How and Why to Give 4G the 5G Treatment
 MEC is an idea whose time has come. And for mobile operators, advertisers, and OTT providers, it's also an idea that can't come soon enough.
MEC is an idea whose time has come. And for mobile operators, advertisers, and OTT providers, it's also an idea that can't come soon enough.
Attitude and Gratitude
I don’t often let my studies in philosophy and worldview creep into these pages intentionally. I don’t think it can be helped, of course, because the more I study philosophy, the more I see just how practical it is (contrary to popular belief). On the other hand, sometimes an observation about our world jumps out at me so strongly that I cannot help but to post about it here. If you don’t want to hear this, I give you permission to stop reading now. 
Today, in the U.S., is what is called “Black Friday.” The name derives from a major stock market crash in the 1850’s, but was eventually applied to the combined shopping and football crowds the day after Thanksgiving by the Philadelphia Police, and now, finally to the general shopping day after Thanksgiving in the U.S.
Thanksgiving is all about giving thanks. About gathering family and friends, and appreciating community, and people, and the shared blessings of homes and meals together. It is interesting that Thanksgiving and Black Friday are juxtaposed in just this way. The family right up against the commercial, the quietness of the home against the loudness of the market. Maybe Continue reading
5 Ways to Improve Video and Real-time Enterprise Apps
By taking a more proactive approach to mobile worker connectivity, enterprises can not only significantly improve productivity but also decrease company support costs.
Every 7.8μs your computer’s memory has a hiccup


Modern DDR3 SDRAM. Source: BY-SA/4.0 by Kjerish
During my recent visit to the Computer History Museum in Mountain View, I found myself staring at some ancient magnetic core memory.

Source: BY-SA/3.0 by Konstantin Lanzet
I promptly concluded I had absolutely no idea on how these things could ever work. I wondered if the rings rotate (they don't), and why each ring has three wires woven through it (and I still don’t understand exactly how these work). More importantly, I realized I have very little understanding on how the modern computer memory - dynamic RAM - works!
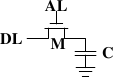
Source: Ulrich Drepper's series about memory
I was particularly interested in one of the consequences of how dynamic RAM works. You see, each bit of data is stored by the charge (or lack of it) on a tiny capacitor within the RAM chip. But these capacitors gradually lose their charge over time. To avoid losing the stored data, they must regularly get refreshed to restore the charge (if present) to its original level. This refresh process involves reading the value of every bit and then writing it back. During this "refresh" time, the memory is busy and it can't perform normal operations Continue reading
Weekly Show 417: Meeting 5G Demands With Cisco’s 5G xHaul Transport (Sponsored)
In today’s sponsored podcast we discuss the new demands that 5G will put on service providers, and how Cisco’s 5G xHaul Transport solution can meet those demands.
The post Weekly Show 417: Meeting 5G Demands With Cisco’s 5G xHaul Transport (Sponsored) appeared first on Packet Pushers.
Serverless Progressive Web Apps using React with Cloudflare Workers
Let me tell you the story of how I learned that you can build Progressive Web Apps on Cloudflare’s network around the globe with one JavaScript bundle that runs both in the browser and on Cloudflare Workers with no modification and no separate bundling for client and server. And when registered as a Service Worker, the same JavaScript bundle will turn your page into a Progressive Web App that doesn’t even make network requests. Here's how that works...
"Any resemblance to actual startups, living or IPO'd, is purely coincidental and unintended" - @sevki
A (possibly apocryphal) Story
I recently met up with some old friends in London who told me they were starting a new business. They did what every coder would do... they quickly hacked something together, bought a domain, and registered the GitHub org and thus Buzzwords was born.
The idea was simple: you could feed the name of your application into a machine learning model and it would generate the configuration files for your deployment for various container orchestrators. They achieved this by going through millions of deployment configurations and training a linear regression model by gamifying quantum computing because blockchain, or something (I told you this Continue reading
Black Friday Blowout: Hot Tech Picks for 2019
‘Tis the season… for the best shopping deals! What’s on tech pros’ must-have technology list for 2019?
From Excel to Network Infrastructure as Code with Carl Buchmann
After a series of forward-looking podcast episodes we returned to real life and talked with Carl Buchmann about his network automation journey, from managing upgrades with Excel and using Excel as the configuration consistency tool to network-infrastructure-as-code concepts he described in a guest blog post in February 2018
Read more ...Cisco Expands Intent-Based Networking Portfolio
The expansion of the portfolio brings IBN to the end-to-end network and can be deployed at customers of all sizes.
PQ 159: The SATCOM Primer For Network Engineers
Today's Priority Queue is a primer on satellite communications for military and commercial networks, including key basics on frequency bands and coverage areas, how different orbits affect network design, and more. Our guests are PC Drew and Evander Cook.
The post PQ 159: The SATCOM Primer For Network Engineers appeared first on Packet Pushers.
How to Avoid Being the Network Turkey
In honor of the Thanksgiving holiday, we’ve put together a few handy tips on how to avoid becoming the network turkey. While many may enjoy it at the family dinner table, nobody wants to be the turkey at work, causing disruptions for their coworkers and organization.
Fast Google Fonts with Cloudflare Workers
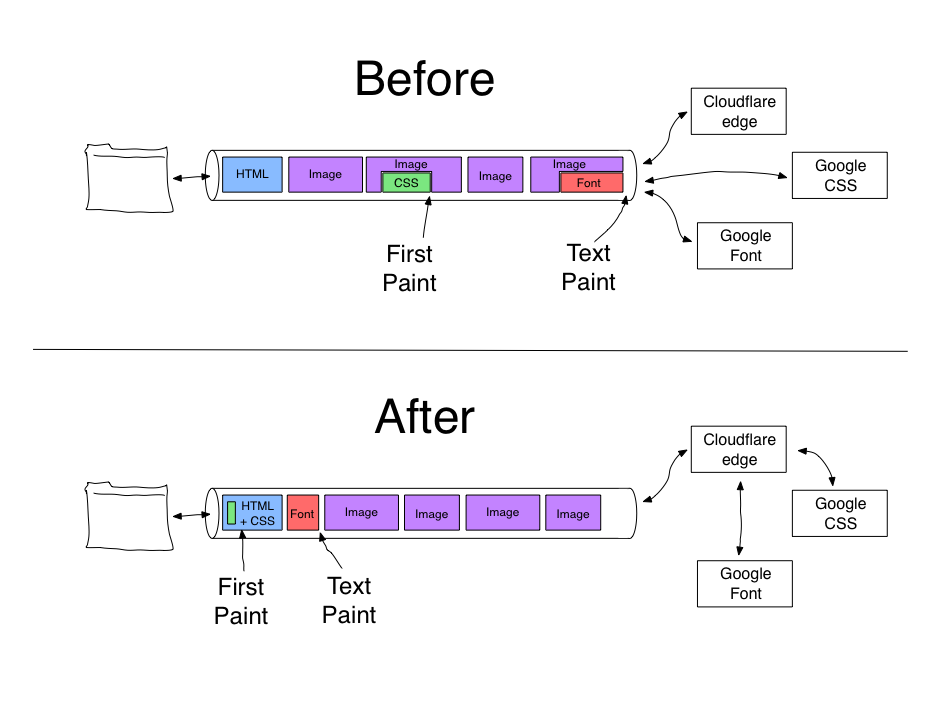
Google Fonts is one of the most common third-party resources on the web, but carries with it significant user-facing performance issues. Cloudflare Workers running at the edge is a great solution for fixing these performance issues, without having to modify the publishing system for every site using Google Fonts.
This post walks through the implementation details for how to fix the performance of Google Fonts with Cloudflare Workers. More importantly, it also provides code for doing high-performance content modification at the edge using Cloudflare Workers.
Google fonts are SLOW
First, some background. Google Fonts provides a rich selection of royalty-free fonts for sites to use. You select the fonts you want to use, and end up with a simple stylesheet URL to include on your pages, as well as styles to use for applying the fonts to parts of the page:
<link href="https://fonts.googleapis.com/css?family=Open+Sans|Roboto+Slab"
rel="stylesheet">
<style>
body {
font-family: 'Open Sans', sans-serif;
}
h1 {
font-family: 'Roboto Slab', serif;
}
Your visitor’s browser fetches the CSS file as soon as the HTML for the page is available. The browser will request the underlying font files when the browser does layout for the page and discovers that it needs Continue reading
Philippines Department of ICT Sets the Multistakeholder Model into Action

Early this year, we embarked on an initiative with the Philippines Department of ICT (DICT) to co-develop the country’s National ICT Ecosystem Framework (NIEF) in a multistakeholder fashion. The NIEF, which succeeds the Philippine Digital Strategy, will guide the course of ICT use and development, as well as the priority areas for government, until 2022.
Our collaboration builds upon the success of the Philippine Chapter’s work with key stakeholders to advance open Internet development in the country, particularly in the policy sphere, and DICT’s sustained drive to expand avenues for participation in its policy formulation. Just last year, DICT and the Chapter, together with the Foundation for Media Alternatives, spearheaded the first Philippine Internet Governance Colloquium, which has been scaled up to a countrywide roadshow this year to help address pertinent Internet issues in different localities.
Having formalized our partnership in a memorandum of understanding, signed in July by DICT’s Secretary, Eliseo M. Rio, and the Internet Society’s Regional Bureau Director for Asia-Pacific, Rajnesh D. Singh, we pledged to support the DICT in embedding the multistakeholder approach not only in the framework’s development but in its implementation. Our engagement was complemented by an Internet Governance training workshop Continue reading
ONUG Europe 2018 – What to Expect
 SDxCentral spoke with Nick Lippis, ONUG co-founder and co-chair, about ONUG’s first conference in Europe. The event is part of a partnership with Barclays, and will be held December 7 at their corporate headquarters in London.
SDxCentral spoke with Nick Lippis, ONUG co-founder and co-chair, about ONUG’s first conference in Europe. The event is part of a partnership with Barclays, and will be held December 7 at their corporate headquarters in London.
Big Cloud Players, Other Hyperscalers Spend $26B on Capex in Q3 2018
 Beyond the usual suspects, Alibaba's capex leapt in the quarter putting it ahead of many other hyperscale operators.
Beyond the usual suspects, Alibaba's capex leapt in the quarter putting it ahead of many other hyperscale operators.
GSMA Launches Edge Cloud Initiative for Operators
 Huawei is a key player in the group, which might explain why no U.S. operators are members.
Huawei is a key player in the group, which might explain why no U.S. operators are members.
Pivot3 HCI Beats Dell EMC, HPE for Airport Data Center Modernization
 The vendor’s resiliency also improved airport security. “With security you can’t afford any downtime,” said the director of IT and security at Charleston International Airport.
The vendor’s resiliency also improved airport security. “With security you can’t afford any downtime,” said the director of IT and security at Charleston International Airport.
Microsoft Spreads Open Enclave SDK, Integrates With Azure IoT Edge
 The SDK abstracts the developer away from having to deal with hardware security.
The SDK abstracts the developer away from having to deal with hardware security.
SDxCentral’s Weekly Roundup — November 21, 2018
 Cisco acquires software provider Ensoft; AWS expands language processing service and Snowball; and the LF Networking Fund grows its membership.
Cisco acquires software provider Ensoft; AWS expands language processing service and Snowball; and the LF Networking Fund grows its membership.