Zaraz launches new pricing
In July, 2023, we announced that Zaraz was transitioning out of beta and becoming available to all Cloudflare users. Zaraz helps users manage and optimize the ever-growing number of third-party tools on their websites — analytics, marketing pixels, chatbots, and more — without compromising on speed, privacy, or security. Soon after the announcement went online, we received feedback from users who were concerned about the new pricing system. We discovered that in some scenarios the proposed pricing could cause high charges, which was not the intention, and so we promised to look into it. Since then, we have iterated over different pricing options, talked with customers of different sizes, and finally reached a new pricing system that we believe is affordable, predictable, and simple. The new pricing for Zaraz will take effect on April 15, 2024, and is described below.
Introducing Zaraz Events
One of the biggest changes we made was changing the metric we used for pricing Zaraz. One Zaraz Event is an event you’re sending to Zaraz, whether that’s a pageview, a zaraz.track event, or similar. You can easily see the total number of Zaraz Events you’re currently using under the Monitoring section in the Cloudflare Zaraz Continue reading
Remediating new DNSSEC resource exhaustion vulnerabilities

Cloudflare has been part of a multivendor, industry-wide effort to mitigate two critical DNSSEC vulnerabilities. These vulnerabilities exposed significant risks to critical infrastructures that provide DNS resolution services. Cloudflare provides DNS resolution for anyone to use for free with our public resolver 1.1.1.1 service. Mitigations for Cloudflare’s public resolver 1.1.1.1 service were applied before these vulnerabilities were disclosed publicly. Internal resolvers using unbound (open source software) were upgraded promptly after a new software version fixing these vulnerabilities was released.
All Cloudflare DNS infrastructure was protected from both of these vulnerabilities before they were disclosed and is safe today. These vulnerabilities do not affect our Authoritative DNS or DNS firewall products.
All major DNS software vendors have released new versions of their software. All other major DNS resolver providers have also applied appropriate mitigations. Please update your DNS resolver software immediately, if you haven’t done so already.
Background
Domain name system (DNS) security extensions, commonly known as DNSSEC, are extensions to the DNS protocol that add authentication and integrity capabilities. DNSSEC uses cryptographic keys and signatures that allow DNS responses to be validated as authentic. DNSSEC protocol specifications have certain requirements that prioritize availability at Continue reading
Unlocking new use cases with 17 new models in Workers AI, including new LLMs, image generation models, and more

On February 6th, 2024 we announced eight new models that we added to our catalog for text generation, classification, and code generation use cases. Today, we’re back with seventeen (17!) more models, focused on enabling new types of tasks and use cases with Workers AI. Our catalog is now nearing almost 40 models, so we also decided to introduce a revamp of our developer documentation that enables users to easily search and discover new models.
The new models are listed below, and the full Workers AI catalog can be found on our new developer documentation.
Text generation
- @cf/deepseek-ai/deepseek-math-7b-instruct
- @cf/openchat/openchat-3.5-0106
- @cf/microsoft/phi-2
- @cf/tinyllama/tinyllama-1.1b-chat-v1.0
- @cf/thebloke/discolm-german-7b-v1-awq
- @cf/qwen/qwen1.5-0.5b-chat
- @cf/qwen/qwen1.5-1.8b-chat
- @cf/qwen/qwen1.5-7b-chat-awq
- @cf/qwen/qwen1.5-14b-chat-awq
- @cf/tiiuae/falcon-7b-instruct
- @cf/defog/sqlcoder-7b-2
Summarization
- @cf/facebook/bart-large-cnn
Text-to-image
- @cf/lykon/dreamshaper-8-lcm
- @cf/runwayml/stable-diffusion-v1-5-inpainting
- @cf/runwayml/stable-diffusion-v1-5-img2img
- @cf/bytedance/stable-diffusion-xl-lightning
Image-to-text
- @cf/unum/uform-gen2-qwen-500m
New language models, fine-tunes, and quantizations
Today’s catalog update includes a number of new language models so that developers can pick and choose the best LLMs for their use cases. Although most LLMs can be generalized to work in any instance, there are many benefits to choosing models that are tailored for a specific use case. We are excited to bring you some new large language models (LLMs), small language models (SLMs), Continue reading
Open sourcing Pingora: our Rust framework for building programmable network services

Today, we are proud to open source Pingora, the Rust framework we have been using to build services that power a significant portion of the traffic on Cloudflare. Pingora is released under the Apache License version 2.0.
As mentioned in our previous blog post, Pingora is a Rust async multithreaded framework that assists us in constructing HTTP proxy services. Since our last blog post, Pingora has handled nearly a quadrillion Internet requests across our global network.
We are open sourcing Pingora to help build a better and more secure Internet beyond our own infrastructure. We want to provide tools, ideas, and inspiration to our customers, users, and others to build their own Internet infrastructure using a memory safe framework. Having such a framework is especially crucial given the increasing awareness of the importance of memory safety across the industry and the US government. Under this common goal, we are collaborating with the Internet Security Research Group (ISRG) Prossimo project to help advance the adoption of Pingora in the Internet’s most critical infrastructure.
In our previous blog post, we discussed why and how we built Pingora. In this one, we will talk about why and how you might Continue reading
Enhancing security analysis with Cloudflare Zero Trust logs and Elastic SIEM

Today, we are thrilled to announce new Cloudflare Zero Trust dashboards on Elastic. Shared customers using Elastic can now use these pre-built dashboards to store, search, and analyze their Zero Trust logs.
When organizations look to adopt a Zero Trust architecture, there are many components to get right. If products are configured incorrectly, used maliciously, or security is somehow breached during the process, it can open your organization to underlying security risks without the ability to get insight from your data quickly and efficiently.
As a Cloudflare technology partner, Elastic helps Cloudflare customers find what they need faster, while keeping applications running smoothly and protecting against cyber threats. “I'm pleased to share our collaboration with Cloudflare, making it even easier to deploy log and analytics dashboards. This partnership combines Elastic's open approach with Cloudflare's practical solutions, offering straightforward tools for enterprise search, observability, and security deployment,” explained Mark Dodds, Chief Revenue Officer at Elastic.
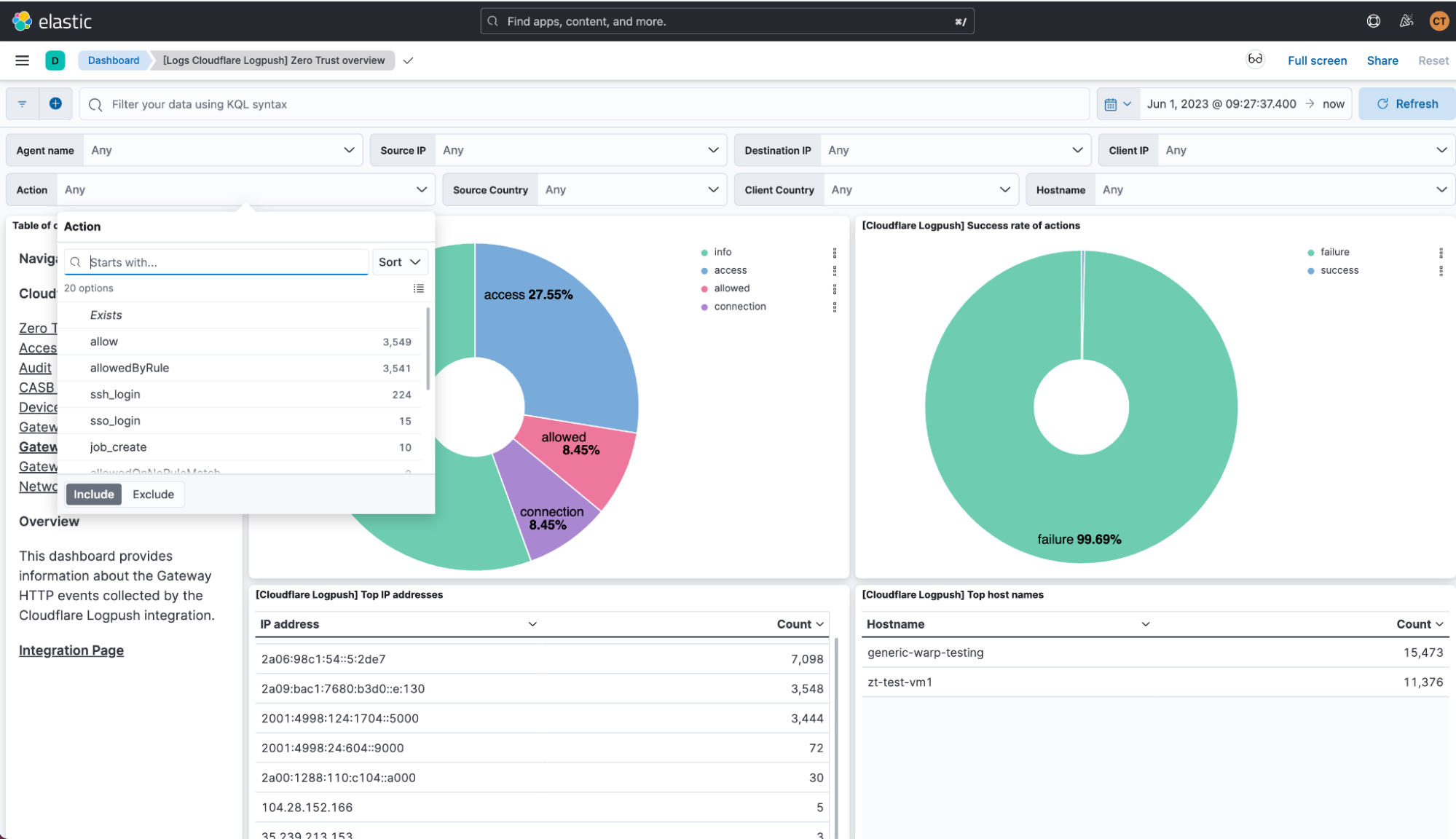
Value of Zero Trust logs in Elastic
With this joint solution, we’ve made it easy for customers to seamlessly forward their Zero Trust logs to Elastic via Logpush jobs. This can be achieved directly via a Restful API or through an intermediary storage solution like Continue reading
All you need to know about the Digital Services Act
February 17th, 2024 marked the entry into force of a landmark piece of European Union (EU) legislation, affecting European users who create and disseminate online content as well as tech companies who act as “intermediaries” on the Internet. I am talking of course about the EU Digital Services Act, or DSA for short. The DSA was first proposed in December 2020, and is meant to update a 20-year-old law called the EU e-commerce Directive, which provides important safeguards and legal certainty for all businesses operating online. The principles of that legal framework, most notably the introduction of EU-wide rules on intermediary liability, are still of major importance today. The DSA is a landmark piece of European legislation because it also sets out, for the first time, enhanced regulatory requirements for (large) digital platforms, thus affecting the entire Internet ecosystem.
At Cloudflare, we are supportive of the longstanding legal frameworks both in Europe and other parts of the world that protect Internet companies from liability for the content that is uploaded or sent through their networks by their users, subscribers or customers. These frameworks are indispensable for the growth of online services, and have been essential in the growth Continue reading
Monitoring machine learning models for bot detection

Cloudflare’s Bot Management is used by organizations around the world to proactively detect and mitigate automated bot traffic. To do this, Cloudflare leverages machine learning models that help predict whether a particular HTTP request is coming from a bot or not, and further distinguishes between benign and malicious bots. Cloudflare serves over 55 million HTTP requests per second — so our machine learning models need to run at Cloudflare scale.
We are constantly making improvements to the models that power Bot Management to ensure they are incorporating the latest threat intelligence. This process of iteration is an important part of ensuring our customers stay a step ahead of malicious actors, and it requires a rigorous process for experimentation, deployment, and ongoing observation.
We recently shared an introduction to Cloudflare’s approach to MLOps, which provides a holistic overview of model training and deployment processes at Cloudflare. In this post, we will dig deeper into monitoring, and how we continuously evaluate the models that power Bot Management.
Why monitoring matters
Before bot detection models are released, we undergo an extensive model testing/validation process to ensure our detections perform as expected. Model performance is validated across a wide number of web traffic Continue reading
Safeguarding your brand identity: Logo Matching for Brand Protection
In an era dominated by digital landscapes, protecting your brand’s identity has become more challenging than ever. Malicious actors regularly build lookalike websites, complete with official logos and spoofed domains, to try to dupe customers and employees. These kinds of phishing attacks can damage your reputation, erode customer trust, or even result in data breaches.
In March 2023 we introduced Cloudflare’s Brand and Phishing Protection suite, beginning with Brand Domain Name Alerts. This tool recognizes so-called “confusable” domains (which can be nearly indistinguishable from their authentic counterparts) by sifting through the trillions of DNS requests passing through Cloudflare’s DNS resolver, 1.1.1.1. This helps brands and organizations stay ahead of malicious actors by spotting suspicious domains as soon as they appear in the wild.
Today we are excited to expand our Brand Protection toolkit with the addition of Logo Matching. Logo Matching is a powerful tool that allows brands to detect unauthorized logo usage: if Cloudflare detects your logo on an unauthorized site, you receive an immediate notification.
The new Logo Matching feature is a direct result of a frequent request from our users. Phishing websites often use official brand logos as part of their facade. In Continue reading
Shaping the future: Cloudflare’s service partner strategy

Introduction and partner landscape
Cloudflare’s global network spans over 310 cities in more than 120 countries, and interconnects with 13,000 networks globally, including major ISPs, cloud services, and enterprises. This network serves as a globally distributed foundation from which Cloudflare offers a broad product portfolio spanning everything from core Internet services like security, performance, and reliability — to web development, AI, corporate access management, creative products, and more.
The diversity of our products is reflected in our millions of customers, who span a dizzying array of industries and institutions in nearly every country around the world. This incredible diversity has meant a lot of specialisation, as Cloudflare’s adaptable product suite is fitted for each use case. Many customers are keen to have a partner to help them ensure they are getting everything they can out of Cloudflare. And they’d like to do it in the language of their choice, with partners who are familiar with the industries and regions they operate in.
This is why Cloudflare has for many years invested in our Partner Services programs, and has made a concerted effort to scout and partner with the world’s leading service providers who can deliver Cloudflare solutions to the Continue reading
Enhancing Zaraz support: introducing certified developers
Setting up Cloudflare Zaraz on your website is a great way to load third-party tools and scripts, like analytics or conversion pixels, while keeping things secure and performant. The process can be a breeze if all you need is just to add a few tools to your website, but If your setup is complex and requires using click listeners, advanced triggers and variables, or, if you’re migrating a substantial container from Google Tag Manager, it can be quite an undertaking. We want to make sure customers going through this process receive all the support they need.
Historically, we've provided hands-on support and maintenance for Zaraz customers, helping them navigate the intricacies of this powerful tool. However, as Zaraz's popularity continues to surge, providing one-on-one support has become increasingly impractical.
Companies usually rely on agencies to manage their tags and marketing campaigns. These agencies often have specialized knowledge, can handle diverse client needs efficiently, scale resources as required, and may offer cost advantages compared to maintaining an in-house team. That's why we're thrilled to announce the launch of the first round of certified Zaraz developers, aligning with the way other Tag Management software works. Our certified developers have undergone an intensive Continue reading
A look at Internet traffic trends during Super Bowl LVIII

After winning Super Bowl LVII in 2023, the Kansas City Chiefs entered Super Bowl LVIII with an opportunity to pull off back-to-back wins, a feat last achieved by the New England Patriots two decades earlier, in 2003 and 2004. They faced the San Francisco 49ers, five-time Super Bowl champions, although their last win was nearly three decades ago, in 1995. The game started slowly, remaining scoreless until the start of the second quarter, after which both teams traded the lead until a tie score at the end of the game made it only the second Super Bowl to go into overtime. And if you weren’t watching it for the football, the advertisements certainly didn’t disappoint. And if you weren’t watching it for the football or the advertisements, but instead were waiting to see how many times CBS cut away to a shot of Taylor Swift during the game, the answer is… 16. (By my count, at least.)
In this blog post, we will explore which Super Bowl advertisements drove the largest spikes in traffic, as well as examine how traffic to food delivery services, social media, sports betting, and video platform websites and applications changed during the game. In Continue reading
Cloudflare defeats patent troll Sable at trial
For almost seven years, Cloudflare has been fighting against patent trolls. We’ve been doing this successfully through the efforts of our own legal team, external counsel, and the extraordinary efforts of people on the Internet looking for prior art (and getting rewarded for it) through our Project Jengo.
While we refuse to pay trolls for their meritless claims, we’ve been happy to award prizes to Project Jengo participants who help stop the trolls through prior art that invalidates their patents or claims. Project Jengo participants helped us in the past roundly beat the patent troll Blackbird (who subsequently went out of business).
Today, we’re back to talk about yet another win thanks to a lot of work by us, our external counsel, and Project Jengo participants.
Sable
Last Thursday, on a clear, sunny morning in Waco, Texas, a jury returned a verdict after less than two hours of deliberation. The jury found that Cloudflare did not infringe the patent asserted against Cloudflare by patent trolls Sable IP and Sable Networks.
And while that would have been enough to decide the case by itself, the jury went further and found that Sable’s old and broadly-written patent claim was invalid and never Continue reading
connect() – why are you so slow?
It is no secret that Cloudflare is encouraging companies to deprecate their use of IPv4 addresses and move to IPv6 addresses. We have a couple articles on the subject from this year:
- Amazon’s $2bn IPv4 tax – and how you can avoid paying it
- Using DNS to estimate worldwide state of IPv6 adoption
And many more in our catalog. To help with this, we spent time this last year investigating and implementing infrastructure to reduce our internal and egress use of IPv4 addresses. We prefer to re-allocate our addresses than to purchase more due to increasing costs. And in this effort we discovered that our cache service is one of our bigger consumers of IPv4 addresses. Before we remove IPv4 addresses for our cache services, we first need to understand how cache works at Cloudflare.
How does cache work at Cloudflare?
Describing the full scope of the architecture is out of scope of this article, however, we can provide a basic outline:
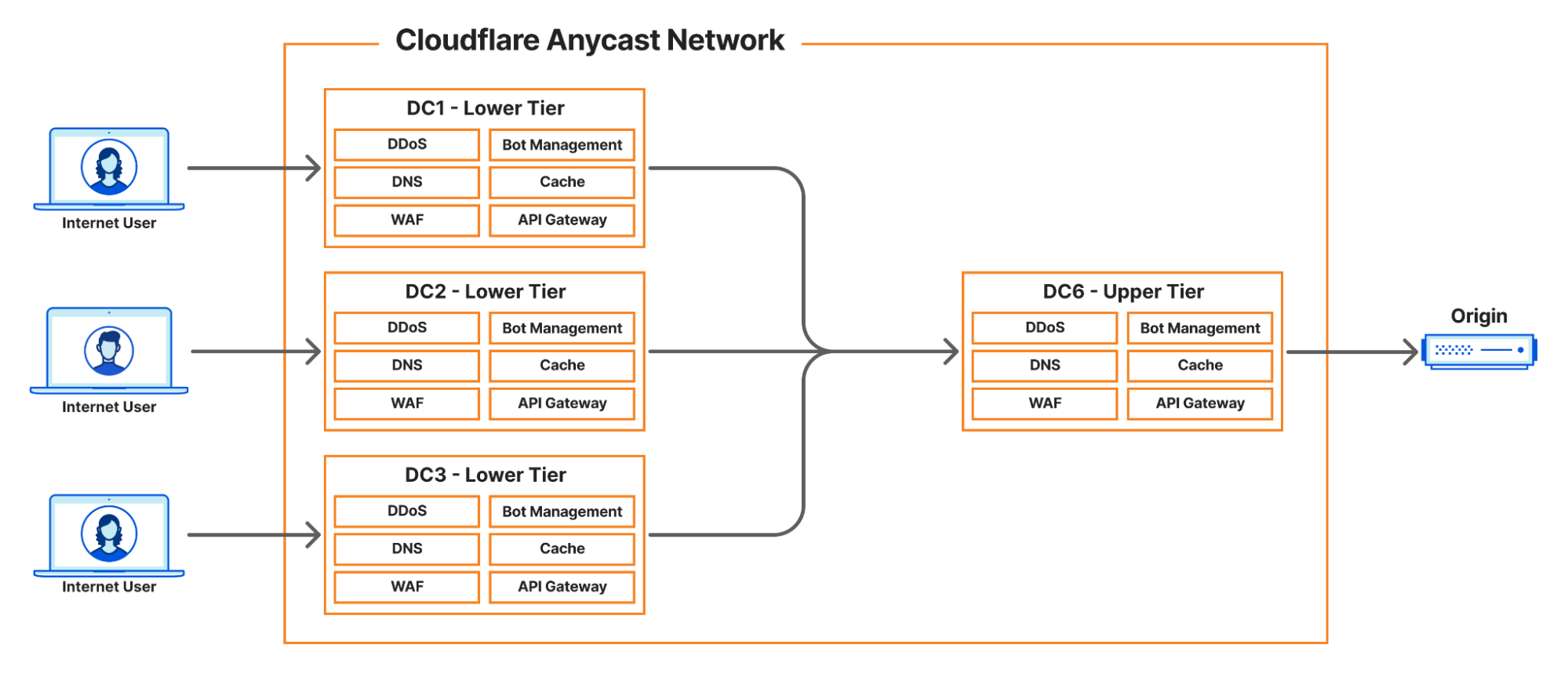
- Internet User makes a request to pull an asset
- Cloudflare infrastructure routes that request to a handler
- Handler machine returns cached asset, or if miss
- Handler machine reaches to origin server (owned by a customer) to pull the Continue reading
Fulfilling the promise of single-vendor SASE through network modernization
As more organizations collectively progress toward adopting a SASE architecture, it has become clear that the traditional SASE market definition (SSE + SD-WAN) is not enough. It forces some teams to work with multiple vendors to address their specific needs, introducing performance and security tradeoffs. More worrisome, it draws focus more to a checklist of services than a vendor’s underlying architecture. Even the most advanced individual security services or traffic on-ramps don’t matter if organizations ultimately send their traffic through a fragmented, flawed network.
Single-vendor SASE is a critical trend to converge disparate security and networking technologies, yet enterprise "any-to-any connectivity" needs true network modernization for SASE to work for all teams. Over the past few years, Cloudflare has launched capabilities to help organizations modernize their networks as they navigate their short- and long-term roadmaps of SASE use cases. We’ve helped simplify SASE implementation, regardless of the team leading the initiative.
Announcing (even more!) flexible on-ramps for single-vendor SASE
Today, we are announcing a series of updates to our SASE platform, Cloudflare One, that further the promise of a single-vendor SASE architecture. Through these new capabilities, Cloudflare makes SASE networking more flexible and accessible for Continue reading
Adding new LLMs, text classification and code generation models to the Workers AI catalog

Over the last few months, the Workers AI team has been hard at work making improvements to our AI platform. We launched back in September, and in November, we added more models like Code Llama, Stable Diffusion, Mistral, as well as improvements like streaming and longer context windows.
Today, we’re excited to announce the release of eight new models.
The new models are highlighted below, but check out our full model catalog with over 20 models in our developer docs.
Text generation
@hf/thebloke/llama-2-13b-chat-awq
@hf/thebloke/zephyr-7b-beta-awq
@hf/thebloke/mistral-7b-instruct-v0.1-awq
@hf/thebloke/openhermes-2.5-mistral-7b-awq
@hf/thebloke/neural-chat-7b-v3-1-awq
@hf/thebloke/llamaguard-7b-awq
Code generation
@hf/thebloke/deepseek-coder-6.7b-base-awq
@hf/thebloke/deepseek-coder-6.7b-instruct-awq
Bringing you the best of open source
Our mission is to support a wide array of open source models and tasks. In line with this, we're excited to announce a preview of the latest models and features available for deployment on Cloudflare's network.
One of the standout models is deep-seek-coder-6.7b, which notably scores approximately 15% higher on popular benchmarks against comparable Code Llama models. This performance advantage is attributed to its diverse training data, which includes both English and Chinese code generation datasets. In addition, the openhermes-2.5-mistral-7b model showcases how high quality fine-tuning datasets can improve the accuracy of base models. Continue reading
Thanksgiving 2023 security incident
On Thanksgiving Day, November 23, 2023, Cloudflare detected a threat actor on our self-hosted Atlassian server. Our security team immediately began an investigation, cut off the threat actor’s access, and on Sunday, November 26, we brought in CrowdStrike’s Forensic team to perform their own independent analysis.
Yesterday, CrowdStrike completed its investigation, and we are publishing this blog post to talk about the details of this security incident.
We want to emphasize to our customers that no Cloudflare customer data or systems were impacted by this event. Because of our access controls, firewall rules, and use of hard security keys enforced using our own Zero Trust tools, the threat actor’s ability to move laterally was limited. No services were implicated, and no changes were made to our global network systems or configuration. This is the promise of a Zero Trust architecture: it’s like bulkheads in a ship where a compromise in one system is limited from compromising the whole organization.
From November 14 to 17, a threat actor did reconnaissance and then accessed our internal wiki (which uses Atlassian Confluence) and our bug database (Atlassian Jira). On November 20 and 21, we saw additional access indicating they may have come back Continue reading
LangChain Support for Workers AI, Vectorize and D1
During Developer Week, we announced LangChain support for Cloudflare Workers. Langchain is an open-source framework that allows developers to create powerful AI workflows by combining different models, providers, and plugins using a declarative API — and it dovetails perfectly with Workers for creating full stack, AI-powered applications.
Since then, we’ve been working with the LangChain team on deeper integration of many tools across Cloudflare’s developer platform and are excited to share what we’ve been up to.
Today, we’re announcing five new key integrations with LangChain:
- Workers AI Chat Models: This allows you to use Workers AI text generation to power your chat model within your LangChain.js application.
- Workers AI Instruct Models: This allows you to use Workers AI models fine-tuned for instruct use-cases, such as Mistral and CodeLlama, inside your Langchain.js application.
- Text Embeddings Models: If you’re working with text embeddings, you can now use Workers AI text embeddings with LangChain.js.
- Vectorize Vector Store: When working with a Vector database and LangChain.js, you now have the option of using Vectorize, Cloudflare’s powerful vector database.
- Cloudflare D1-Backed Chat Memory: For longer-term persistence across chat sessions, you can swap out LangChain’s default Continue reading
Cyber attacks targeting Jewish and Holocaust educational websites surge by 872% in 2023

Tomorrow is the International Holocaust Remembrance Day, a mournful occasion to remember those who perished at the hands of the Nazis and their collaborators. The Holocaust, a catastrophic event in human history, resulted in the extermination of one-third of the Jewish population in Europe — totaling six million Jews during the Second World War. It also claimed the lives of countless others from minority and disability groups targeted under the Nazis' brutal regime of intolerance.
At Cloudflare, through Project Galileo, we are committed to safeguarding Jewish and Holocaust educational websites. This initiative offers complimentary protection to vulnerable groups worldwide. You can apply for the project using this form.
Combating antisemitism with education and cyber defense
Today more than ever, it’s important to ensure educational websites about the Holocaust are protected and available. Education about the Holocaust helps communities understand the dangers of prejudice and dehumanization, and can play an important role in combating antisemitism. As only 13 countries worldwide have mandated Holocaust education, publicly available resources play an important role in ensuring access to information.
According to the Anti-Defamation League, over 1 billion people globally are reported to hold antisemitic attitudes. In the United States, the Continue reading
Reflecting on the GDPR to celebrate Privacy Day 2024
Just in time for Data Privacy Day 2024 on January 28, the EU Commission is calling for evidence to understand how the EU’s General Data Protection Regulation (GDPR) has been functioning now that we’re nearing the 6th anniversary of the regulation coming into force.
We’re so glad they asked, because we have some thoughts. And what better way to celebrate privacy day than by discussing whether the application of the GDPR has actually done anything to improve people’s privacy?
The answer is, mostly yes, but in a couple of significant ways – no.
Overall, the GDPR is rightly seen as the global gold standard for privacy protection. It has served as a model for what data protection practices should look like globally, it enshrines data subject rights that have been copied across jurisdictions, and when it took effect, it created a standard for the kinds of privacy protections people worldwide should be able to expect and demand from the entities that handle their personal data. On balance, the GDPR has definitely moved the needle in the right direction for giving people more control over their personal data and in protecting their privacy.
In a couple of key areas, however, we Continue reading
Introducing Foundations – our open source Rust service foundation library
In this blog post, we're excited to present Foundations, our foundational library for Rust services, now released as open source on GitHub. Foundations is a foundational Rust library, designed to help scale programs for distributed, production-grade systems. It enables engineers to concentrate on the core business logic of their services, rather than the intricacies of production operation setups.
Originally developed as part of our Oxy proxy framework, Foundations has evolved to serve a wider range of applications. For those interested in exploring its technical capabilities, we recommend consulting the library’s API documentation. Additionally, this post will cover the motivations behind Foundations' creation and provide a concise summary of its key features. Stay with us to learn more about how Foundations can support your Rust projects.
What is Foundations?
In software development, seemingly minor tasks can become complex when scaled up. This complexity is particularly evident when comparing the deployment of services on server hardware globally to running a program on a personal laptop.
The key question is: what fundamentally changes when transitioning from a simple laptop-based prototype to a full-fledged service in a production environment? Through our experience in developing numerous services, we've identified several critical differences:
- Observability: Continue reading