Intel Offloads Wind River to Investment Firm TPG
 The deal ends Intel’s near decade of ownership of Wind River. The embedded software firm will keep its existing management team when it's independent.
The deal ends Intel’s near decade of ownership of Wind River. The embedded software firm will keep its existing management team when it's independent.
 The deal ends Intel’s near decade of ownership of Wind River. The embedded software firm will keep its existing management team when it's independent.
The deal ends Intel’s near decade of ownership of Wind River. The embedded software firm will keep its existing management team when it's independent.
As I informed our community in my last note, we launched the Open Call for CEO Candidates on Friday, 9 March 2018.
The deadline for applications is 23:59 UTC on Friday, 6 April 2018
This means that potential candidates interested in applying still have a few more days to do so. Candidates can apply for the position by visiting the Perrett Laver (our search firm for this process) web site using the following link:
https://candidates.perrettlaver.com/vacancies/726/ceo/
While the Candidate Pack (information about the CEO position) has been available for download on the link above during the whole open call, we have received input from our community asking us to make the Candidate Pack available also on a regular URL outside the search firm’s portal. Accordingly, for your convenience, we have now made it available on the following link as well:
https://www.internetsociety.org/wp-content/uploads/2018/04/Internet-Society-CEO-Succession.pdf
Please, distribute this call to potential candidates who may be interested so that they can apply before the upcoming deadline.
The ongoing open call for candidates will result in a long list of candidates. Taking the long list as a starting point, the whole board (at this point the search committee has already done Continue reading
 The platform is increasingly popping up in conversations tied to the orchestration and management of containers in a production environment.
The platform is increasingly popping up in conversations tied to the orchestration and management of containers in a production environment.
 A big driver for using next-generation technologies was improved capabilities to configure, troubleshoot, and measure data center networks.
A big driver for using next-generation technologies was improved capabilities to configure, troubleshoot, and measure data center networks.
 Mosaic NetworX integrated Connected2Fiber’s connected world platform with its Salesforce instance to more effectively design and sell its SD-WAN service.
Mosaic NetworX integrated Connected2Fiber’s connected world platform with its Salesforce instance to more effectively design and sell its SD-WAN service.
 Juniper Networks security team wants to unify threat detection, automated enforcement, and mitigation in a unified platform and integrate with other technology vendors to support non-Juniper gear.
Juniper Networks security team wants to unify threat detection, automated enforcement, and mitigation in a unified platform and integrate with other technology vendors to support non-Juniper gear.
Ian Buck doesn’t just run the Tesla accelerated computing business at Nvidia, which is one of the company’s fastest-growing and most profitable products in its twenty five year history. The work that Buck and other researchers started at Stanford University in 2000 and then continued at Nvidia helped to transform a graphics card shader into a parallel compute engine that is helping to solve some of the world’s toughest simulation and machine learning problems.
The annual GPU Technology Conference was held by Nvidia last week, and we sat down and had a chat with Buck about a bunch of things …
The Buck Stops – And Starts – Here For GPU Compute was written by Timothy Prickett Morgan at The Next Platform.
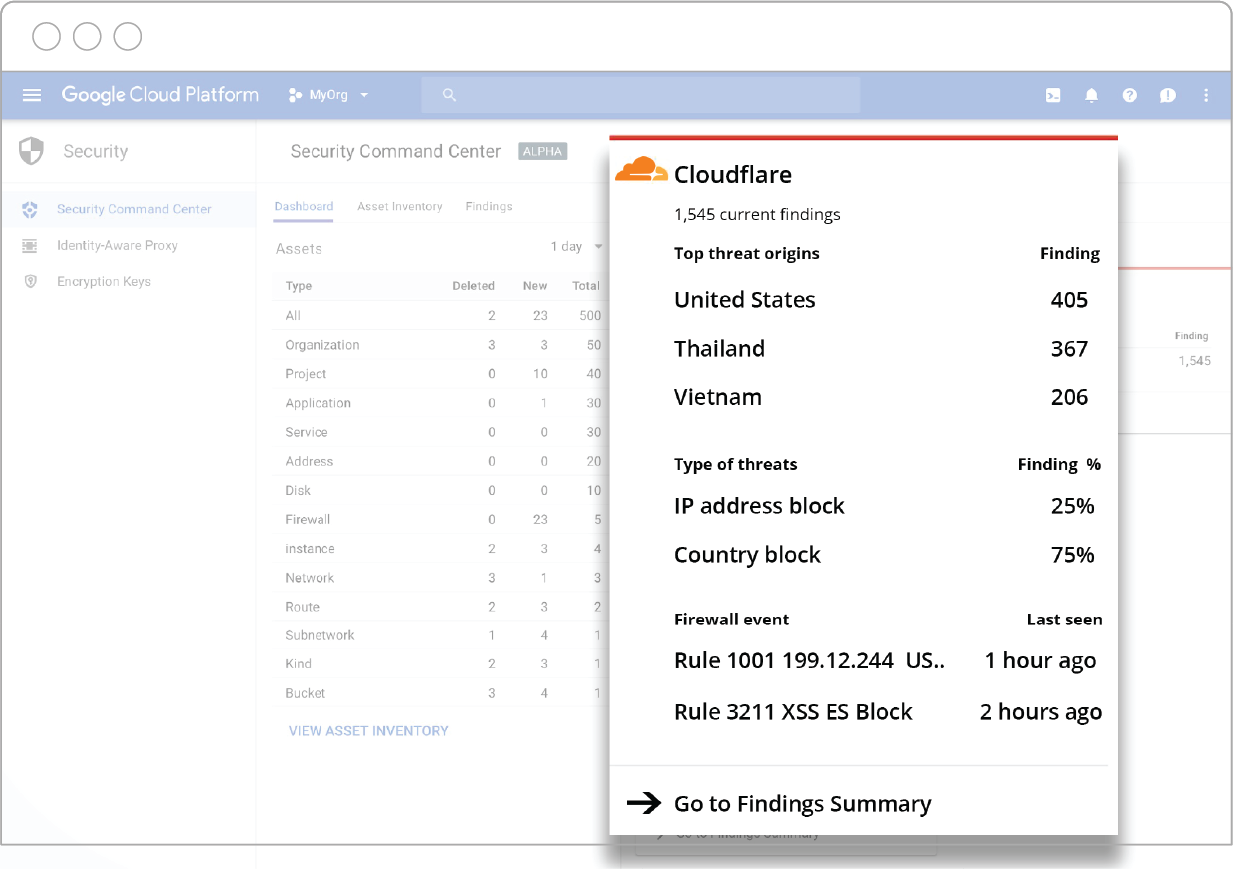
How great would it be to have a dashboard with a holistic view of threats, malicious server activity, vulnerabilities, sensitive data access levels and a daily scan of resources across all of your applications and services? Now you can.
Cloudflare is thrilled to announce its integration with Cloud Security Command Center (Cloud SCC) for Google Cloud Platform: A security and data risk platform helping enterprises gather data, identify threats, and act on them before they result in business damage or loss.
The advantage of the Cloud SCC solution is that it surfaces insights from both the Google Cloud Platform, as well as Cloudflare’s edge, in a unified dashboard.
Through Cloudflare’s API endpoints, data is pushed to Google’s Cloud SCC dashboard and domain name information mapped to the appropriate Google Cloud asset. Cloudflare’s branded card in the Cloud SCC dashboard is automatically populated with a summary of top theat origins, top types of threats, and latest Web Application Firewall (WAF) events.
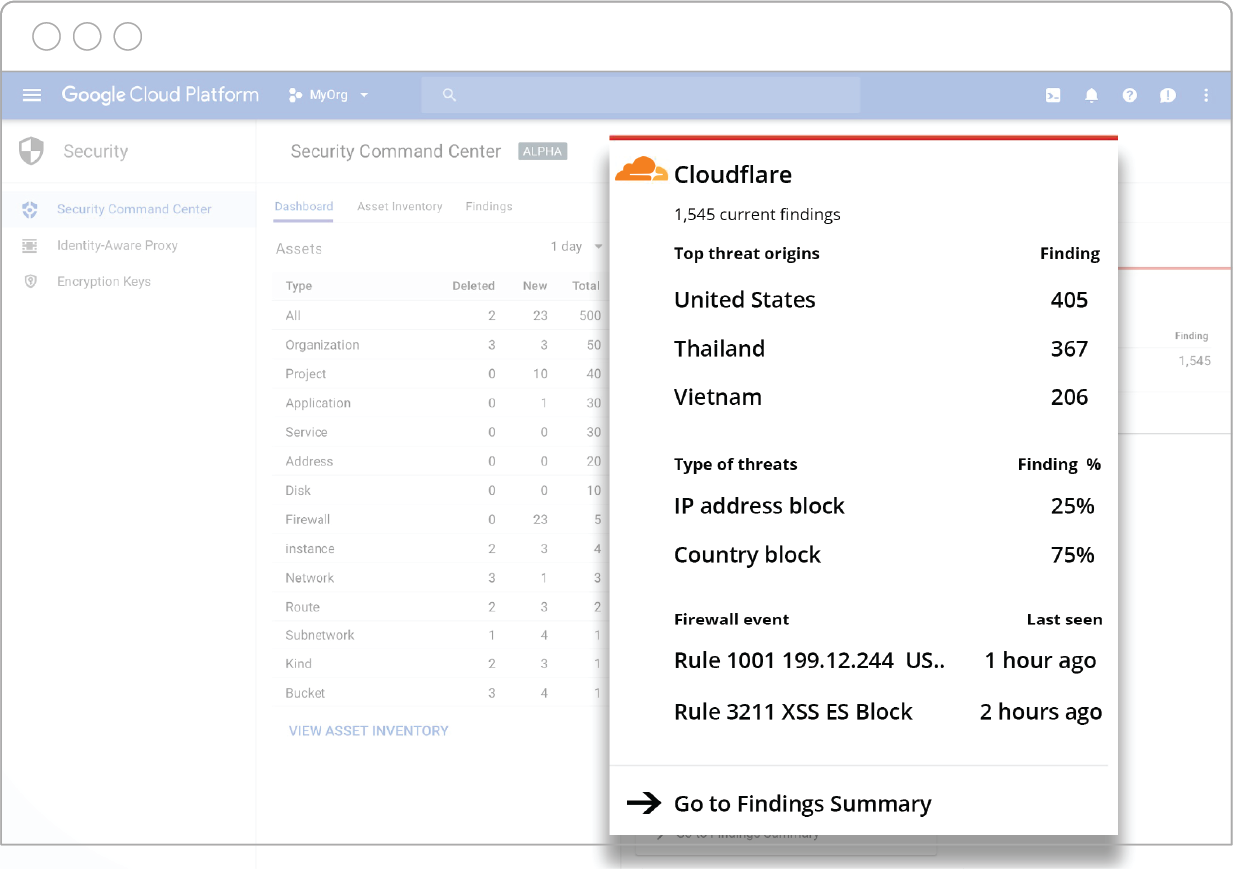
To view a full list of Cloudflare events, click on the Cloudflare card in Cloud SCC and it will take you to a “Cloudflare Findings” page. From there, you can Continue reading
 OpenShift, OpenStack, and Ansible were key drivers for 2018 results, with the impending acquisition of CoreOS set to bolster its container and Kubernetes position moving forward.
OpenShift, OpenStack, and Ansible were key drivers for 2018 results, with the impending acquisition of CoreOS set to bolster its container and Kubernetes position moving forward.
baselineCreate(name,window,sensitivity,repeat);Where:
var status = baselineCheck(name,value);Where:
VMware Cloud on AWS is an on-demand service that enables you to run applications across vSphere-based cloud environments with access to a broad range of AWS services. Powered by VMware Cloud Foundation, this service integrates vSphere, vSAN and NSX along with VMware vCenter management, and is optimized to run on dedicated, elastic, bare-metal AWS infrastructure. With this service, IT teams can manage their cloud-based resources with familiar VMware tools. This course is 2 hours and 25 minutes long and taught by Joseph Holbrook.

Why You Should Watch:
VMWare Cloud on AWS allows you take advantage of what you already know and have in your existing infrastructure. Your existing skills, investment in training, operational practices, and investment in software licenses remain relevant and applicable when you move to the public cloud. As part of that move you can forget about building & running data centers, modernizing hardware, and scaling to meet transient or short-term demand. You can also take advantage of a long list of AWS compute, database, analytics, IoT, AI, security, mobile, deployment and application services.
What You’ll Learn:
This course covers the VMware Cloud on AWS service overview, Prereqs, Licensing, SDDC, Hybrid Linked Mode, NSX, Compute Options, Connectivity Continue reading

Welcome to another entry in the Getting Started series. The API (Application Programming Interface) or, as I like to refer to it, the Magical Land of Automation Information, can be used in quite a few ways. In this Getting Started post, we will be discussing Red Hat Ansible Tower’s API and how you can use it to extract information to utilize in your playbooks and other tools.
The idea for this blog post came about when David Federlein was developing a new Ansible Tower demo and presentation. I will be making references to that codebase, which you can follow along with throughout this post. Please note that this demo utilizes Vagrant and VirtualBox so you’ll need to have those applications installed if you would like to stand up the demo yourself.
Ansible Tower’s API is fully browsable. You can navigate to your instance’s REST API by typing this into your browser: http://<Tower server name>/api/v2. Once there, you can click any of the listed links and view the current objects loaded for that particular attribute in Ansible Tower. Everything you can do in Ansible Tower's UI can be done from the API; you can also use it Continue reading
Bioinspired computing is nothing new but with the rise in mainstream interest in machine learning, these architectures and software frameworks are seeing fresh light. This is prompting a new wave of young companies that are cropping up to provide hardware, software, and management tools—something that has also spurred a new era of thinking about AI problems.
We most often think of these innovations happening at the server and datacenter level but more algorithmic work is being done (to suit better embedded hardware) to deploy comprehensive models on mobile devices that allow for long-term learning on single instances of object recognition …
Momentum for Bioinspired GPU Computing at the Edge was written by Nicole Hemsoth at The Next Platform.
Last month in Kathmandu, Nepal, 750 delegates participated in APRICOT 2018 – Asia-Pacific’s largest Internet conference. It was led by Internet Exchange Nepal (npIX) with support from several organizations including the Internet Society (ISOC) Nepal Chapter.
The Internet Society, through its Asia-Pacific Bureau, is a long-term partner of the APRICOT conferences, sponsoring a competitive fellowship programme, as part of the Internet Society’s mission to support capacity building in developing countries. Read more about our fellows at APRICOT 2018:
Team ISOC @ APRICOT 2018 comprised of staff from Regional Bureaus and Internet Technology. This included Andrei Robachevsky, Aftab Siddiqui, Rajnesh Singh, Salam Yamout, and myself.
In line with the Internet Society’s 2018 Action Plan, our core message at APRICOT 2018 was to strengthen the global Internet routing system and mitigate many of the risks facing the Internet’s core today. This includes route hijacking, traffic detouring, and address spoofing – which is a root cause of Distributed Denial of Service (DDOS) attacks. We promoted the Mutually Agreed Norms for Routing Security (MANRS), a set of recommendations addressing these risks, already adopted by some network operators.
Team ISOC took on a wide variety of roles Continue reading