Cisco IOS – Understanding IGP Network Statements
One of the things that I find both counterintuitive and often misunderstood is the role of the network command in interior gateway protocols. This command is used in the router configuration mode on Cisco devices. While there are some protocol specifics that should be understood, it behaves similarly between RIP, EIGRP and OSPF. The common misconception is that the network statement determines what will be advertised. While it can affect what is being advertised, that is not the direct purpose of this command.
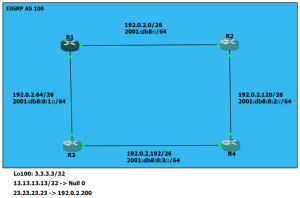
If you have mistakenly thought the network command determines what is being advertised, you’re certainly not alone. We can even find verbiage in the output of “show ip protocols” that lends credibility to this position. Let’s take a look at the following configuration.
In the above example, I have enable EIGRP on all of the interfaces.
R1 Configuration
interface Loopback0 ip address 1.1.1.1 255.255.255.0 interface Loopback1 ip address 2.2.2.1 255.255.255.0 interface FastEthernet0/0 ip address 192.168.1.1 255.255.255.0 router eigrp 1 network 1.1.1.1 0.0.0.0 network 2.2.2.1 0.0.0.0 network 192. Continue reading



 Last week, I spent a the majority of my commute time listening to a cybercrime novel by Mark Russinovich. This book, Trojan Horse, is the second of three books in the Jeff Aiken Novel series and didn’t disappoint in any way. In the past I read the electronic version of the first book, Zero Day. Whether or not you work in information security, you’ll likely find these books enjoyable. Having some grasp of the reach and dependance on information systems, I find these books are reasonably plausible. I plan to listen to the final installment in the series during my travels this week.
Last week, I spent a the majority of my commute time listening to a cybercrime novel by Mark Russinovich. This book, Trojan Horse, is the second of three books in the Jeff Aiken Novel series and didn’t disappoint in any way. In the past I read the electronic version of the first book, Zero Day. Whether or not you work in information security, you’ll likely find these books enjoyable. Having some grasp of the reach and dependance on information systems, I find these books are reasonably plausible. I plan to listen to the final installment in the series during my travels this week.