Google Cloud Adds Compute, Memory-Intensive VMs
The cloud provider also added second-generation Intel Xeon scalable processor virtual machines for...
Kubernetes Adoption Alters Vendor Support Models
Mesosphere's recent name change and operational focus follows similar moves by Docker Inc., Pivotal...
Going Independent
Many people look forward to the day that they can quit the day job and become their own boss. In this episode we chat with Jody Lemoine and Bruno Wollmann, two people who have done just that, to discuss some of the lessons learned as they transitioned into independent self-employment in the networking space.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post Going Independent appeared first on Network Collective.
Key Steps and Pitfalls to Avoid in Cloud Security, with Valtix’s CEO Vishal Jain
Hear from Valtix CEO Vishal Jain and is his take on cloud security today, where it’s going, and...
Preserving Native Cultures: Vote Now for the Internet Society’s Panel for SXSW 2020

What benefits can Internet connectivity bring to Tribal and Indigenous communities – especially when it comes to language and culture preservation? That’s the topic of our panel proposal for South by Southwest (SXSW) 2020: “How Internet Access Can Preserve Native Cultures.”
And we’re excited to announce that you can now vote for it!
SXSW, is an annual conference held in Austin, Texas, USA. The conference’s many events include a music festival, networking opportunities, and panels that focus on technology, governance, film, culture, and music. The panels featured at SXSW live within tracks that range from health and medtech to innovative applications of new technologies. All panels at SXSW are chosen through a public vote so that participants can decide what they want to discuss at the event.
That’s where we need your help!
SXSW is a platform for bringing important policy issues and initiatives to light, which is why we’ve applied. It’s an ideal forum for exposing the impact that technology can have on culture.
If accepted, our panel would discuss specific issues that Tribal and Indigenous areas face when it comes to broadband deployment, the lessons that communities can learn from one another, and how they can Continue reading
Reinventing Your Own STP Wheel…
One of my readers sent me a link to an interesting L2-over-IP "design". Someone tried to connect two data centers with redundant etherip links using home-brewed redundancy mechanism and (surprise, surprise) managed to bring both of them down. The obvious fix: patch the etherip device driver.
I don't know enough about OpenBSD to figure out whether (A) it doesn't have STP at all, (B) STP doesn't work over EtherIP, (C) host routing based on ARP entries would be too much of a hassle, (D) some people don't understand the networking fundamentals, (E) everything looks like a nail once you found a hammer, or (F) all of the above. Insightful comments would be highly appreciated.
Datanauts 171: The Joy Of Engineering With William Lam
Turning to technical folks and their blogs is a good way to "not panic" when it comes to dealing with the trough of woe. In this episode, we'll talk to prolific technical blogger & VMware employee William Lam to get an insider's view of what happens to generate community-oriented content.
The post Datanauts 171: The Joy Of Engineering With William Lam appeared first on Packet Pushers.
Building a GraphQL server on the edge with Cloudflare Workers


Today, we're open-sourcing an exciting project that showcases the strengths of our Cloudflare Workers platform: workers-graphql-server is a batteries-included Apollo GraphQL server, designed to get you up and running quickly with GraphQL.
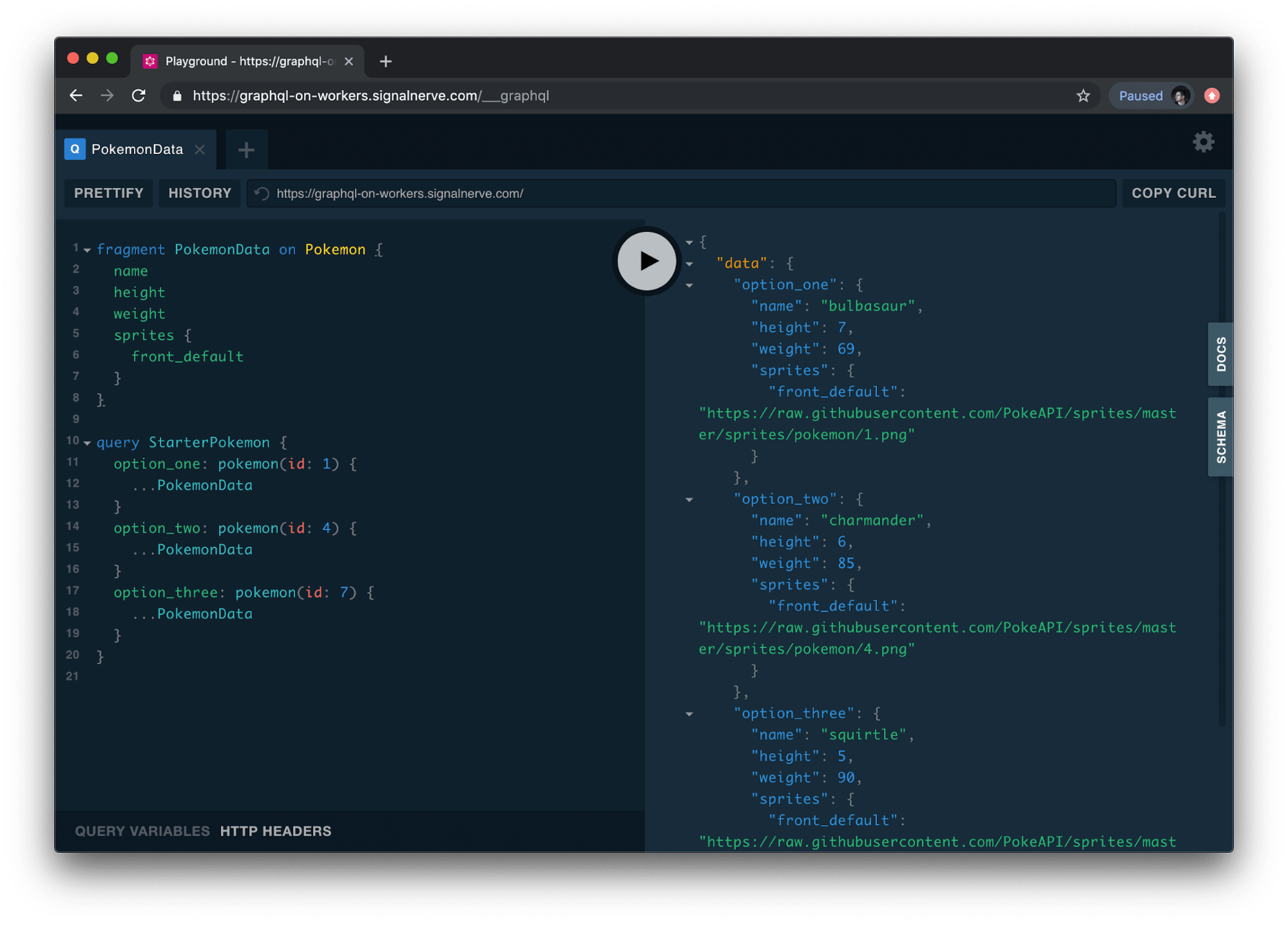
As a full-stack developer, I’m really excited about GraphQL. I love building user interfaces with React, but as a project gets more complex, it can become really difficult to manage how your data is managed inside of an application. GraphQL makes that really easy - instead of having to recall the REST URL structure of your backend API, or remember when your backend server doesn't quite follow REST conventions - you just tell GraphQL what data you want, and it takes care of the rest.
Cloudflare Workers is uniquely suited as a platform to being an incredible place to host a GraphQL server. Because your code is running on Cloudflare's servers around the world, the average latency for your requests is extremely low, and by using Wrangler, our open-source command line tool for building and managing Workers projects, you can deploy new versions of your GraphQL server around the world within seconds.
If you'd like to try the GraphQL Continue reading
Adtran Mosaic Gets Smarter, Announces New Hardware
Adtran upgraded its Mosaic software-defined access suite with new features aimed at improving...
sFlow-RT 3.0 released
The sFlow-RT 3.0 release has a simplified user interface that focusses on metrics needed to manage the performance of the sFlow-RT analytics software and installed applications.Applications are available that replace features from the previous 2.3 release. The following instructions show how to install sFlow-RT 3.0 along with basic data exploration applications.
On a system with Java 1.8+ installed:
wget https://inmon.com/products/sFlow-RT/sflow-rt.tar.gzOn a system with Docker installed:
tar -xvzf sflow-rt.tar.gz
./sflow-rt/get-app.sh sflow-rt flow-trend
./sflow-rt/get-app.sh sflow-rt browse-metrics
./sflow-rt/start.sh
mkdir appThe product user interface can be accessed on port 8008. The Status page, shown at the top of this article, displays key metrics about the performance of the software.
docker run -v $PWD/app:/sflow-rt/app --entrypoint /sflow-rt/get-app.sh sflow/sflow-rt sflow-rt flow-trend
docker run -v $PWD/app:/sflow-rt/app --entrypoint /sflow-rt/get-app.sh sflow/sflow-rt sflow-rt browse-metrics
docker run -v $PWD/app:/sflow-rt/app -p 6343:6343/udp -p 8008:8008 sflow/sflow-rt
The Apps tab lists the two applications we installed, browse-metrics and flow-trend, and the green color of the buttons indicates both applications are healthy.
Click on the flow-trend button to open the application and trend traffic flows in real-time. The RESTflow article describes the flow analytics capabilities of sFlow-RT in Continue reading
VMware SVP Tom Corn: Security Is a Team Sport and vAdmins Play a Starring Role
Application security is changing the role of virtual administrators and expanding their job...
On the recent HTTP/2 DoS attacks


Today, multiple Denial of Service (DoS) vulnerabilities were disclosed for a number of HTTP/2 server implementations. Cloudflare uses NGINX for HTTP/2. Customers using Cloudflare are already protected against these attacks.
The individual vulnerabilities, originally discovered by Netflix and are included in this announcement are:
- CVE-2019-9511 HTTP/2 Data Dribble
- CVE-2019-9512 HTTP/2 Ping Flood
- CVE-2019-9513 HTTP/2 Resource Loop
- CVE-2019-9514 HTTP/2 Reset Flood
- CVE-2019-9515 HTTP/2 Settings Flood
- CVE-2019-9516 HTTP/2 0-Length Headers Leak
- CVE-2019-9518 HTTP/2 Request Data/Header Flood
As soon as we became aware of these vulnerabilities, Cloudflare’s Protocols team started working on fixing them. We first pushed a patch to detect any attack attempts and to see if any normal traffic would be affected by our mitigations. This was followed up with work to mitigate these vulnerabilities; we pushed the changes out few weeks ago and continue to monitor similar attacks on our stack.
If any of our customers host web services over HTTP/2 on an alternative, publicly accessible path that is not behind Cloudflare, we recommend you apply the latest security updates to your origin servers in order to protect yourselves from these HTTP/2 vulnerabilities.
We will soon follow up with more details on these vulnerabilities and how we mitigated them.
Full Continue reading
Exploring Batfish with Cumulus – Part 2
In Part 1 of our look into navigating Batfish with Cumulus, we explored how to get started with communicating with the pybatfish SDK, as well as getting some basic actionable topology information back. With the introduction out of the way, we’re going to take a look at some of the more advanced use cases when it comes to parsing the information we get back in response to our queries. Finally, we’re going to reference an existing CI/CD pipeline, where templates are used to dynamically generate switch configuration files, and see exactly where and how Batfish can fit in and aid in our efforts to dynamically test changes.
For a look under the covers, the examples mentioned in this series of posts are tracked in “https://gitlab.com/permitanyany/cldemo2”
Enforcing Policy
As you may remember, in Part 1 we gathered the expected BGP status of all our sessions via the bgpSessionStatus query and added some simple logic to tell us when any of those sessions would report back as anything but “Established”. Building on that type of policy expectation, we’re going to add a few more rules that we want to enforce in our topology.
For example:
- “A leaf switch should Continue reading
Vodafone Ireland Activates 5G Service in 5 Cities
Fellow Irish network operators Eir and Three plan to launch their respective 5G networks before the...
Heavy Networking 465: Looking Backward and Forward with Harry Quackenboss
Harry Quackenboss is long time veteran of infrastructure technology. In networking he was a VP of Sales of Crescendo for FDDI networking (to the desktop) which was acquired by Cisco. He later founded Woven Systems as a high speed Ethernet company of the time and more lately CEO of cPlane, a SDN company now relaunched […]
The post Heavy Networking 465: Looking Backward and Forward with Harry Quackenboss appeared first on Packet Pushers.
CenturyLink’s Edge Strategy Starts With ‘Several Hundred Million’ Investment
While its edge services today tend to be more “on a bespoke basis,” by 2020 “we expect a huge...
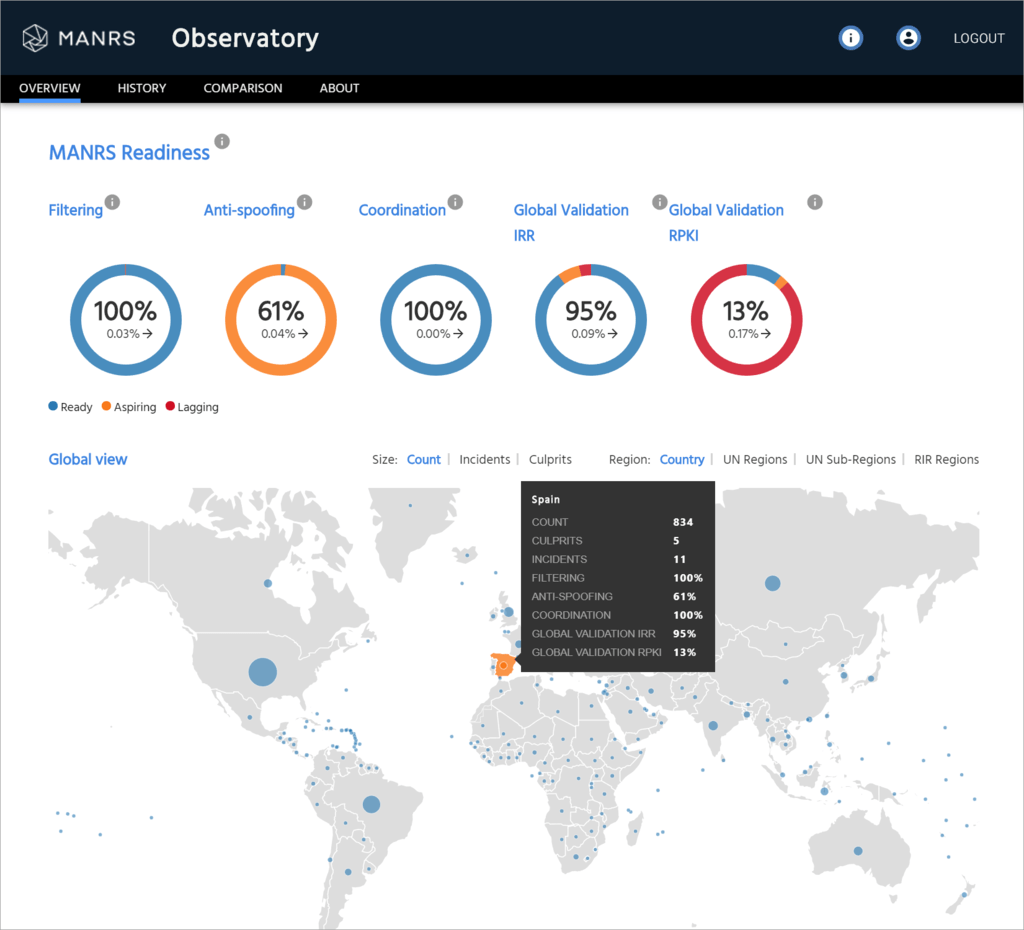
MANRS Observatory: Monitoring the State of Internet Routing Security

Routing security is vital to the future and stability of the Internet, but it’s under constant threat. Which is why we’ve launched a free online tool so that network operators can see how they’re doing, and what they can improve, while anyone can see the health of the Internet at a glance. The MANRS Observatory measures networks’ adherence to MANRS – their “MANRS readiness” – a key indicator of the state of routing security and resiliency of the Internet.
Here’s what the MANRS Observatory is in a nutshell:
- Performance Barometer: MANRS participants can easily monitor how well they adhere to the requirements of this initiative and make any necessary adjustments to their security controls.
- Business Development: Participants can see how they and their peers are performing. They can leverage the MANRS Observatory to determine whether potential partners’ security practices are up to par.
- Government: Policymakers can better understand the state of routing security and resilience and help improve it by calling for MANRS best practices.
- Social Responsibility: MANRS implementation is simple, voluntary, and non-disruptive. The Observatory can help participants ensure they and their peers are keeping their networks secure, which helps improve routing security of the Internet as a whole.
SaaS-ifing Backup Scores Clumio $51M in Funding
The startup, founded by former VMware and Nutanix execs, built a backup service on Amazon Web...


