Microsoft Azure Networking Slide Deck Is Ready
After a few weeks of venting my frustrations on Twitter I finally completed Microsoft Azure Networking slide deck last week and published the related demos on GitHub.
I will use the slide deck in a day-long workshop in Zurich (Switzerland) on June 12th and run a series of live webinar sessions in autumn. If you’re a (paid) subscriber you can already download the slides and it would be great if you’d have time to attend the Zurich workshop – it’s infinitely better to discuss interesting challenges face-to-face than to type questions in a virtual classroom.
RPCValet: NI-driven tail-aware balancing of µs-scale RPCs
RPCValet: NI-driven tail-aware balancing of µs-scale RPCs Daglis et al., ASPLOS’19
Last week we learned about the [increased tail-latency sensitivity of microservices based applications with high RPC fan-outs. Seer uses estimates of queue depths to mitigate latency spikes on the order of 10-100ms, in conjunction with a cluster manager. Today’s paper choice, RPCValet, operates at latencies 3 orders of magnitude lower, targeting reduction in tail latency for services that themselves have service times on the order of a small number of µs (e.g., the average service time for memcached is approximately 2µs).
The net result of rapid advancements in the networking world is that inter-tier communications latency will approach the fundamental lower bound of speed-of-light propagation in the foreseeable future. The focus of optimization hence will completely shift to efficiently handling RPCs at the endpoints as soon as they are delivered from the network.
Furthermore, the evaluation shows that “RPCValet leaves no significant room for improvement” when compared against the theoretical ideal (it comes within 3-15%). So what we have here is a glimpse of the limits for low-latency RPCs under load. When it’s no longer physically possible to go meaningfully faster, further application-level performance Continue reading
Weekly Top Posts: 2019-05-19
- SDxCentral Weekly Wrap: Thrangrycat Attacks Cisco Switches, Routers, Firewalls
- OpenStack Keeps One Eye on the Prize, One Over Its Shoulder
- HPE Buys Supercomputer Company Cray for $1.3B, Boosts Its HPC Business
- Trump Issues Long-Rumored Executive Order Targeting Chinese Telco Vendors
- Thrangrycat Attacks Cisco Switches, Routers, Firewalls
Cloudflare architecture and how BPF eats the world
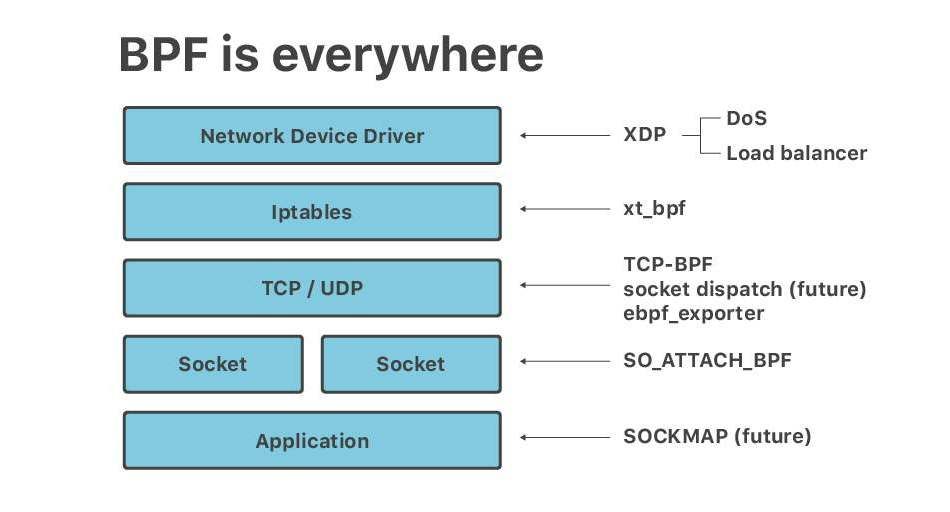
Recently at Netdev 0x13, the Conference on Linux Networking in Prague, I gave a short talk titled "Linux at Cloudflare". The talk ended up being mostly about BPF. It seems, no matter the question - BPF is the answer.
Here is a transcript of a slightly adjusted version of that talk.
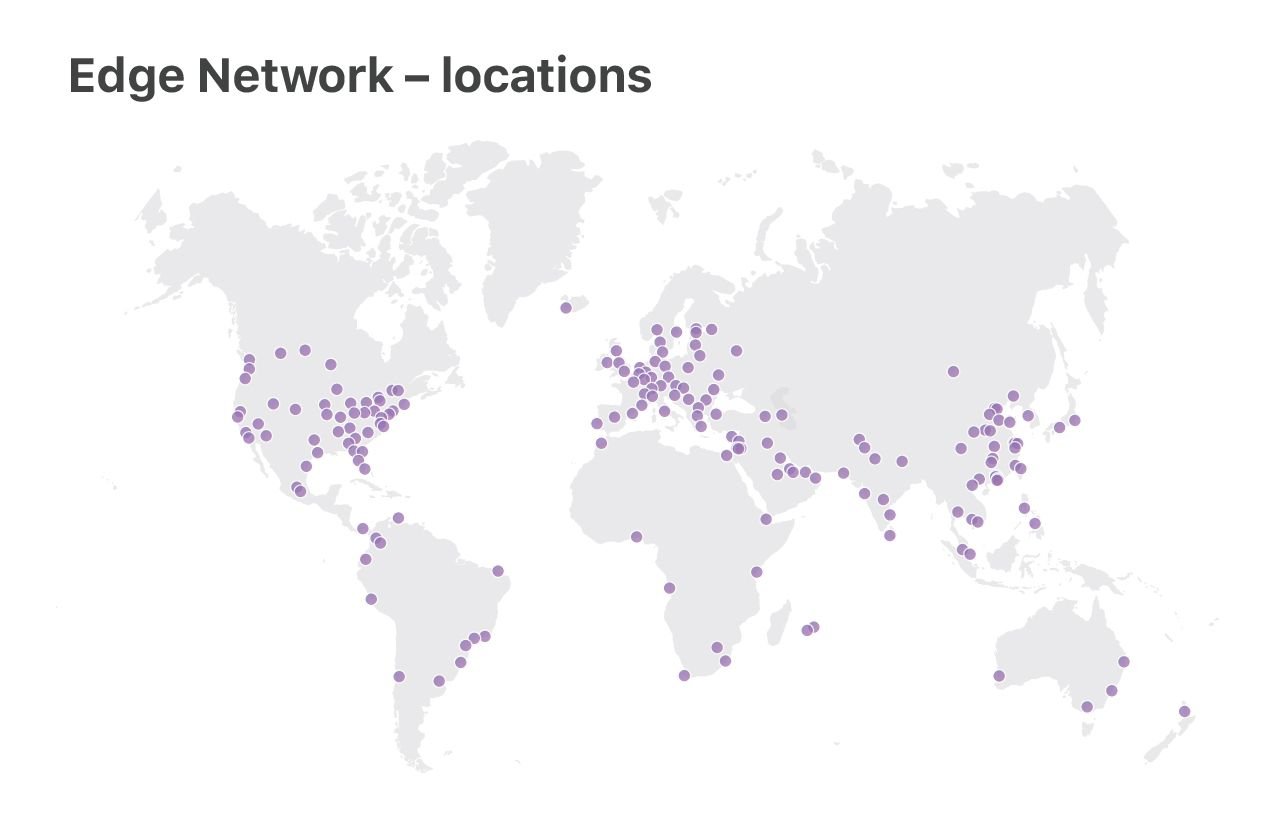
At Cloudflare we run Linux on our servers. We operate two categories of data centers: large "Core" data centers, processing logs, analyzing attacks, computing analytics, and the "Edge" server fleet, delivering customer content from 180 locations across the world.
In this talk, we will focus on the "Edge" servers. It's here where we use the newest Linux features, optimize for performance and care deeply about DoS resilience.
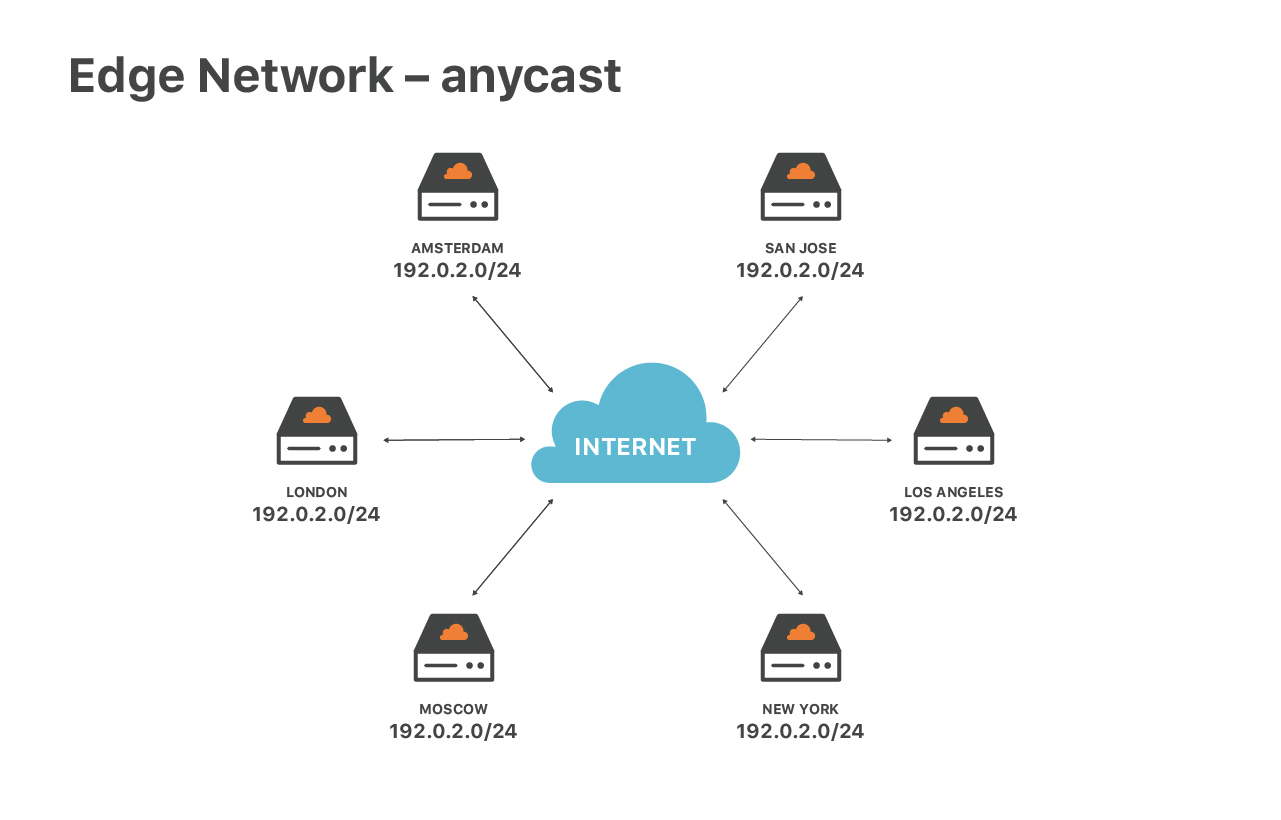
Our edge service is special due to our network configuration - we are extensively using anycast routing. Anycast means that the same set of IP addresses are announced by all our data centers.
This design has great advantages. First, it guarantees the optimal speed for end users. No matter where you are located, you will always reach the closest data center. Then, anycast helps us to spread out DoS traffic. During attacks each of the locations receives a small fraction of Continue reading
KubeCon to Focus on Stability, Extensibility, Stateful Support
 “We expect more people to build frameworks on top of Kubernetes,” said Janet Kuo, a software...
“We expect more people to build frameworks on top of Kubernetes,” said Janet Kuo, a software...
Join Cloudflare & Yandex at our Moscow meetup! Присоединяйтесь к митапу в Москве!


Are you based in Moscow? Cloudflare is partnering with Yandex to produce a meetup this month in Yandex's Moscow headquarters. We would love to invite you to join us to learn about the newest in the Internet industry. You'll join Cloudflare's users, stakeholders from the tech community, and Engineers and Product Managers from both Cloudflare and Yandex.
Cloudflare Moscow Meetup
Tuesday, May 30, 2019: 18:00 - 22:00
Location: Yandex - Ulitsa L'va Tolstogo, 16, Moskva, Russia, 119021
Talks will include "Performance and scalability at Cloudflare”, "Security at Yandex Cloud", and "Edge computing".
Speakers will include Evgeny Sidorov, Information Security Engineer at Yandex, Ivan Babrou, Performance Engineer at Cloudflare, Alex Cruz Farmer, Product Manager for Firewall at Cloudflare, and Olga Skobeleva, Solutions Engineer at Cloudflare.
Agenda:
18:00 - 19:00 - Registration and welcome cocktail
19:00 - 19:10 - Cloudflare overview
19:10 - 19:40 - Performance and scalability at Cloudflare
19:40 - 20:10 - Security at Yandex Cloud
20:10 - 20:40 - Cloudflare security solutions and industry security trends
20:40 - 21:10 - Edge computing
Q&A
The talks will be followed by food, drinks, and networking.
View Event Details & Register Here »
We'll Continue reading
Powerline Install and Setup for Ubuntu Bash on Windows
Install and configure Powerline for Ubuntu Bash on Windows 10.Powerline Install and Setup for Ubuntu Bash on Windows
I am currently using a Windows 10 laptop as my main OS. IMHO Microsoft has really turned it around as a company in recent years and I no longer think of them as M$ Virus Corp!! I still live in a terminal session for a lot of my day and I am not ready give up on Bash just yet. The ability to...Ericsson Head Criticizes Europe For Slow 5G Rollouts
 Ericsson CEO Börje Ekholm blames European government officials and regulators for letting Europe...
Ericsson CEO Börje Ekholm blames European government officials and regulators for letting Europe...
HPE Buys Supercomputer Company Cray for $1.3B, Boosts Its HPC Business
 Cray recently won a portion of the U.S. Department of Energy’s $600 million exascale...
Cray recently won a portion of the U.S. Department of Energy’s $600 million exascale...
Project EVE Seed Code Drops, Creates Virtualization Standard for Edge Devices
 LF Edge announced the Edge Virtualization Engine (EVE) as a new open source project when it...
LF Edge announced the Edge Virtualization Engine (EVE) as a new open source project when it...
ngrok on Cumulus Linux
If you’ve landed on this page, you likely already have a good idea of what ngrok is and what it does. For those that don’t, the reader’s digest version is that it’s a simple way to securely tunnel to a device that sits behind a firewall/NAT device. It’s a slick implementation that is easy to install and allows a few different tunneling options. For the purpose of this blog, we’re using ssh and eliminating the need for port forwarding on the firewall.
Here are step-by-step instructions for turning up ngrok ssh services on Cumulus Linux. Note that these instructions work on the default VRF. You’ll need to take additional configuration steps to get this to work on Cumulus Linux with mgmt VRF enabled.
First, install the unzip package from the repo

Then wget the ngrok application, or optionally add the appropriate repo to your /etc/apt/sources.list and use apt to pull the package. You’ll obviously want to find the appropriate package for your switch (x86 or ARM).
If you don’t know the download link, navigate to https://dashboard.ngrok.com/get-started and copy the link address on the web link of the download section (right click the download link to snag the Continue reading
SDxCentral Weekly Wrap: Thrangrycat Attacks Cisco Switches, Routers, Firewalls
 SDxCentral Weekly Wrap for May 17, 2019: Flaws found in Cisco switches, routers, and firewalls;...
SDxCentral Weekly Wrap for May 17, 2019: Flaws found in Cisco switches, routers, and firewalls;...
Open19 Hardware in PoCs With ‘Mega Data Center Operators’
 Open19 Foundation President Yuval Bachar kicked off the second annual summit by declaring that...
Open19 Foundation President Yuval Bachar kicked off the second annual summit by declaring that...
History of Networking: Pseudowires
In this episode of the History of Networking, Donald Sharp and I talk to Luca Martini about the origins of pseudowires—one of the more interesting innovations in the use of MPLS.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/