BiB097: VMware’s Future In The Cloud-Native Era
Kit Colbert is the VP & CTO, Cloud Platform BU at VMware. In this briefing, Drew Conry-Murray and Ethan Banks reflect on a Zoom conversation they had with Kit during VMworld 2020. The context of the conversation was simple enough. Harshly stated, we wanted to know what VMware's future is in the cloud-native era. Will companies need VMware? Kit's answer was not hand-wavy, cheerleader-ish nonsense. Instead, he responded with a thoughtful plan.
The post BiB097: VMware’s Future In The Cloud-Native Era appeared first on Packet Pushers.
The Internet Is Built on ‘Intermediaries’ – They Should Be Protected

This opinion piece was originally published in The Hill.
Now is not the time to be careless with laws that could harm the Internet we rely on more than ever in our day to day lives.
Policymakers owe it to the billions of users around world that rely on the Internet for work, education, and daily activities to do their homework before attempting to change laws so pivotal to the Internet’s success.
And yet, the uptick of lawmakers making hasty changes to the law known as “Section 230” is proof of uninformed decision making that has the future of a law that helped shape the Internet looking increasingly grim.
In the last two years, there have been at least 18 attempts – via bills, executive orders and other initiatives – to try blow up the rule that has kept Internet intermediaries from being liable from the actions of their users since 1996. Within each of those efforts, the definition of what will be impacted has varied widely from “platforms” to “interactive computer services” and “Internet intermediaries.”
Depending on these definitions, and the larger policies they are attached to, the associated impacts of these proposals could be annoying, or they could Continue reading
Introducing Automatic Platform Optimization, starting with WordPress


Today, we are announcing a new service to serve more than just the static content of your website with the Automatic Platform Optimization (APO) service. With this launch, we are supporting WordPress, the most popular website hosting solution serving 38% of all websites. Our testing, as detailed below, showed a 72% reduction in Time to First Byte (TTFB), 23% reduction to First Contentful Paint, and 13% reduction in Speed Index for desktop users at the 90th percentile, by serving nearly all of your website’s content from Cloudflare’s network. This means visitors to your website see not only the first content sooner but all content more quickly.
With Automatic Platform Optimization for WordPress, your customers won’t suffer any slowness caused by common issues like shared hosting congestion, slow database lookups, or misbehaving plugins. This service is now available for anyone using WordPress. It costs $5/month for customers on our Free plan and is included, at no additional cost, in our Professional, Business, and Enterprise plans. No usage fees, no surprises, just speed.
How to get started
The easiest way to get started with APO is from your WordPress admin console.
1. First, install the Cloudflare WordPress plugin on your WordPress Continue reading
Building Automatic Platform Optimization for WordPress using Cloudflare Workers

This post explains how we implemented the Automatic Platform Optimization for WordPress. In doing so, we have defined a new place to run WordPress plugins, at the edge written with Cloudflare Workers. We provide the feature as a Cloudflare service but what’s exciting is that anyone could build this using the Workers platform.
The service is an evolution of the ideas explained in an earlier zero-config edge caching of HTML blog post. The post will explain how Automatic Platform Optimization combines the best qualities of the regular Cloudflare cache with Workers KV to improve cache cold starts globally.
The optimization will work both with and without the Cloudflare for WordPress plugin integration. Not only have we provided a zero config edge HTML caching solution but by using the Workers platform we were also able to improve the performance of Google font loading for all pages.
We are launching the feature first for WordPress specifically but the concept can be applied to any website and/or content management system (CMS).
A new place to run WordPress plugins?
There are many individual WordPress plugins for performance that use similar optimizations to existing Cloudflare services. Automatic Platform Optimization is bringing them all together into Continue reading
DNS Flag Day 2020


October 1 was this year’s DNS Flag Day. Read on to find out all about DNS Flag Day and how it affects Cloudflare’s DNS services (hint: it doesn’t, we already did the work to be compliant).
What is DNS Flag Day?
DNS Flag Day is an initiative by several DNS vendors and operators to increase the compliance of implementations with DNS standards. The goal is to make DNS more secure, reliable and robust. Rather than a push for new features, DNS flag day is meant to ensure that workarounds for non-compliance can be reduced and a common set of functionalities can be established and relied upon.
Last year’s flag day was February 1, and it set forth that servers and clients must be able to properly handle the Extensions to DNS (EDNS0) protocol (first RFC about EDNS0 are from 1999 - RFC 2671). This way, by assuming clients have a working implementation of EDNS0, servers can resort to always sending messages as EDNS0. This is needed to support DNSSEC, the DNS security extensions. We were, of course, more than thrilled to support the effort, as we’re keen to push DNSSEC adoption forward .
DNS Flag Day 2020
The goal for Continue reading
Network Operating Systems: Questions and Answers
James Miles got tons of really interesting questions while watching the Network Operating System Models webinar by Dinesh Dutt, and the only reasonable thing to do when he sent them over was to schedule a Q&A session with Dinesh to discuss them.
We got together last week and planned to spend an hour or two discussing the questions, but (not exactly unexpectedly) we got only halfway through the list in the time we had, so we’re continuing next week.
Network Operating Systems: Questions and Answers
James Miles got tons of really interesting questions while watching the Network Operating System Models webinar by Dinesh Dutt, and the only reasonable thing to do when he sent them over was to schedule a Q&A session with Dinesh to discuss them.
We got together last week and planned to spend an hour or two discussing the questions, but (not exactly unexpectedly) we got only halfway through the list in the time we had, so we’re continuing next week.
Toward an API for the real numbers
Towards an API for the real numbers, Boehm, PLDI’20
Last time out we saw that even in scientific computing applications built by experts, problems with floating point numbers are commonplace. The idiosyncrasies of floating point representations also show up in more everyday applications such as calculators and spreadsheets. Here the user-base is less inclined to be sympathetic:
If arithmetic computations and results are directly exposed to human users who are not floating point experts, floating point approximations tend to be viewed as bugs.
Hans-J. Boehm, author of today’s paper, should know, because he’s been involved in the development of the Android calculator app. That app is subject to “voluminous (public) user feedback”, and in the 2014 floating-point based calculator, bug reports relating to inaccurate results, unnecessary zeroes, and the like.
It’s a classic software development moment. The bug / feature request that looks just like any other ordinary issue on the outside, but takes you from straightforward implementation to research-level problem on the inside! In this case, the realisation that you can’t just use standard IEEE floating point operations anymore.
For calculators, spreadsheets, and many other applications we don’t need the raw performance of hardware floating point operations. But Continue reading
Integrating 5G Edge Services into Enterprise Networks
The biggest factor in choosing a 5G edge computing provider will likely be based on which 5G services are available where your business requires them.The Docker Dashboard Welcomes Hub and Local Images
Last year we released the Docker Dashboard as part of Docker Desktop, today we are excited to announce we are releasing the next piece of the dashboard to our community customers with a new Images UI. We have expanded the existing UI for your local machine with the ability to interact with your Docker images on Docker Hub and locally. This allows you to: display your local images, manage them (run, inspect, delete) through an intuitive UI without using the CLI. And for you images in Hub you can now view you repos or your teams repos and pull images directly from the UI.
To get started, Download the latest Docker Desktop release and load up the dashboard (we are also excited that we have given the dashboard an icon )
)
You will be able to see that we have also added a new sidebar to navigate between the two areas and we are planning to add new sections in here soon. To find out more about what’s coming or to give feedback on what you would like to see check out our public roadmap.
Let’s jump in and have a look at what we can do…
From Continue reading
Launching the First-Ever Virtual Indigenous Connectivity Summit

COVID-19 has moved many of our lives online, and our conversations around how to further broadband access are no exception. This year, the Indigenous Connectivity Summit is happening virtually for the first time.
After meeting in Santa Fe, Inuvik, and Waimanalo and Hilo, this year we had planned to meet in Winnipeg – the city with the highest Indigenous population in Canada. We will sorely miss seeing our ICS community in person, but we are excited to meet online and demonstrate how important it is for Indigenous communities to connect to the Internet.
An important aspect of the ICS is the space created for community members to engage in conversations sharing similar challenges, connecting with one another, and innovating solutions to the lack of broadband access in their communities. We are excited to continue having these impactful conversations virtually and to recreate a more discussion-based environment than in a typical webinar format. We are also looking forward to having new faces join us this year. Without the barrier of travel, we can now engage with more participants from different communities.
The conversations we hold at the ICS hold significant weight in the policy world. Take our conversations around the Tribal Continue reading
Docker Names Donnie Berkholz to Vice President of Products
To deepen Docker’s investment in products that make developers successful, we’re pleased to announce that Donnie Berkholz will join the Docker team as VP of Products. Donnie has an extensive background as a practitioner, leader, and advisor on developer platforms and communities. He spent more than a decade as an open-source developer and leader at Gentoo Linux, and he recently served as a product and technology VP at CWT overseeing areas including DevOps and developer services. Donnie’s also spent time at RedMonk, 451 Research, and Scale Venture Partners researching and advising on product and market strategy for DevOps and developer products.

To get to know Donnie, we asked him a few questions about his background and where he plans to focus in his new role:
What got you the most excited about joining Docker?
I’ve been a big fan of Docker’s technology since the day it was announced. At the time, I was an industry analyst with RedMonk, and I could instantly sense the incredible impact that it would have in transforming the modern developer experience. Recent years have borne that out with the astonishing growth in popularity of containers and cloud-native development. With Docker’s renewed focus on developers, Continue reading
NTS RFC Published: New Standard to Ensure Secure Time on the Internet

The Internet Society is pleased to see the publication of RFC 8915: Network Time Security for the Network Time Protocol by the Internet Engineering Task Force (IETF). This standard represents a new security mechanism for one of the oldest protocols on the Internet, the Network Time Protocol (NTP).
Secure and Accurate Time
NTP enables the synchronization of time on computers connected by a network. Time is very important for many vital everyday functions, such as financial transactions and the correct operation of electrical power systems and transportation systems. Secure and accurate time is also crucial for many Internet security technologies including basic website security. As everything becomes more distributed and more online, synchronized time in computers becomes even more important. But despite all this, security for NTP has lagged behind in development and deployment. Network Time Security (NTS) was developed to fill this gap.
The publication of the NTS protocol on 1 October, 2020 represents the culmination of many years of work by the IETF NTP Working Group. NTS adds cryptographic security for the client-server mode of NTP. So, what does this mean? It means that NTP can now confirm the identity of the network clocks that are exchanging time Continue reading
NTS is now an RFC
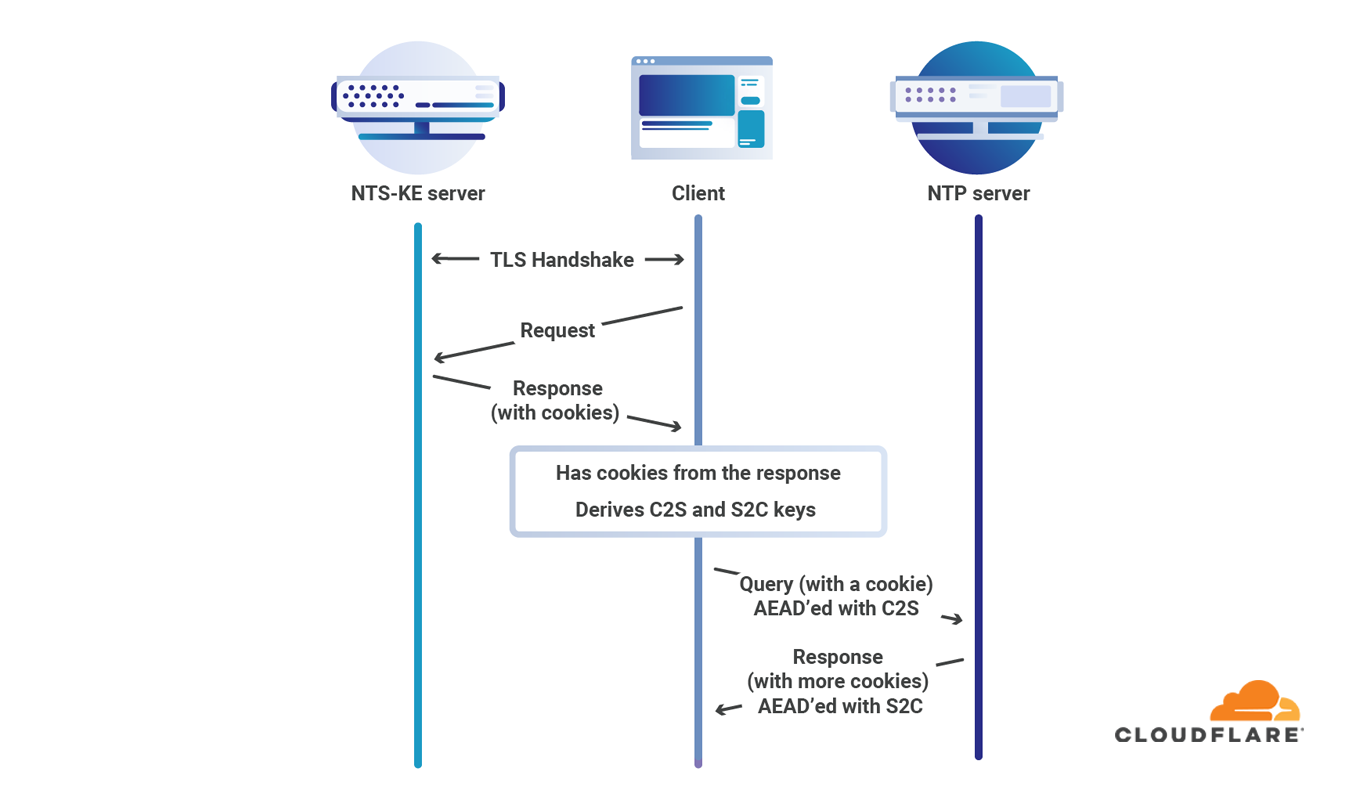
Earlier today the document describing Network Time Security for NTP officially became RFC 8915. This means that Network Time Security (NTS) is officially part of the collection of protocols that makes the Internet work. We’ve changed our time service to use the officially assigned port of 4460 for NTS key exchange, so you can use our service with ease. This is big progress towards securing a ubiquitous Internet protocol.
Over the past months we’ve seen many users of our time service, but very few using Network Time Security. This leaves computers vulnerable to attacks that imitate the server they use to obtain NTP. Part of the problem was the lack of available NTP daemons that supported NTS. That problem is now solved: chrony and ntpsec both support NTS.
Time underlies the security of many of the protocols such as TLS that we rely on to secure our online lives. Without accurate time, there is no way to determine whether or not credentials have expired. The absence of an easily deployed secure time protocol has been a problem for Internet security.
Without NTS or symmetric key authentication there is no guarantee that your computer is actually talking NTP with the computer Continue reading