Day Two Cloud 011: Going All In On Serverless And DevOps
What's it like using serverless in production? We answer that question in this Day Two Cloud podcast with guest Robb Schiefer, who's running a live application on AWS Lambda for a healthcare company. We talk about why the organization adopted serverless, how they chose AWS, and how DevOps practices are key for ongoing operations.Day Two Cloud 011: Going All In On Serverless And DevOps
What's it like using serverless in production? We answer that question in this Day Two Cloud podcast with guest Robb Schiefer, who's running a live application on AWS Lambda for a healthcare company. We talk about why the organization adopted serverless, how they chose AWS, and how DevOps practices are key for ongoing operations.
The post Day Two Cloud 011: Going All In On Serverless And DevOps appeared first on Packet Pushers.
Caribbean Community Gathers Together to Discuss Improving Connectivity in the Region

Cooperation has been key to expanding Internet access around the globe. Ten years ago, the African region created AfPIF, a space focused on collaboration about among regional actors on topics related to peering and interconnection. Inspired by that project, in 2014 I approached Bevil Wooding to create a similar space for the Caribbean.
In recent years, the Caribbean has been losing its traditional industries, such as sugar and banana production. In this context, the Internet can be seen as a good opportunity to leverage the local economy. Fortunately, the idea gained the support of the Caribbean Telecommunications Union (CTU) and the Caribbean Network Operators Group (CaribNOG). That’s how the Caribbean Peering and Interconnection Forum (CarPIF) was born.
From its inaugural meeting in 2015, CarPIF has sought to bring together key infrastructure, service, and content providers to improve network interconnection, lower the cost of connectivity, and increase the number of Internet users and services in the Caribbean. This year, the meeting will be held from 12 to 13 June in Grenada, with the aim of highlight the active role played by the Organization of Eastern Caribbean States (OECS) in the successful deployment of Internet Continue reading
5G Subscriptions to Hit 1.9B in 2024, Ericsson Says
 The Swedish vendor upgraded its forecasts by an additional 400 million subscribers or 27% as 5G...
The Swedish vendor upgraded its forecasts by an additional 400 million subscribers or 27% as 5G...
Project Galileo: Lessons from 5 years of protecting the most vulnerable online

Today is the 5th anniversary of Cloudflare's Project Galileo. Through the Project, Cloudflare protects—at no cost—nearly 600 organizations around the world engaged in some of the most politically and artistically important work online. Because of their work, these organizations are attacked frequently, often with some of the fiercest cyber attacks we’ve seen.

Since it launched in 2014, we haven't talked about Galileo much externally because we worry that drawing more attention to these organizations may put them at increased risk. Internally, however, it's a source of pride for our whole team and is something we dedicate significant resources to. And, for me personally, many of the moments that mark my most meaningful accomplishments were born from our work protecting Project Galileo recipients.
The promise of Project Galileo is simple: Cloudflare will provide our full set of security services to any politically or artistically important organizations at no cost so long as they are either non-profits or small commercial entities. I'm still on the distribution list that receives an email whenever someone applies to be a Project Galileo participant, and those emails remain the first I open every morning.
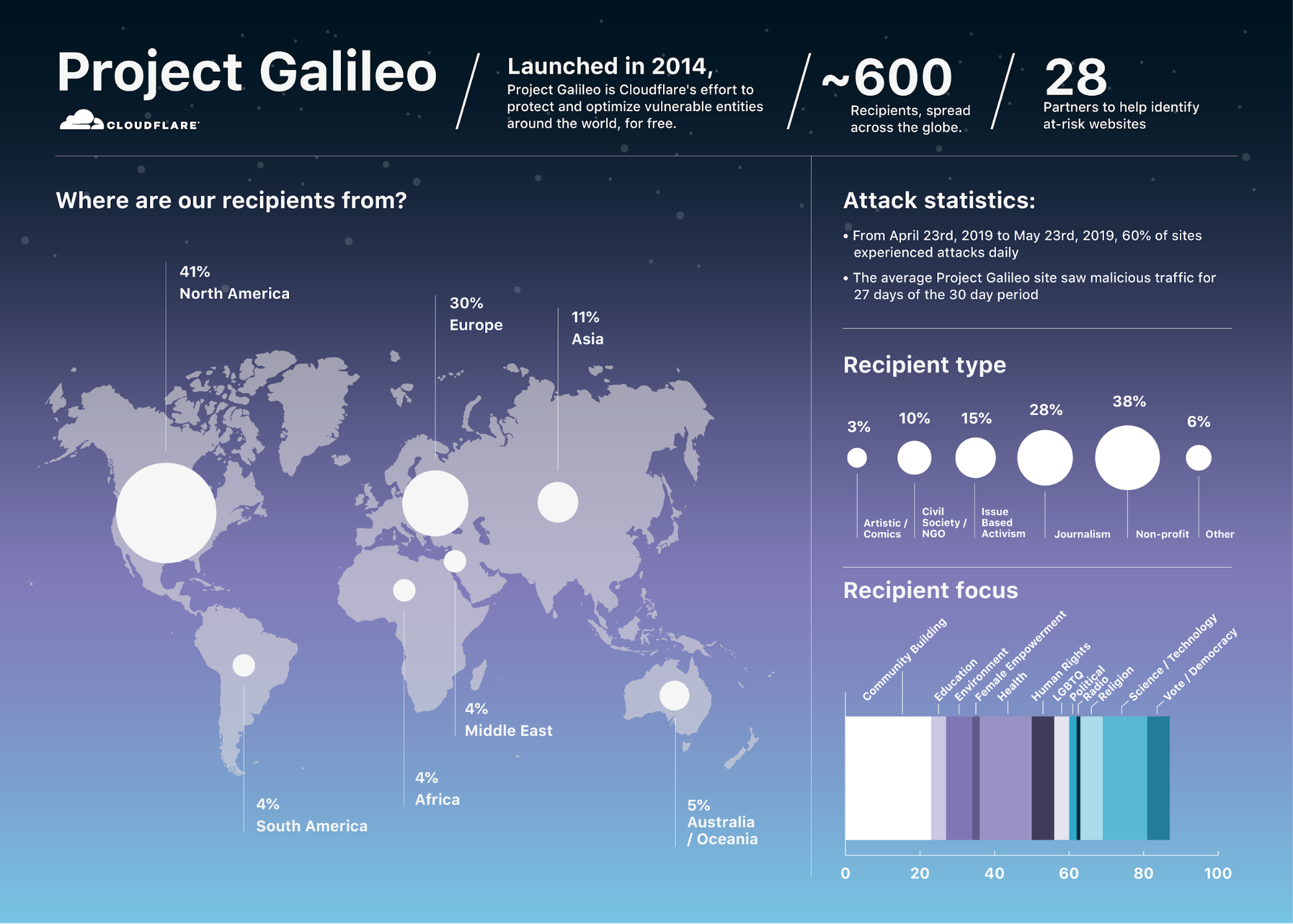
The Project Galileo Backstory
Five years ago, Project Galileo was born Continue reading
Don’t use Opera browser Because Privacy Threat

Lack of transparency, false incentives and lack of trus
The post Don’t use Opera browser Because Privacy Threat appeared first on EtherealMind.
Switch Buffer Sizes and Fermi Estimates
In my quest to understand how much buffer space we really need in high-speed switches I encountered an interesting phenomenon: we no longer have the gut feeling of what makes sense, sometimes going as far as assuming that 16 MB (or 32MB) of buffer space per 10GE/25GE data center ToR switch is another $vendor shenanigan focused on cutting cost. Time for another set of Fermi estimates.
Let’s take a recent data center switch using Trident II+ chipset and having 16 MB of buffer space (source: awesome packet buffers page by Jim Warner). Most of switches using this chipset have 48 10GE ports and 4-6 uplinks (40GE or 100GE).
Read more ...DC/SP. Part 13/8. Real-time data analytics and closed-loop automation with InfluxData Kapacitor for the Data Centre Fabric
Hello my friend,
This article is kind of a special one for me. It doesn’t mean that everything I have written before has a little sense. Everything what I have written about the Data Centre Fabric project was steps towards fully automated data centre operation, and today we make a final step towards the closed-loop automation based using the real-time data analytics by InfluxData Kapacitor.

2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Brief description
According to the official website, InfluxData Kapacitor is alerting system following publish-subscribe design pattern, which supports both steam and batch data processing. If we translate it from the geeks’ language, it means that Kapacitor can subscribe to a certain to topics in the data producer (e.g., time series database – InfluxDB or collector – Telegraf) and start getting information out of it:
- Steam processing means that all the information coming to the subscribed Continue reading