ជំរាបសួរ! – Phnom Penh: Cloudflare’s 122nd Data Center
Cloudflare is excited to turn up our newest data center in Phnom Penh, Cambodia, making over 7 million Internet properties even faster. This is our 122nd data center globally, and our 41st data center in Asia. By the end of 2018, we expect that 95% of the world's population will live in a country with a Cloudflare data center, as we grow our global network to span 200 cities.
Cambodian Internet
Home to over 16 million people, Cambodia has a relatively low base of Internet penetration (~25%) today, but is seeing an increasing number of Internet users coming online. For perspective, Cambodia has approximately the same number of Internet users as Lebanon (where we just turned up our 121st data center!) or Singapore (from where we used to serve a portion of Cambodian visitors).
In the coming weeks, we’ll further optimize our routing for Cloudflare customers and expect to see a growing number of ISPs pick up our customers’ traffic on a low latency path.
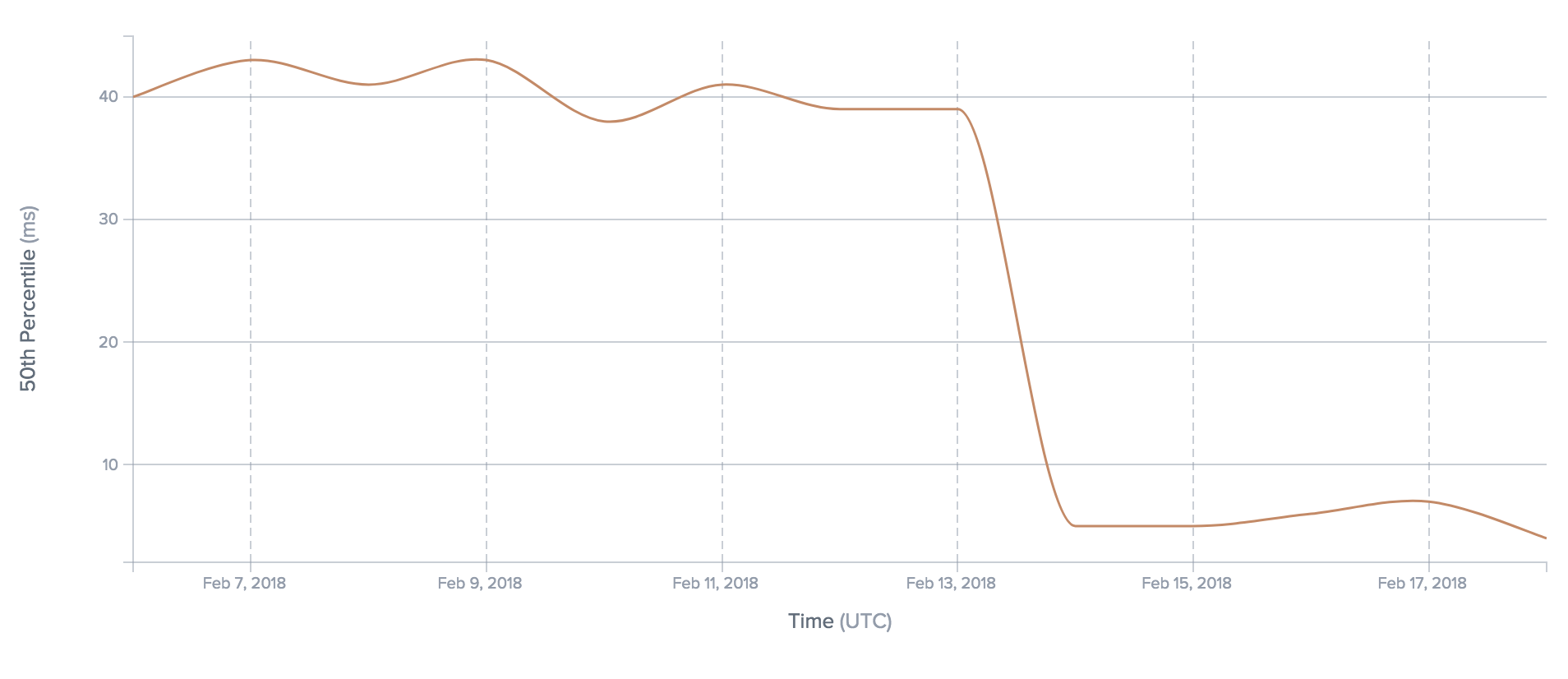
Latency from a Cambodian ISP (SINET) to Cloudflare customers decreases 10x
Coming up next
Next up, in fact, thousands of feet further up, we head to the mountains for Cloudflare’s 123rd data center. Following Continue reading
Using Go as a scripting language in Linux
At Cloudflare we like Go. We use it in many in-house software projects as well as parts of bigger pipeline systems. But can we take Go to the next level and use it as a scripting language for our favourite operating system, Linux?
gopher image CC BY 3.0 Renee French
Tux image CC0 BY OpenClipart-Vectors
Why consider Go as a scripting language
Short answer: why not? Go is relatively easy to learn, not too verbose and there is a huge ecosystem of libraries which can be reused to avoid writing all the code from scratch. Some other potential advantages it might bring:
- Go-based build system for your Go project:
go buildcommand is mostly suitable for small, self-contained projects. More complex projects usually adopt some build system/set of scripts. Why not have these scripts written in Go then as well? - Easy non-privileged package management out of the box: if you want to use a third-party library in your script, you can simply
go getit. And because the code will be installed in yourGOPATH, getting a third-party library does not require administrative privileges on the system (unlike some other scripting languages). This is especially useful in large Continue reading
리눅스에서 Go를 스크립트 언어로 사용하기
This is a Korean translation of a prior post by Ignat Korchagin.
Cloudflare에서는 Go를 좋아합니다. Go는 많은 내부 소프트웨어 프로젝트와 거대한 파이프라인 시스템의 일부로도 사용되고 있습니다. 하지만 Go를 한단계 더 끌어 올려서 우리가 선호하는 운영체제인 리눅스의 스크립트 언어로 사용할 수 있을까요?

gopher image CC BY 3.0 Renee French | Tux image CC0 BY OpenClipart-Vectors
Go를 왜 스크립트 언어로 고려하는가
간단한 답은: 왜 안되나요? Go는 비교적 쉽게 배울 수 있고 아주 복잡하지도 않고, 코드를 처음부터 작성해야 하는 일을 피하기 위해 재사용 가능한 라이브러리의 거대한 에코시스템이 있습니다. 추가로 다음과 같은 잠재적인 장점이 있습니다:
- 여러분의 Go 프로젝트를 위한 Go 기반 빌드 시스템:
go build명령은 대부분의 소규모이며 독립적인 프로젝트에 적합합니다. 더 복잡한 프로젝트는 대부분 별도의 빌드 시스템/스크립트 세트를 채용하고 있습니다. 이런 스크립트도 Go로 작성 가능하지 않을까요? - 바로 이용 가능한 별도 권한 없는 패키지 관리: 여러분의 프로그램에서 서드 파티 라이브러리를 사용하고 싶다면 단순히
go get을 사용하면 됩니다. 그리고 이 코드가 여러분의GOPATH에 설치되므로, 서드파티 라이브러리를 받는 것은 시스템의 별도 운영 권한을 필요로 하지 않습니다(다른 일부 스크립트 언어와 달리). 이것은 대규모의 기업 환경에서 특히 유용합니다. - 초기 단계 프로젝트를 위한 빠른 코드 프로토타이핑: 최초로 돌아가는 코드를 작성할 때 컴파일 되기 위해서 많은 편집을 해야 하고 "편집->빌드->체크" 사이클을 위해 많은 키보드 입력을 Continue reading
Keeping our users safe
To everyone in Cloudflare, account security is one of our most important tasks. We recognize that to every customer on our platform, we are critical infrastructure. We also know that the simplest attacks often lead to the most devastating of outcomes. Most people think that if they are going to get hacked it will be by some clever ”zero day”. The reality couldn’t be farther from the truth.
Attackers are smart and they have realized that even in 2018, the human is still the weakest link in the chain. The 2017 Verizon breach report identified that 81% of hacking related breaches occurred as a result of weak credentials or credential theft, an increase from the 63% reported in 2016’s breach report.
Source: Verizon 2017 data breach report
Your credentials are as important as your house or car keys. If someone copies or steals them, the repercussions can be catastrophic. If you suspect someone has access to your house keys you change your locks. If you aren’t fast enough, someone might break in.
Likewise if you realize that someone might have access to your password, the remedy is to change it. Too often, as with house keys, we are slow to Continue reading
Cloudflare ♥ Open Source: upgrade to Pro Plan on the house

Happy Valentine's Day, Internet!
There’s a special place in our heart for all the open source projects that support the Internet and improve the lives of everyone in the developer community, and today seems like an appropriate time to express the gratitude we have for the non-profit / volunteer-run projects that hold everything together.
Cloudflare uses a lot of open source software and also contributes to open source. Informally, Cloudflare has already been upgrading the plans of certain eligible open source projects that have reached out to us or that we have interfaced with. Here are some of the projects whose landing pages are already protected by Cloudflare.

A subset of open source projects on Cloudflare. See more >>
To really pay the goodwill forward, we want to make this opportunity common knowledge in the developer community. In 2018, we intend to provide free Cloudflare Pro Plan upgrades to eligible open source projects (subject to a case-by-case evaluation) that:
- provide engineering tools or resources to the developer community; and
- are volunteer-run or working on a non-profit basis.
Are you an open source project using @Cloudflare? We want to give you a free Pro Plan to thank you for your work Continue reading
Why I’m helping Cloudflare grow in Asia

I’m excited to announce that I’ve joined Cloudflare as Head of Asia. This is an important time for the company as we continue to grow our presence in the region and build on the successes we’ve already had in our Singapore office. In this new role, I’m eager to grow our brand recognition in Asia and optimize our reach to clients by building up teams and channel partners.
A little about me
I’m a Californian with more than 20 years of experience growing businesses across Asia. I initially came to Asia with the Boston Consulting Group and since then I’ve helped Google and Twitter start and grow their businesses in Singapore and Asia. In many cases throughout my career, I’ve been one of the very first employees (sometimes the first) on the ground in this part of the world. To me, the Asian market presents an often untapped opportunity for companies looking to expand, and it’s a challenge that has appealed to me throughout my career.
 This year's Chinese New Year celebration
This year's Chinese New Year celebration
Why Cloudflare?
I’m driven by opportunities to work with global businesses that drive change and are full of ambitious and passionate people. Cloudflare’s mission is to help build Continue reading
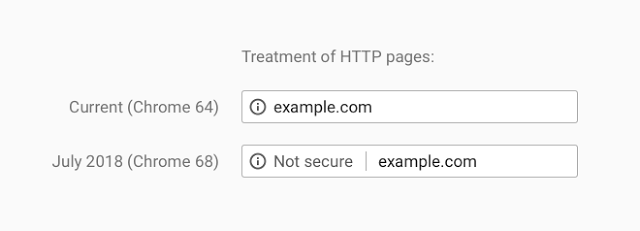
HTTPS or bust: Chrome’s plan to label sites as “Not Secure”

Google just announced that beginning in July 2018, with the release of Chrome 68, web pages loaded without HTTPS will be marked as “not secure”.
More than half of web visitors will soon see this warning when browsing unencrypted HTTP sites, according to data from Cloudflare’s edge that shows 56.62% of desktop requests originate from Chrome. Users presented with this warning will be less likely to interact with these sites or trust their content, so it’s imperative that site operators not yet using HTTPS have a plan to do so by July.
How did we get here (and why)?
To those who have followed the Chrome team’s public statements, this announcement comes as no surprise. Google has been gearing up for this change since 2014, as Chrome boss Parisa Tabriz tweeted and Chris Palmer memorialized in a widely distributed email. While this step is an important and potentially jarring one for users, it’s by no means the last step that Google will take to influence website administrator behavior for the better.
But why are they making this change (now)? Google’s primary motivation for driving HTTPS adoption is simple: a safe browsing experience is good for business. Users that feel Continue reading
Marhaba Beirut! Cloudflare’s 121st location – مرحبا بيروت! موقع “كلاودفلار” ال ١٢١

Lebanon is a historic country, home to two cities among the oldest in the world. There’s a vast mix of influences from the East and West. It’s also the smallest country in continental Asia.

CC-BY-SA Gregor Rom
Lebanon’s connection to the Internet
Lebanon is a little different to most other countries when it comes to the internet, with all connectivity to the outside world flowing via a single network, Ogero. Traffic to Lebanon was previously served from our existing deployments in Marseille and Paris, due to where Ogero connects to the rest of the internet. By deploying locally in Beirut, round-trip latency is cut by around 50 milliseconds. This might seem like almost nothing, but it adds up when you factor in a DNS lookup and 3-way handshake required to open a TCP connection. Internet penetration in Lebanon according to different sources is around 75%, which is quite high. However, the speed available to end users is low, typically in single digit megabits per second.
The Ministry of Telecommunications has an ambitious plan to Continue reading
Bye Bye Blackbird


Courtesty of PublicDomainPictures.net
As we have talked about repeatedly in this blog, we at Cloudflare are not fans of the behavior of patent trolls. They prey upon innovative companies using overly-broad patents in an attempt to bleed settlements out of their targets. When we were first sued by a patent troll called Blackbird Technologies last spring, we decided that we weren’t going along with their game by agreeing to a modest settlement in lieu of going through the considerable effort and expense of litigation. We decided to fight.
We’re happy to report that earlier today, the United States District Court for the Northern District of California dismissed the case that Blackbird brought against Cloudflare. In a two-page order (copied below) Judge Vince Chhabria noted that “[a]bstract ideas are not patentable” and then held that Blackbird’s attempted assertion of the patent “attempts to monopolize the abstract idea of monitoring a preexisting data stream between a server” and is invalid as a matter of law. That means that Blackbird loses no matter what the facts of the case would have been.
The court’s ruling comes in response to a preliminary motion filed by Cloudflare under Section 101 of the U. Continue reading
It’s Hard To Change The Keys To The Internet And It Involves Destroying HSM’s


The root of the DNS tree has been using DNSSEC to protect the zone content since 2010. DNSSEC is simply a mechanism to provide cryptographic signatures alongside DNS records that can be validated, i.e. prove the answer is correct and has not been tampered with. To learn more about why DNSSEC is important, you can read our earlier blog post.
Today, the root zone is signed with a 2048 bit RSA “Trust Anchor” key. This key is used to sign further keys and is used to establish the Chain of trust that exists in the public DNS at the moment.
With access to this root Trust Anchor, it would be possible to re-sign the DNS tree and tamper with the content of DNS records on any domain, implementing a man-in-the-middle DNS attack… without causing recursors and resolvers to consider the data invalid.
As explained in this blog the key is very well protected with eye scanners and fingerprint readers and fire-breathing dragons patrolling the gate (okay, maybe not dragons). Operationally though, the root zone uses two different keys, the mentioned Trust Anchor key (that is called the Key Signing Key or KSK for Continue reading
How we made our page-load optimisations even faster
In 2017 we made two of our web optimisation products - Mirage and Rocket Loader - even faster! Combined, these products speed up around 1.2 billion web-pages a week. The products are both around 5 years old, so there was a big opportunity to update them for the brave new world of highly-tuned browsers, HTTP2 and modern Javascript tooling. We measured a performance boost that, very roughly, will save visitors to sites on our network between 50-700ms. Visitors that see content faster have much higher engagement and lower bounce rates, as shown by studies like Google’s. This really adds up, representing a further saving of 380 years of loading time each year and a staggering 1.03 petabytes of data transfer!

Cycling image Photo by Dimon Blr on Unsplash.
What Mirage and Rocket Loader do
Mirage and Rocket Loader both optimise the loading of a web page by reducing and deferring the number of assets the browser needs to request for it to complete HTML parsing and rendering on screen.
Mirage
Coming soon to a university near you

Attention software engineering students: Cloudflare is coming to the University of Illinois at Urbana-Champaign and the University of Wisconsin–Madison, and we want to meet you! We will be attending UW–Madison’s Career Connection on Wednesday, February 7 and UIUC’s Startup Career Fair on Thursday, February 8. We’ll also be hosting tech talks at UIUC on Friday, February 2 at 6:00pm in 2405 Siebel Center and at UW–Madison on Tuesday, February 6 (time and location coming soon).

Cloudflare staff at YHack 2017. Photo courtesy Andrew Fitch.
Built in Champaign
In early 2016, Cloudflare opened an engineering office in Champaign, IL to build Argo Smart Routing. Champaign's proximity to the University of Illinois, one of the nation's top engineering schools, makes it an attractive place for high-tech companies to set up shop and for talented engineers to call home. Since graduating from UIUC in 2008, I've had opportunities to work on amazing software projects, growing technically and as a leader, all while enjoying the lifestyle benefits of Champaign (15 minute commute, anyone?).
Cloudflare has attended annual recruiting events at UIUC since the Champaign office was opened. This year, we've started to expand our search to other top engineering schools in the midwest. Continue reading
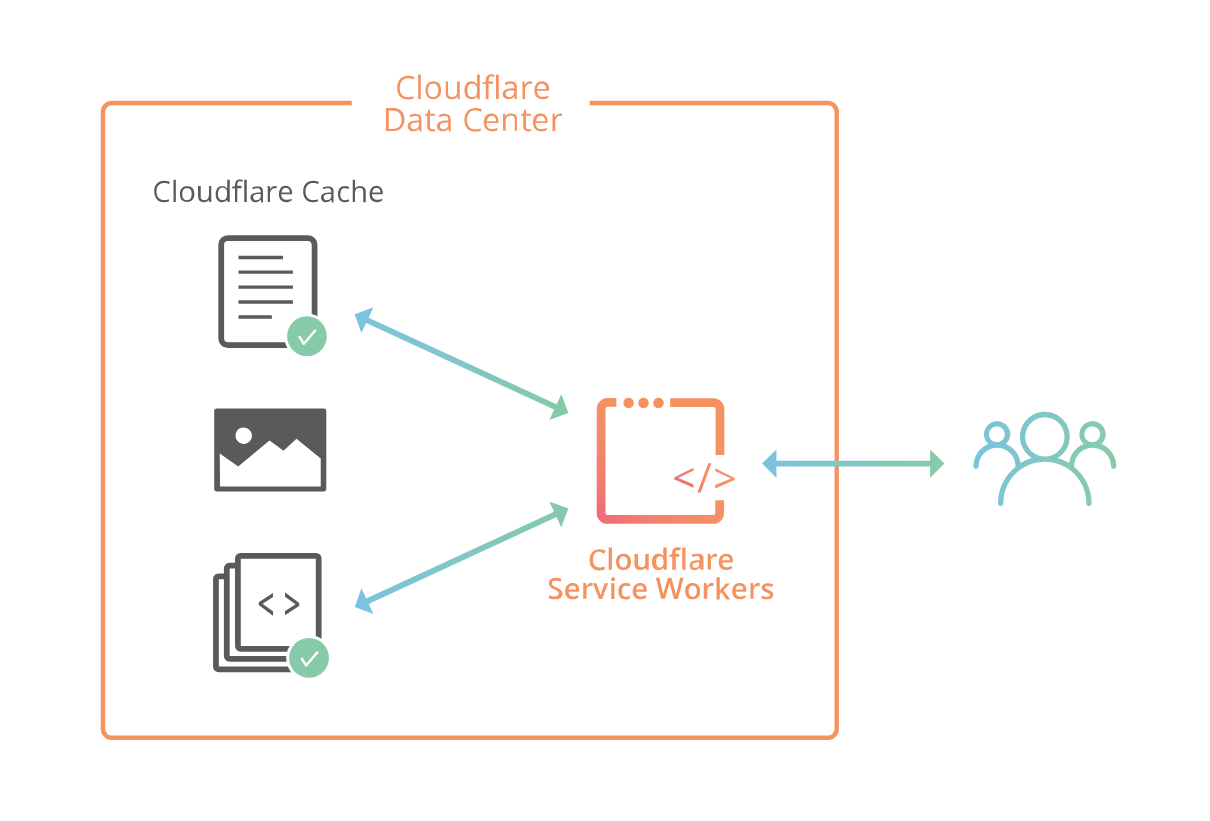
Cloudflare Workers is now on Open Beta
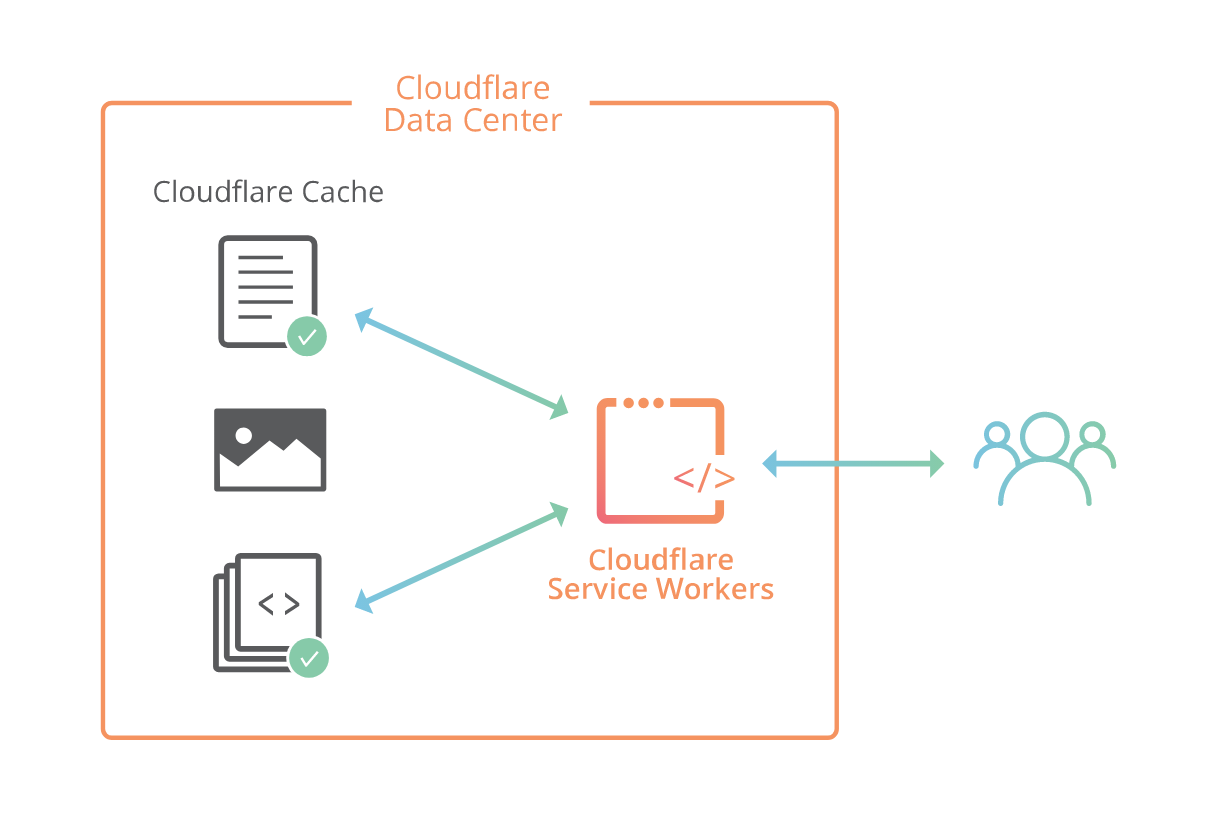
Cloudflare Workers Beta is now open!
Cloudflare Workers lets you run JavaScript on Cloudflare’s edge, deploying globally to over 120+ data centers around the world in less than 30 seconds. Your code can intercept and modify any request made to your website, make outbound requests to any URL on the Internet, and replace much of what you might need to configure your CDN to do today. Even better, it will do this from all our edge locations around the world, closer to many of your users than your origin servers can ever be. You will have a fully functional Turing-complete language in your fingertips which will allow you to build powerful applications on the edge. The only limit is your imagination.
To get started:
- Sign in to your account on cloudflare.com.
- Visit the Workers tab.
- Launch the editor.
- Write some code and save it.
- Go to the routes tab and prescribe on what requests you want to run Workers for
That’s it!
You can start by writing a simple ‘hello world’ script, but chances are that you are going write Workers that are more complicated. You can check out our page with recipes to:
Rust 로 복잡한 매크로를 작성하기: 역폴란드 표기법
This is a Korean translation of a prior post.
(이 글은 제 개인 블로그에 게시된 튜토리얼을 다시 올린 것입니다)
Rust에는 흥미로운 기능이 많지만 그중에도 강력한 매크로 시스템이 있습니다. 불행히도 The Book[1]과 여러가지 튜토리얼을 읽고 나서도 서로 다른 요소의 복잡한 리스트를 처리하는 매크로를 구현하려고 하면 저는 여전히 어떻게 만들어야 하는지를 이해하는데 힘들어 하며, 좀 시간이 지나서 머리속에 불이 켜지는 듯한 느낌이 들면 그제서야 이것저것 매크로를 마구 사용하기 시작 합니다. :) (맞아요, 난-매크로를-써요-왜냐하면-함수나-타입-지정이나-생명주기를-쓰고-싶어하지-않아서 처럼과 같은 이유는 아니지만 다른 사람들이 쓰는걸 봤었고 실제로 유용한 곳이라면 말이죠)
CC BY 2.0 image by Conor Lawless
그래서 이 글에서는 제가 생각하는 그런 매크로를 쓰는 데 필요한 원칙을 설명하고자 합니다. 이 글에서는 The Book의 매크로 섹션을 읽어 보았고 기본적인 매크로 정의와 토큰 타입에 대해 익숙하다고 가정하겠습니다.
이 튜토리얼에서는 역폴란드 표기법 (Reverse Polish Notation, RPN)을 예제로 사용합니다. 충분히 간단하기 때문에 흥미롭기도 하고, 학교에서 이미 배워서 익숙할 지도 모르고요. 하지만 컴파일 시간에 정적으로 구현하기 위해서는 재귀적인 매크로를 사용해야 할 것입니다.
역폴란드 표기법(후위 또는 후치 표기법으로 불리기도 합니다)은 모든 연산에 스택을 사용하므로 연산 대상을 스택에 넣고 [이진] 연산자는 연산 대상 두개를 스택에서 가져와서 결과를 평가하고 다시 스택에 넣습니다. 따라서 다음과 같은 식을 생각해 보면:
2 3 + 4 *
이 식은 다음과 같이 해석됩니다:
Writing complex macros in Rust: Reverse Polish Notation
(This is a crosspost of a tutorial originally published on my personal blog)
Among other interesting features, Rust has a powerful macro system. Unfortunately, even after reading The Book and various tutorials, when it came to trying to implement a macro which involved processing complex lists of different elements, I still struggled to understand how it should be done, and it took some time till I got to that "ding" moment and started misusing macros for everything :) (ok, not everything as in the i-am-using-macros-because-i-dont-want-to-use-functions-and-specify-types-and-lifetimes everything like I've seen some people do, but anywhere it's actually useful)
CC BY 2.0 image by Conor Lawless
So, here is my take on describing the principles behind writing such macros. It assumes you have read the Macros section from The Book and are familiar with basic macros definitions and token types.
I'll take a Reverse Polish Notation as an example for this tutorial. It's interesting because it's simple enough, you might be already familiar with it from school, and yet to implement it statically at compile time, you already need to use a recursive macros approach.
Reverse Polish Notation (also called postfix notation) uses a stack for all its operations, Continue reading
SEO Performance in 2018 Using Cloudflare
For some businesses SEO is a bad word, and for good reason. Google and other search engines keep their algorithms a well-guarded secret making SEO implementation not unlike playing a game where the referee won’t tell you all the rules. While SEO experts exist, the ambiguity around search creates an opening for grandiose claims and misinformation by unscrupulous profiteers claiming expertise.
If you’ve done SEO research, you may have come across an admixture of legitimate SEO practices, outdated optimizations, and misguided advice. You might have read that using the keyword meta tag in your HTML will help your SEO (it won’t), that there’s a specific number of instances a keyword should occur on a webpage (there isn’t), or that buying links will improve your rankings (it likely won’t and will get the site penalized). Let’s sift through the noise and highlight some dos and don’ts for performance-based SEO in 2018.
SEO is dead, long live SEO!
Nearly every year since its inception, SEO is declared dead. It is true that the scope of best practices for search engines has narrowed over the years as search engines have become smarter, and much of the benefit Continue reading
Lessons learned from adapting Site Search 360 for Cloudflare Apps

This is a guest post by David Urbansky, CEO and Co-Founder of SEMKNOX and Site Search 360. David is a search enthusiast having built natural language search experiences for e-commerce sites and recipe search engines.
As a startup founder, there are always key product decisions to be made when Site Search 360, our key product, is embedded in one context versus another. I’d like to share some experiences, choices, and challenges in our process packaging Site Search 360 for Cloudflare Apps.
What is Site Search 360?
Site Search 360 is a search solution for websites. Offering a search bar on a website improves user experience tremendously if the site has more than just a handful of pages. According to a eConsultancy study, up to 30% of web visitors use the search feature on e-commerce sites and searchers sometimes make up 40% of the revenue. Additionally, Nielsen Group found that 51% of people who did not find what they were looking for with the first query, gave up without refining the search - the search had better work very well then.
Why use the Cloudflare App?
Considering these facts, almost every website should have a search feature. However, implementing Continue reading
Large drop in traffic from the Democratic Republic of Congo
It is not uncommon for countries around the world to interrupt Internet access for political reasons or because of social unrest. We've seen this many times in the past (e.g. Gabon, Syria, Togo).
Today, it appears that Internet access in the Democratic Republic of Congo has been greatly curtailed. The BBC reports that Internet access in the capital, Kinshasa was cut on Saturday and iAfrikan reports that the cut is because of anti-Kabila protests.
Our monitoring of traffic from the Democratic Republic of Congo shows a distinct drop off starting around midnight UTC on January 21, 2018. Traffic is down to about 1/3 of its usual level.
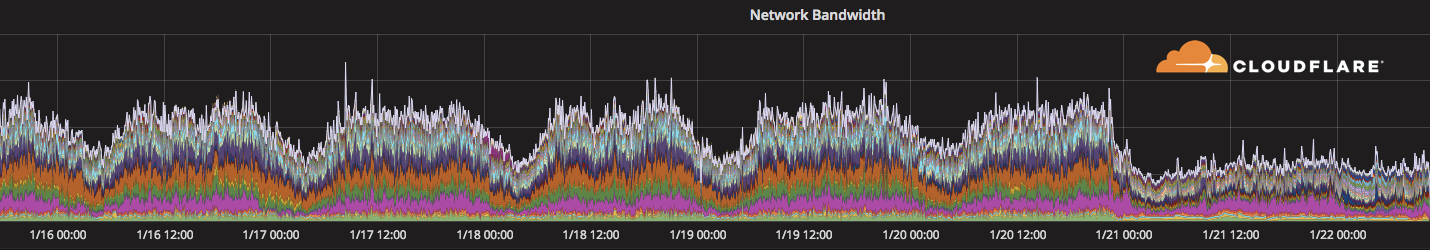
We'll update this blog once we have more information about traffic levels.
Web Cache Deception Attack revisited
In April, we wrote about Web Cache Deception attacks, and how our customers can avoid them using origin configuration.
Read that blog post to learn about how to configure your website, and for those who are not able to do that, how to disable caching for certain URIs to prevent this type of attacks. Since our previous blog post, we have looked for but have not seen any large scale attacks like this in the wild.
Today, we have released a tool to help our customers make sure only assets that should be cached are being cached.
A brief re-introduction to Web Cache Deception attack
Recall that the Web Cache Deception attack happens when an attacker tricks a user into clicking a link in the format of http://www.example.com/newsfeed/foo.jpg, when http://www.example.com/newsfeed is the location of a dynamic script that returns different content for different users. For some website configurations (default in Apache but not in nginx), this would invoke /newsfeed with PATH_INFO set to /foo.jpg. If http://www.example.com/newsfeed/foo.jpg does not return the proper Cache-Control headers to tell a web cache not to cache the content, web caches may decide to cache Continue reading
SYN 패킷 처리 실제
역자주: 이 글은 Marek Majkowski의 https://blog.cloudflare.com/syn-packet-handling-in-the-wild/ 를 번역한 것입니다.
우리 Cloudflare 에서는 실제 인터넷상의 서버 운영 경험이 많습니다. 하지만 이런 흑마술 마스터하기를 게을리하지도 않습니다. 이 블로그에서는 인터넷 프로토콜의 여러 어두운 부분을 다룬 적이 있습니다: understanding FIN-WAIT-2 나 receive buffer tuning과 같은 것들입니다.

CC BY 2.0 image by Isaí Moreno
사람들이 충분히 신경쓰지 않는 주제가 하나 있는데, 바로 SYN 홍수(SYN floods) 입니다. 우리는 리눅스를 사용하고 있는데 리눅스에서 SYN 패킷 처리는 매우 복잡하다는 것을 알게 되었습니다. 이 글에서는 이에 대해 좀 더 알아 보도록 하겠습니다.
두개의 큐의 이야기
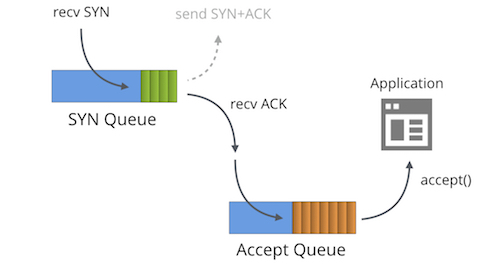
일단 만들어진 소켓에 대해 "LISTENING" TCP 상태에는 두개의 분리된 큐가 존재 합니다:
- SYN 큐
- Accept 큐
일반적으로 이 큐에는 여러가지 다른 이름이 붙어 있는데, "reqsk_queue", "ACK backlog", "listen backlog", "TCP backlog" 등이 있습니다만 혼란을 피하기 위해 위의 이름을 사용하도록 하겠습니다.
SYN 큐
SYN 큐는 수신 SYN 패킷[1] (구체적으로는 struct inet_request_sock)을 저장합니다. 이는 SYN+ACK 패킷을 보내고 타임아웃시에 재시도하는 역할을 합니다. 리눅스에서 재시도 값은 다음과 같이 설정됩니다:
$ sysctl net.ipv4.tcp_synack_retries
net.ipv4.tcp_synack_retries = 5
문서를 보면 다음과 같습니다:
tcp_synack_retries - 정수
수동 TCP 연결 시도에 대해서 SYNACK를 몇번 다시 보낼지를 지정한다.
이 값은 255 이하이어야 한다. 기본값은 5이며, 1초의 초기 RTO값을 감안하면
마지막 재전송은 31초 Continue reading