Daily Roundup: Deutsche Telekom, Vodafone Embrace 5G DSS
Deutsche Telekom, Vodafone Germany embraced 5G DSS; Edgewise Networks CEO shared security-related...
Deutsche Telekom, Vodafone Germany embraced 5G DSS; Edgewise Networks CEO shared security-related...
Security has always been important for datacenter operators, but the days of putting a ring of protection around the datacenter and then walking away satisfied in the knowledge that the data and applications therein were protected from outside forces are long over. …
Locking Down Linux For The Enterprise was written by Jeffrey Burt at The Next Platform.
CenturyLink experienced the single largest gain in billable installations in 2019, according to...
Edgewise Networks CEO Peter Smith discusses the rapid shift to remote work because of COVID-19 and...
If you’ve used Cluster API (CAPI), you may have noticed that workload clusters created by CAPI use, by default, a “stacked master” configuration—that is, the etcd cluster is running co-located on the control plane node(s) alongside the Kubernetes control plane components. This is a very common configuration and is well-suited for most deployments, so it makes perfect sense that this is the default. There may be cases, however, where you’ll want to use a dedicated, external etcd cluster for your Kubernetes clusters. In this post, I’ll show you how to use an external etcd cluster with CAPI on AWS.
The information in this blog post is based on this upstream document. I’ll be adding a little bit of AWS-specific information, since I primarily use the AWS provider for CAPI. This post is written with CAPI v1alpha3 in mind.
The key to this solution is building upon the fact that CAPI leverages kubeadm for bootstrapping cluster nodes. This puts the full power of the kubeadm API at your fingertips—which in turn means you have a great deal of flexibility. This is the mechanism whereby you can tell CAPI to use an external etcd cluster instead of creating a co-located etcd Continue reading
The race to blanket Germany with 5G got underway last July and market leader Deutsche Telekom now...
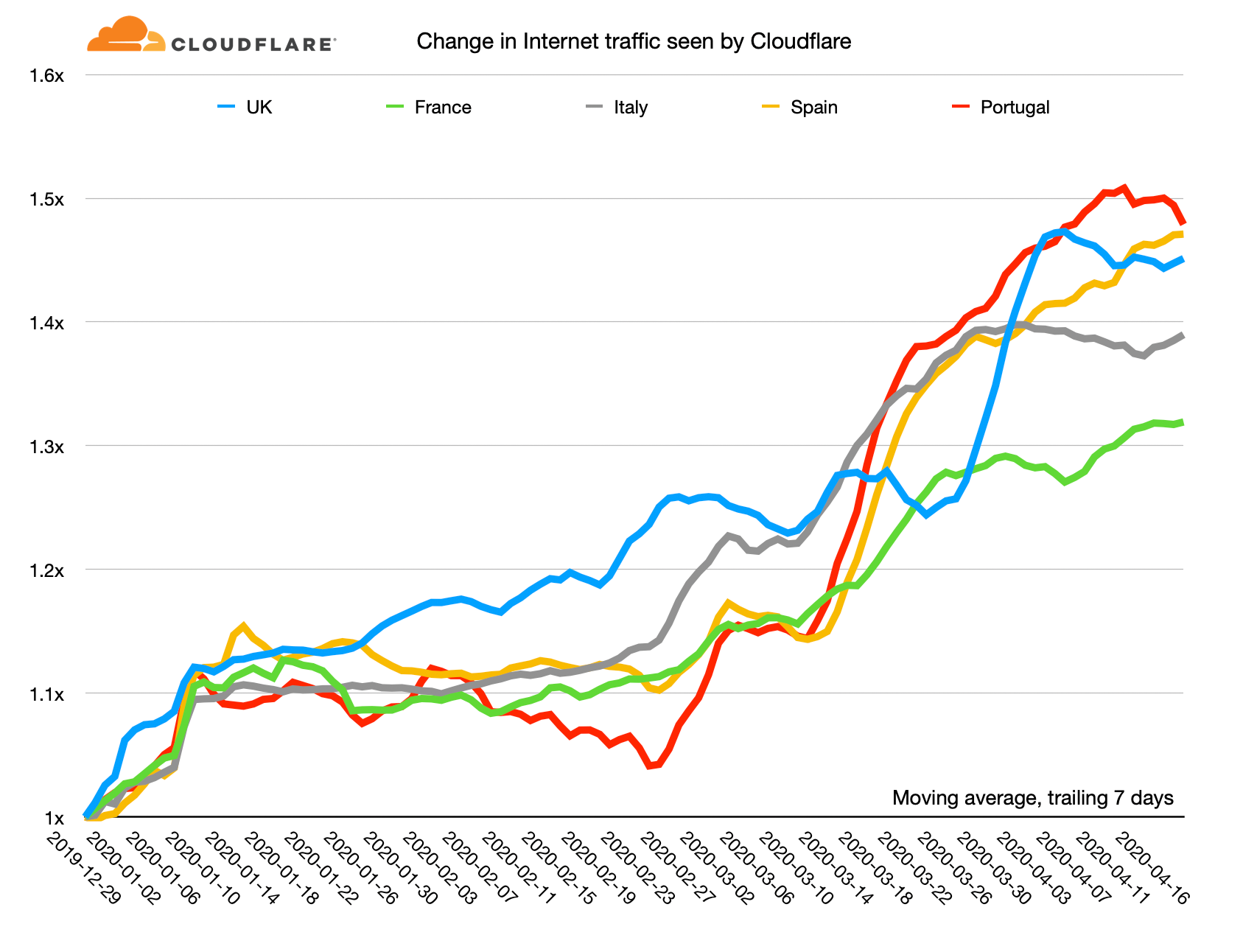
A month ago I wrote about changes in Internet traffic caused by the COVID-19 emergency. At the time I wrote:
Cloudflare is watching carefully as Internet traffic patterns around the world alter as people alter their daily lives through home-working, cordon sanitaire, and social distancing. None of these traffic changes raise any concern for us. Cloudflare's network is well provisioned to handle significant spikes in traffic. We have not seen, and do not anticipate, any impact on our network's performance, reliability, or security globally.
That holds true today; our network is performing as expected under increased load. Overall the Internet has shown that it was built for this: designed to handle huge changes in traffic, outages, and a changing mix of use. As we are well into April I thought it was time for an update.
Here's a chart showing the relative change in Internet use as seen by Cloudflare since the beginning of the year. I've calculated moving average of the trailing seven days for each country and use December 29, 2019 as the reference point.
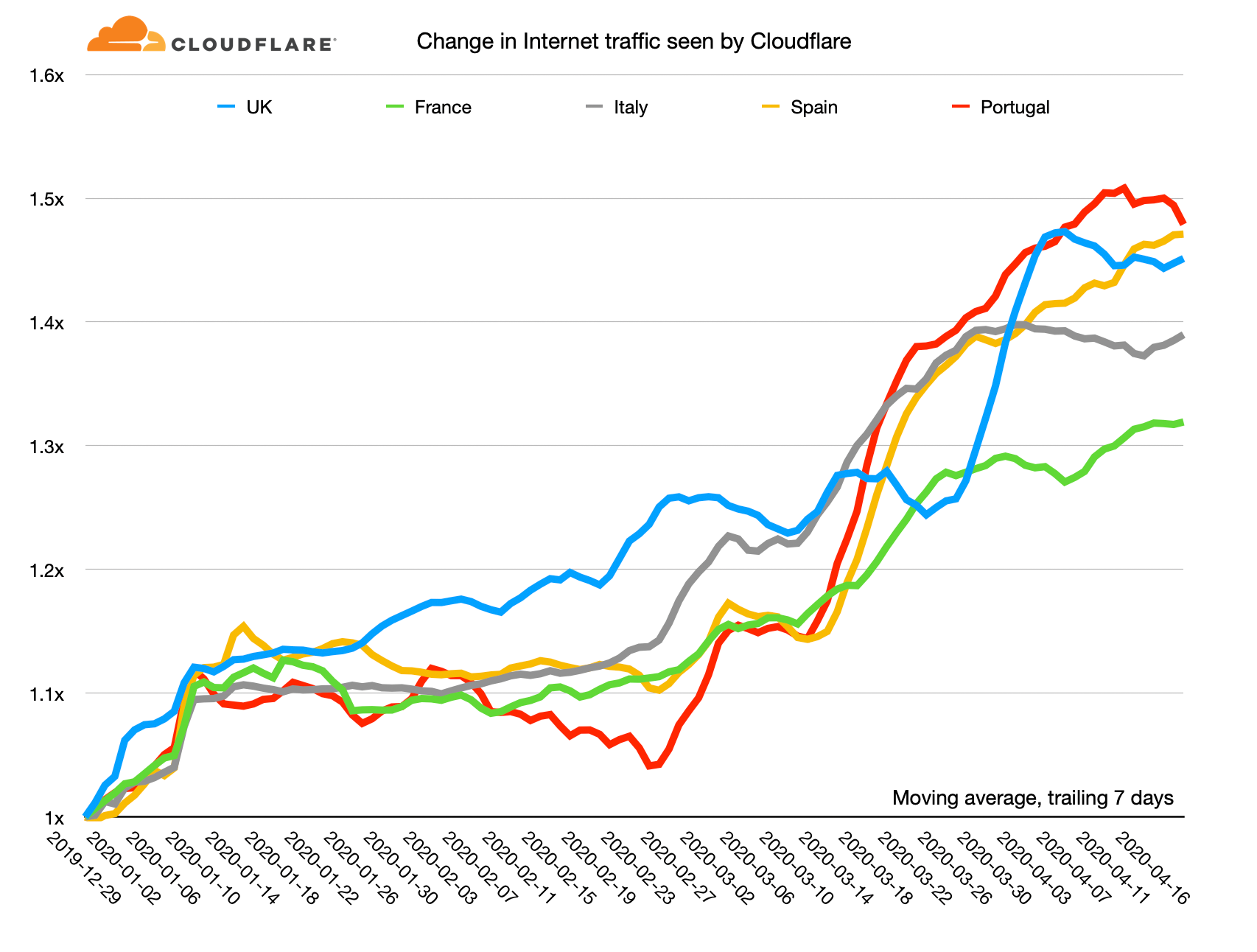
On this chart the highest growth in Internet use has been in Portugal: it's currently running at about a 50% increase Continue reading
The Internet Society Elections Committee is pleased to announce the final results of the 2020 elections and the IETF selection for the Board of Trustees.
The voting concluded on 3 April. The results were announced and the challenge period was opened on 6 April. The deadline to file challenges was 15 April. One challenge was filed in the Chapters election. In accordance with the Procedures for Selecting Trustees, Internet Society President Andrew Sullivan, the chairs of the Nominations and Elections committees, and the other members of the board discussed the merits of the challenge. In the end, the board decided that the challenge was without merit and rejected it.
Therefore, the election results announced on 6 April stand:
Also, following the process documented in RFC 3677, the Internet Architecture Board, on behalf of the IETF, has selected:
The term of office for all of the new Trustees will be three years, commencing with the 2020 Annual General Meeting, 1-2 August.
The Elections Committee congratulates all the new Trustees and expresses its gratitude once more to all Continue reading
If you’re in Las Vegas, Nevada, and are looking for the best places to enjoy your time and your quality business networking, do your research first and don’t spread yourself too thin.
There is a huge difference between the Las Vegas business referral organization and Las Vegas business networking organization. Here are a few you should get to know well.
Both networking organizations and business referral organizations could be really valuable to make your business grow. If you are a member of BNI for a very long time in Las Vegas and if you put the effort into the business networking group, it would help your business grow in ways you can’t imagine. They both meet every week and attendance is necessary.
Trustegrity gathers its members once a month and gives you relationships and increase the number of referrals among those in it. It is not strict about the whole one person per profession like BNI. In Las Vegas, there are a lot of different other business networking organizations that feature one member per profession. They usually have a structure in which they meet either twice a week or once a week. Continue reading
A reader of my blog sent me this question:
Do you think we can trust DSCP marking on servers (whether on DC or elsewhere - Windows or Linux )?
As they say “not as far as you can throw them”.
Does that mean that the network should do application recognition and marking on the ingress network node? Absolutely not, although the switch- and router vendors adore the idea of solving all problems on their boxes.
I’ve written before about how to use existing AWS infrastructure with Cluster API (CAPI), and I was recently able to help update the upstream documentation on this topic (the upstream documentation should now be considered the authoritative source). These instructions are perfect for placing a Kubernetes cluster into an existing VPC and associated subnets, but there’s one scenario that they don’t yet address: what if you need your CAPI workload cluster to be able to communicate with other EC2 instances or other AWS services in the same VPC? In this post, I’ll show you the CAPI functionality that makes this possible.
One of the primary mechanisms used in AWS to control communications among instances and services is the security group. I won’t go into any detail on security groups, but this page from AWS provides an explanation and overview of how security groups work.
In order to make a CAPI workload cluster able to communicate with other EC2 instances or other AWS services, you’ll need to somehow use security groups to make that happen. There are at least two—possibly more—ways to accomplish this:
IBM and Fortanix doubled down on confidential computing; Google Anthos built a bridge to AWS; and...
Subscribe to Kernel of Truth on iTunes, Google Play, Spotify, Cast Box and Sticher!
Click here for our previous episode.
Hosts Roopa Prabhu and Pete Lumbis are joined by a special guest to the podcast, Russ White! The group come together virtually to discuss what we should think about when it comes to routing protocols in the datcenter. What are the tradeoffs when using traditional protocols like OSPF or BGP? What about new protocols like RIFT or a hybrid approach with things like BGP-link state? Spoiler alert: it depends.
Guest Bios
Roopa Prabhu: Roopa Prabhu is Chief Linux Architect at Cumulus Networks. At Cumulus she and her team work on all things kernel networking and Linux system infrastructure areas. Her primary focus areas in the Linux kernel are Linux bridge, Netlink, VxLAN, Lightweight tunnels. She is currently focused on building Linux kernel dataplane for E-VPN. She loves working at Cumulus and with the Linux kernel networking and debian communities. Her past experience includes Linux clusters, ethernet drivers and Linux KVM virtualization platforms. She has a BS and MS in Computer Science. You can find her on Twitter at @__roopa.
Pete Lumbis: Pete, CCIE R&S #28677 and CCDE 2012::3, is Continue reading
Ericsson closed Q1 with 86 commercial 5G contracts and 29 live 5G networks. It activated an...
The European Union has made it clear that it wants to be able to stand on its own two feet in the design of server processors, for both general purpose uses and for exascale-class supercomputers. …
Drilling Down Into The SiPearl European Arm Server Chip was written by Timothy Prickett Morgan at The Next Platform.