Response: How Important is it to Understand Hardware Architecture?

This reddit post asked the question: For example, I’m going through a Cisco Live presentation on troubleshooting ASR routers, and the first 50 slides or so are completely dedicated to describing the Route Processors, Packet Engines, ASICs, Buffers, etc., and the different paths that packets can take through the hardware. While that’s all obviously important […]
The post Response: How Important is it to Understand Hardware Architecture? appeared first on EtherealMind.
Senegal Kicks Off Enhancing IoT Security Project

On April 4, 2018, the Canadian Multistakeholder Process: Enhancing Internet of Things (IoT) Security held its first convening in partnership with the Canadian Internet Registration Authority (CIRA); CANARIE; Innovation, Science and Economic Development (ISED) Canada; and the Canadian Internet Policy and Public Interest Clinic (CIPIC). Over 80 participants from government, academia, public interest, industry, and other organizations attended the first meeting and many have continued to engage at in-person and virtual meetings ever since. Over the past eight months, this group has experienced significant success in the areas of consumer education, labeling, and network resiliency. And these achievements have been well-noted on a global scale.
A delegation from Senegal came to Canada in July to meet with members of the Enhancing IoT Security oversight committee. The group was comprised of government officials, Senegal Chapter members, and staff from the Internet Society’s African Bureau. The delegation met with Canadian government officials, technologists, public interest groups, and North American Bureau staff to learn more about how and why the IoT security project was initiated, and what the group had accomplished to date. The group discussed the significant successes the Canadian multistakeholder group had already achieved, the challenges it faced, Continue reading
Response: Super Micro says no implants on motherboards

I’m convinced that Bloomberg is wrong about the hardware implants. Until they retract the story they don’t have credibility to report on technology. Supermicro commissioned 3rd party audit and found nothing which is confirmation of many other sources who also refute the claims. The ONLY people making the claim is Bloomberg and there is no […]
The post Response: Super Micro says no implants on motherboards appeared first on EtherealMind.
Murambinda Works Community Engagement Workshop in Buhera: Meeting Challenges with Opportunity

Over 100 community members, including head masters, government officials, teachers and heads of primary and secondary schools gathered in Buhera rural district council of Zimbabwe on 15 November, eager to engage in discussions related to the initial deployment of the Murambinda Works Community Network. Schools, health and the local authority facilities have been earmarked as the initial benefactors for the inaugural roll out of the Murambinda Works Community Network.
The CEO of Murambinda, Mama Emilie gave a welcoming speech followed by the district school inspector of Buhera who talked about the importance of equipping their schools with ICT. “We cannot imagine a good curriculum that has not taken into consideration ICT. The partnership with Internet Society is a blessing to the district. We want to support it until infinity,” he said. The inspector also mentioned some of the challenges they are facing in their schools including the lack of power, unavailability of computers and connectivity. (Since 2015, 1200 teachers have been trained in ICT, but couldn’t do much with their acquired knowledge.)
TelONE, the national Telecommunications parastatal company with infrastructure in Murambinda Town, was also present at the workshop. “One man cannot make it but we can work together Continue reading
Tech Time is Real Time
Silicon Valley is both an addiction and passion where entrepreneurs seek the realm of the impossible. Real-time language translation, fraud detection, and autonomous vehicle control are being addressed through the use of neural network models, detecting patterns and behaviors across massive amounts of structured and unstructured data. Indeed, change is not only a constant progression in Silicon Valley, it is a continuum in time. Every piece of traditional technology has to imminently become smarter, challenged or be eliminated. While this transformation is especially true for entrepreneurs, invention is not limited to start-ups. I have witnessed several waves of evolution and revolution during my journey in Silicon Valley in both high-tech and networking.
6 Things You Should Know About 802.11ax
New applications, an explosion in mobile device use, and IoT are driving Wi-Fi connectivity needs through the roof. 802.11ax tries to address the issues while creating new opportunities and services.
The truth about Black Friday and Cyber Monday

At Cloudflare we handle a lot of traffic on behalf of our customers. Something we all see and hear a lot about at this time of year are Black Friday (23 November this year) and Cyber Monday (26 November) - but just how important are these days on the Internet?

To try and answer this question, we took a look at anonymised samples of HTTP requests crossing our network. First of all, let’s look at total page views from across our global network from the last few weeks and see if we can spot Black Friday and Cyber Monday:
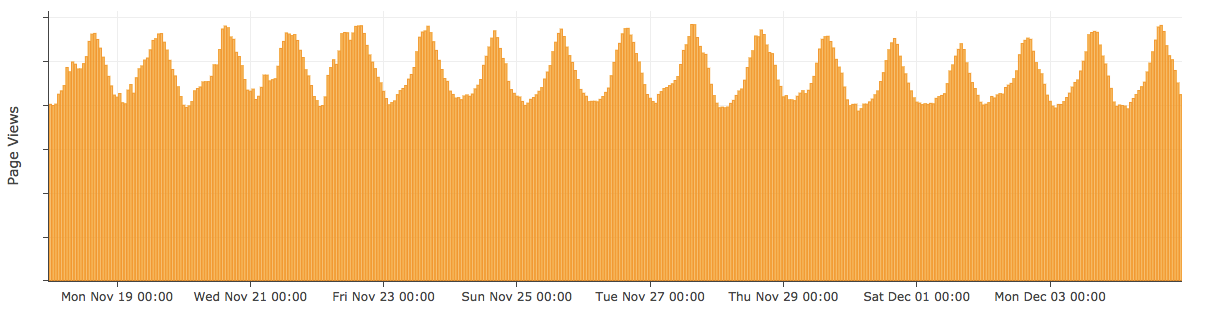
So this is total page views by day (UTC) from November 19 (a week before Cyber Monday) until Monday December 3. Other than follow-the-sun fluctuations in a repeating daily pattern, each whole day is pretty similar in shape and size compared to the last. Black Friday and Cyber Monday aren’t visible in overall traffic patterns.
Get specific
We have a very diverse set of customers across 12 million domain names and not all of them are selling products or doing so directly online. To identify those websites Continue reading
Building Your Own Virtual Lab
Last week we published Matt Oswalt’s thoughts on using virtual labs in training and testing. In the second part of his interview with Christoph Jaggi he talked about building a virtual lab.
Matt will cover the same topic in way more details in his guest speaker presentation in Spring 2019 Building Network Automation Solutions online course. Register here.
Read more ...A new look on your Cloudflare dashboard
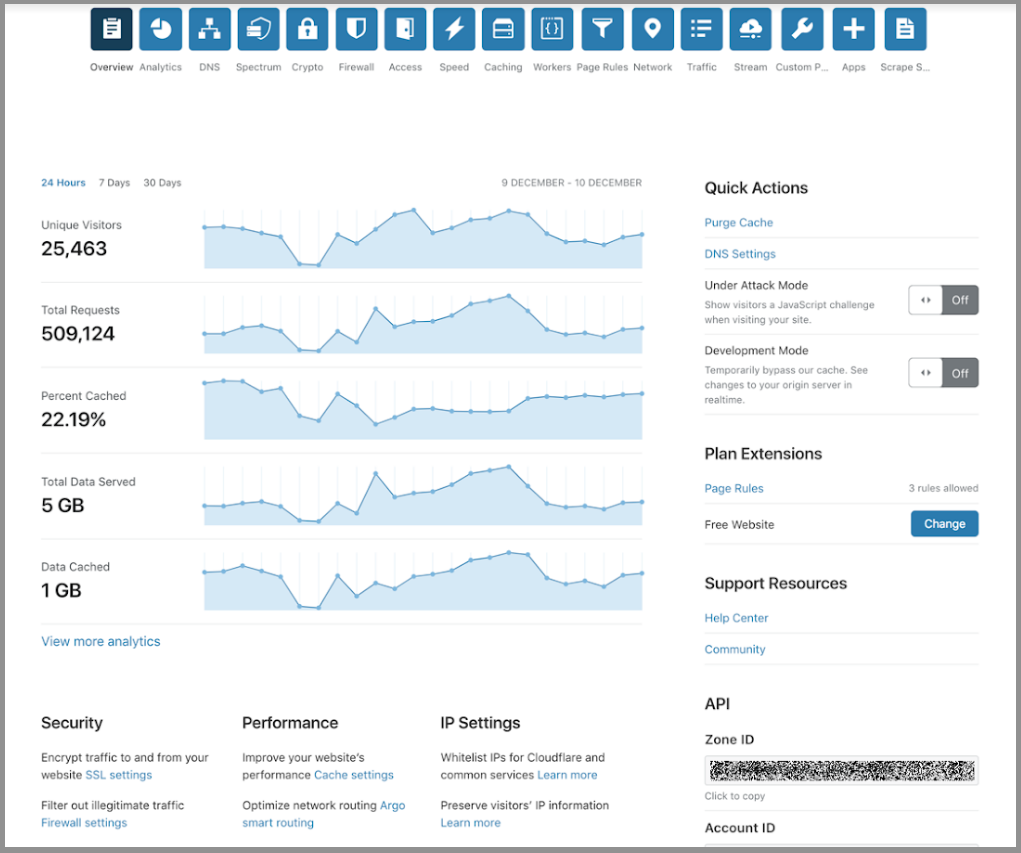
Building a great customer experience is a top priority here at Cloudflare. Over the last week, we have been slowly rolling out an improvement to our customer dashboard - specifically the zone overview page. We are now ready to share the new dashboard with everyone.
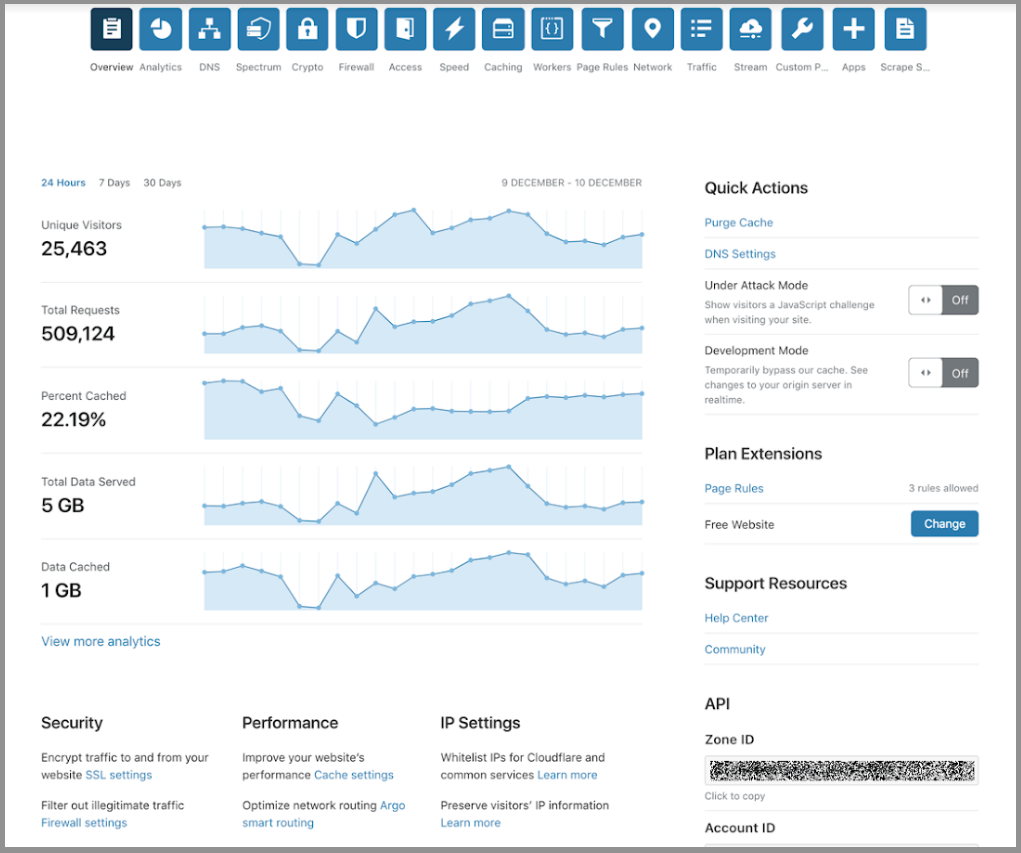
Many of the changes you’ll notice first were driven directly by customer feedback. We’ve heard time and time again that site owners would like better visibility of their key analytics, and for it to be easier to apply certain common settings changes. This new dashboard provides both, with a snapshot of several of your key analytics, and a new toolkit area for easy access to key functions. This page has also been redesigned from top to bottom for responsiveness across various devices and screen widths.
Even more interesting is all the work under-the-hood that went into making this release and how it sets the stage for improvements to our customer experience as we look ahead to 2019. This is one of the first pieces of production Product work shipped using our new prototyping framework. We will soon be sharing details of the design systems work that underlies the new experience on Continue reading
Optanix Launches Monitoring Platform From Internal Software Offering
 “Most software that’s used for monitoring comes from software companies. We built this software out of operational need and we built it as users of the technology,” said Optanix CSO Edmond Baydian.
“Most software that’s used for monitoring comes from software companies. We built this software out of operational need and we built it as users of the technology,” said Optanix CSO Edmond Baydian.
Deutsche Telekom Launches 5G Network in Poland With Huawei Equipment
 Things aren’t all bad news for Huawei. T-Mobile Poland confirmed that Huawei is the sole vendor supporting its 5G network.
Things aren’t all bad news for Huawei. T-Mobile Poland confirmed that Huawei is the sole vendor supporting its 5G network.
VMware Rolls Out NSX Service Mesh Based on Istio
 The NSX Service Mesh beta will initially support Cloud PKS (formerly known as VMware Kubernetes Engine or VKE), but VMware plans to extend it to any Kubernetes environment.
The NSX Service Mesh beta will initially support Cloud PKS (formerly known as VMware Kubernetes Engine or VKE), but VMware plans to extend it to any Kubernetes environment.
Lenovo Works With Cumulus to Offer Disaggregated Switch Hardware, Software
 Cumulus already offers its NOS on lots of different hardware. But this is Lenovo’s first foray into the disaggregated switch model.
Cumulus already offers its NOS on lots of different hardware. But this is Lenovo’s first foray into the disaggregated switch model.
SD-WAN Will Be Fueled By Collaboration Between Cloud Providers and Vendors
 The latest numbers from IHS Markit show that SD-WAN revenue grew 23 percent from the previous quarter to $284 million. VMware continues to hold the No. 1 spot.
The latest numbers from IHS Markit show that SD-WAN revenue grew 23 percent from the previous quarter to $284 million. VMware continues to hold the No. 1 spot.
Optimal Route Reflection: Next Hop Self
Recently, I posted a video short take I did on BGP optimal route reflection. A reader wrote in the comments to that post:
…why can’t Router set next hop self to updates to router E and avoid this suboptimal path?
To answer this question, it is best to return to the scene of the suboptimality—

To describe the problem again: A and C are sending the same route to B, which is a route reflector. B selects the best path from its perspective, which is through B, and sends this route to each of its clients. In this case, E will learn the path with a next hop of A, even though the path through C is closer from E’s perspective. In the video, I discuss several ways to solve this problem; one option I do not talk about is allowing B to set the next hop to itself. Would this work?
Before answering the question, however, it is important to make one observation: I have drawn this network with B as a router in the forwarding path. In many networks, the route reflector is a virtual machine, or a *nix host, and is not capable of forwarding the traffic Continue reading
Pivotal Picks Kubernetes, Knative to Bust Serverless Siloes
 The Pivotal Function Service is the first multi-cloud packaging of the Kubernetes-based Knative project and operates alongside the Pivotal Application Service and Pivotal Container Service.
The Pivotal Function Service is the first multi-cloud packaging of the Kubernetes-based Knative project and operates alongside the Pivotal Application Service and Pivotal Container Service.
