Debian 11 After Install Guide
I find Debian as one of the best Linux distros available. End users should generally […]
The post Debian 11 After Install Guide first appeared on Brezular's Blog.
Debian 11 After Install Guide
I find Debian as one of the best Linux distros available. End users should generally […]
Mashing Up CXL And Gen-Z For Shared Disaggregated Memory
If you are impatient for not just memory pooling powered by the CXL protocol, but the much more difficult task of memory sharing by servers attached to giant blocks of external memory, you are not alone. …
Mashing Up CXL And Gen-Z For Shared Disaggregated Memory was written by Timothy Prickett Morgan at The Next Platform.
Tech Bytes: Aruba Enhances Security Capabilities In EdgeConnect SD-WAN (Sponsored)
Today on the Tech Bytes podcast we’re talking SD-WAN. We dive into new features and capabilities in Aruba EdgeConnect SD-WAN, including new security and segmentation features, licensing options, and more. Our sponsor is Aruba, a Hewlett Packard Enterprise company.Tech Bytes: Aruba Enhances Security Capabilities In EdgeConnect SD-WAN (Sponsored)
Today on the Tech Bytes podcast we’re talking SD-WAN. We dive into new features and capabilities in Aruba EdgeConnect SD-WAN, including new security and segmentation features, licensing options, and more. Our sponsor is Aruba, a Hewlett Packard Enterprise company.
The post Tech Bytes: Aruba Enhances Security Capabilities In EdgeConnect SD-WAN (Sponsored) appeared first on Packet Pushers.
Ubuntu 20.04 Docker image – Python For Network Engineers
This is an updated Docker image of Python For Network Engineers (PFNE) based on Ubuntu 20.04 (minimal server distro). It contains all necessary tools for network / devops engineers to test automation and learn Python: OpensslNet-toolsIPutilsIProuteIPerfTCPDumpNMAPPython 2Python 3ParamikoNetmikoAnsiblePyntcNAPALMNetcatSocat If you notice a missing package which could be a value added for the scope of the … Continue reading Ubuntu 20.04 Docker image – Python For Network EngineersBGP Configuration on FortiOS
I’ve never done a post on Forti-anything, but I’m really appreciating the products Fortinet is putting out lately. They’re transitioning from “run your SMB off of our stuff” to “actually, we’re pretty good for larger companies”, so their GUI lacks features to keep the SMB from blowing stuff up, The advanced features are there in the CLI, and I wanted to use it to show that difference between the GUI and the real config.
Let’s review some of the basic configuration elements of BGP first. You need an autonomous system (AS) number and a router ID for your side. You also need the AS number of the remote system. You need the IP address on their side (usually the interface facing you). That looks something like this. We’re going to be ‘Fortigate 1’ for this exercise.
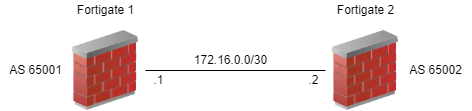
With just this information, we can turn up a BGP neighbor that does absolutely nothing. To actually send some routes, you need to tell BGP what to send. We’ll keep this simple and add just connected networks. Adding to the diagram, we get this.
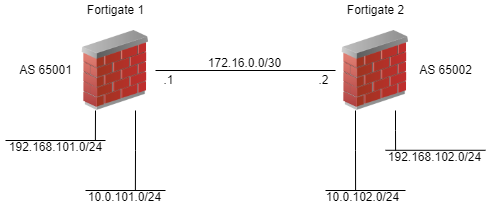
Now we have something of value (though choosing BGP over OSPF or RIP for this little scenario is pretty horrible). Continue reading
The Cloud Gets Foggy
The explosion of sensor and IoT data at the edge is forcing organizations to rethink the location of their data processing infrastructure, “bringing down” the cloud to the ground in the form of fog computing.Network Break 405: Tech And Geopolitics Collide; Juniper Posts Record Q3 Results
Take a Network Break! This week we discuss a trio of stories at the intersection of tech and global political power struggles. Plus, startup Versa Networks lands $120 million investment in a pre-IPO round, and tech companies including Juniper Networks, Intel, and Google/Alphabet release financial results.Network Break 405: Tech And Geopolitics Collide; Juniper Posts Record Q3 Results
Take a Network Break! This week we discuss a trio of stories at the intersection of tech and global political power struggles. Plus, startup Versa Networks lands $120 million investment in a pre-IPO round, and tech companies including Juniper Networks, Intel, and Google/Alphabet release financial results.
The post Network Break 405: Tech And Geopolitics Collide; Juniper Posts Record Q3 Results appeared first on Packet Pushers.
Lenovo And UConn Use HPC And AI To Predict The Weather
Sponsored Feature: Humans have wanted to know what the weather is going to do since first we understood how the forces of nature determined our expectations of survival. …
Lenovo And UConn Use HPC And AI To Predict The Weather was written by James Hayes at The Next Platform.
BGP Configuration on FortiOS
I’ve never done a post on Forti-anything, but I’m really appreciating the products Fortinet is putting out lately. They’re transitioning from “run your SMB off of our stuff” to “actually, we’re pretty good for larger companies”, so their GUI lacks features to keep the SMB from blowing stuff up, The advanced features are there in the CLI, and I wanted to use it to show that difference between the GUI and the real config.
Let’s review some of the basic configuration elements of BGP first. You need an autonomous system (AS) number and a router ID for your side. You also need the AS number of the remote system. You need the IP address on their side (usually the interface facing you). That looks something like this. We’re going to be ‘Fortigate 1’ for this exercise.
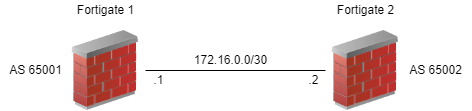
With just this information, we can turn up a BGP neighbor that does absolutely nothing. To actually send some routes, you need to tell BGP what to send. We’ll keep this simple and add just connected networks. Adding to the diagram, we get this.
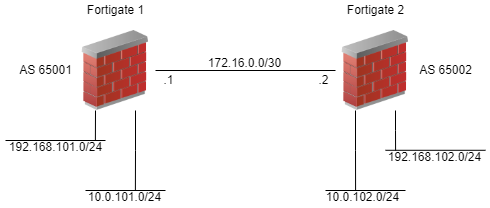
Now we have something of value (though choosing BGP over OSPF or RIP for this little scenario is pretty horrible). Continue reading
Apple Only Pays 48M per year in Bug Bounties ?
 This article from Apple boggles my brain: Apple Security Bounty. Upgraded. – Apple Security Research – https://security.apple.com/blog/apple-security-bounty-upgraded/ In the past two and a half years since opening our program, we’re incredibly proud to have awarded researchers nearly $20 million in total payments, with an average payout of $40,000 in the Product category, and including 20 […]
This article from Apple boggles my brain: Apple Security Bounty. Upgraded. – Apple Security Research – https://security.apple.com/blog/apple-security-bounty-upgraded/ In the past two and a half years since opening our program, we’re incredibly proud to have awarded researchers nearly $20 million in total payments, with an average payout of $40,000 in the Product category, and including 20 […]
Let Ansible keep an eye on your AWS environment
In a cloud model, the security of the environment and compliance becomes the responsibility of both the end users and the cloud provider. This is what we call the shared responsibility model in which every part of the cloud, including the hardware, data, configurations, access rights, and operating system, are protected. Depending on the local legislation and the origin of the data that is handled (for instance laws like HIPAA, the GDPR in Europe, or the Californian CCPA), you may have to enforce strict rules on your environment and log events for audit purposes. AWS CloudTrail will help you to achieve this goal. The service can collect and record any kind of information coming from your environment and store or send the events to a destination for audit. In addition to security and compliance, this service helps keep track of resource consumption.
Ansible’s CloudTrail module is used to leverage the various features of the CloudTrail service to monitor and audit user activities and API calls in the AWS environment. A trail is a configuration that lets us describe an event filter and decide where the matching entries should be sent. The recent 5.0.0 release of the Amazon.aws Continue reading