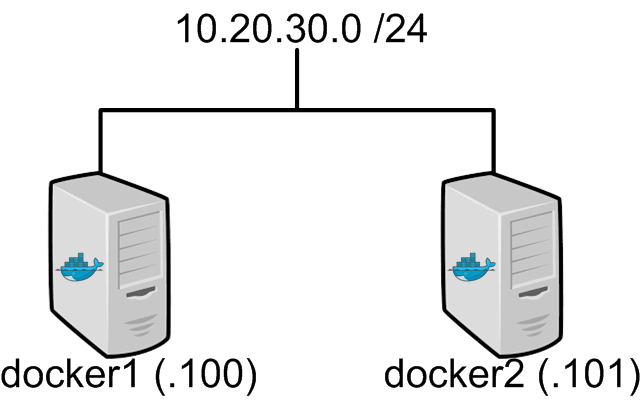
 We’ve talked about docker in a few of my more recent posts but we haven’t really tackled how docker does networking. We know that docker can expose container services through port mapping, but that brings some interesting challenges along with it.
We’ve talked about docker in a few of my more recent posts but we haven’t really tackled how docker does networking. We know that docker can expose container services through port mapping, but that brings some interesting challenges along with it.