8 Networking Startups Shaking Up the Industry
The hottest networking startups are leveraging trends like artificial intelligence and interoperability as well as building on tried and true technologies of the past.
Redefining Active-Active Network Connections
Network device and data center connections often described as "active-active" might be better termed "psuedo active-active."
Schneier’s Law Applied to Networking
A while ago I stumbled upon Schneier’s law (must-read):
Any person can invent a security system so clever that she or he can't think of how to break it.
I’m pretty sure there’s a networking equivalent:
Any person can create a clever network design that is so complex that she or he can't figure out how it will fail in production.
I know I’ve been there with my early OSPF network designs.
Traceroute through Firepower Threat Defense
Nearly eight years ago, I wrote an article about configuring the ASA to permit Traceroute and how to make the device show up in the output. That article is still relevant and gets quite a few hits every day. I wanted to put together a similar How-To article for those using Firepower Threat Defense.
This article examines the configuration required to allow proper traceroute functionality in an FTD environment. The examples shown here leverage Firepower Management Center to manage Firepower Threat Defense. As with any configuration, please assess the security impact and applicability to your environment before implementing.
Before we get started, it is important to understand that there are two basic types of Traceroute implementations. I am using OSX for testing and it defaults to using UDP packets for the test. However, I can also test with ICMP using the -I option. I am already permitting all outbound traffic, so this is not a problem of allowing the UDP or ICMP toward the destination.
Both types of traceroute depend on sending packets with an incrementing TTL field. This is the field that each router decreases as the packet is forwarded. Any router decreasing this to zero should drop the Continue reading
Count My Voice: Demanding an Internet That Benefits Everyone
The Internet Society has a vision that the Internet must be open, global, and secure for the good of all people. But to get there, the world must demand change in how decisions that shape the Internet’s future are made. Decisions being made behind closed doors.
We’re asking young people around the world – smart passionate people who are spearheading online diversity initiatives, using tech for social development, or working to make the Internet more inclusive – to raise their voice and let policy and decision-makers know that when it comes to the policies that shape the Internet their voice counts.
The digital future impacts us all. Open the doors and listen to the diverse voices of people both online and off. Let’s build an Internet that’s for everyone.
Mary Helda Akongo is one of those voices. A recent graduate of Makerere University in Kampala, Uganda, she believes technology has the power to positively influence the social, political, and economic development of women in Africa. Founder of Roaring Doves, an online and offline peer support community for victims and survivors of gender-based violence, she is also the operations and programs manager for Zimba Women, a Ugandan organization that Continue reading
Autopilot for Elite Dangerous using OpenCV and thoughts on CV enabled bots in visual-to-keyboard loop
Ok, first let’s get one thing clear. This is an educational project for me learning some computer vision algorithms (I want to make an insect identification system to protect a bee hive, – but that is for much later article) and the game Elite Dangerous provided only interesting guinea pig here to test some principles. This was never intended as a game cheat/bot or anything like that, although in the last chapter I will give my thoughts on AI becoming a thing playing games using undetectable external “human loops” (e.g. looking at monitor and pushing keyboard) that no anti-cheat will ever catch, but that is way beyond my motivation as I personally like Elite as it is and definitely do not want to destroy its internal mechanics by creating a farming/trading bot this way. That is also the reason why code of my experiments is not disclosed. If I do not figure out some clever way how to share this without some script-kiddies turning this experiment into a cheat I never will share this code. If you are here looking for a game cheat, you will not get it. If you are here to learn how to program Continue reading
Cloud Intelligence Throwdown: Amazon vs. Google vs. Microsoft
A closer look at native threat intelligence capabilities built into major cloud platforms and discussion of their strengths and shortcomings.
TLS 1.3 – Internet Security Gets a Boost
Today marks the formal publication of an overhaul of the Transport Layer Security (TLS) protocol. TLS is an Internet standard used to prevent eavesdropping, tampering, and message forgery for various Internet applications. It is probably the most widely deployed network security standard in the world. Often indicated by the small green padlock in a web browser’s address bar1, TLS is used in financial transactions, by medical institutions, and to ensure secure connections in a wide variety of other applications.
We believe the new version of this protocol, TLS 1.3, published as RFC 8446, is a significant step forward towards an Internet that is safer and more trusted.
Under development for the past four years and approved by the Internet Engineering Task Force (IETF) in March 2018, TLS 1.3 addresses known issues with the previous versions and improves security and performance, in particular it is able to establish a session more quickly than its predecessors. Because it is more efficient, TLS 1.3 promises better performance for the billions of users and organizations that use TLS every day. As with every IETF standard, TLS 1.3 was developed through open processes and participation, and included contributions from scores of individuals.
A Detailed Look at RFC 8446 (a.k.a. TLS 1.3)
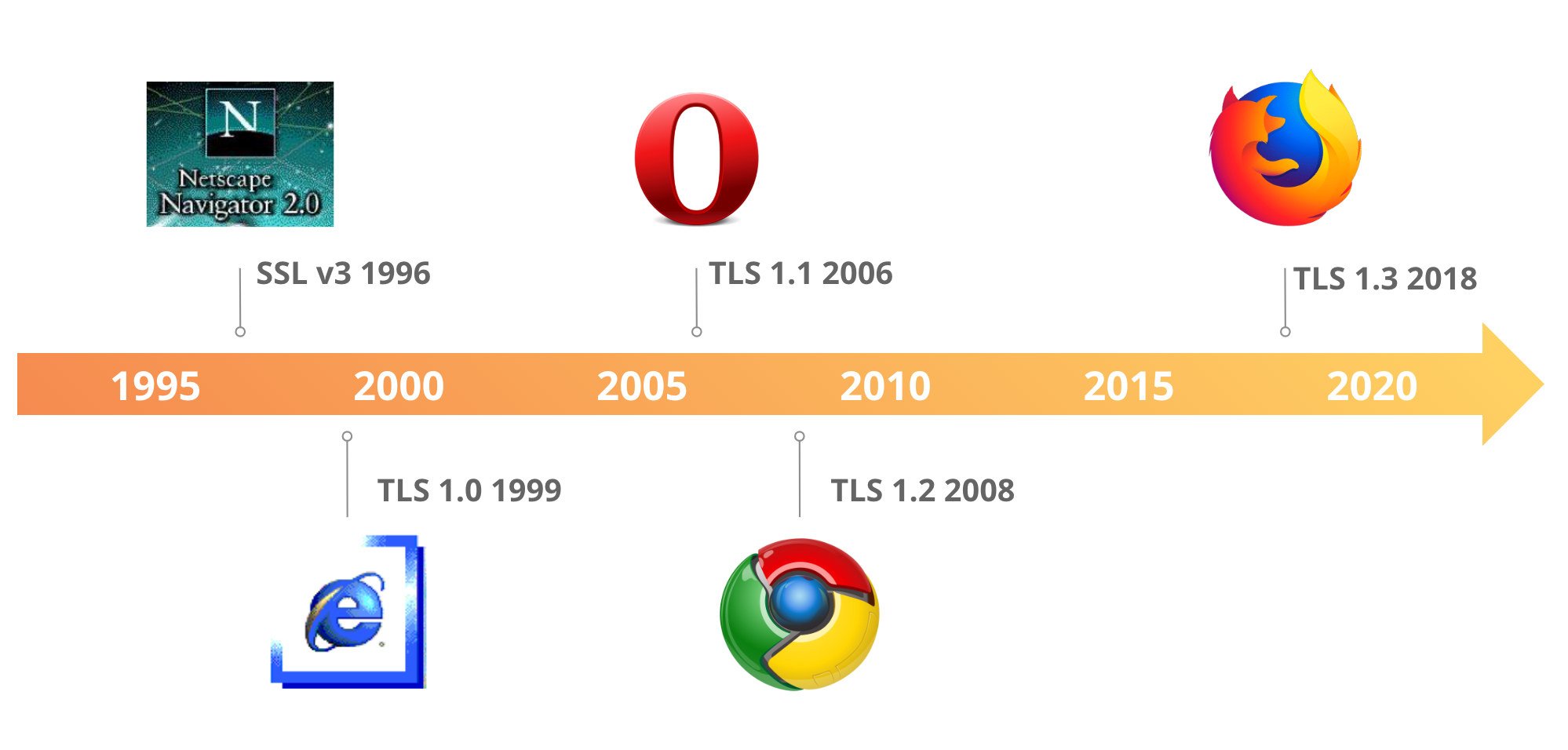
For the last five years, the Internet Engineering Task Force (IETF), the standards body that defines internet protocols, has been working on standardizing the latest version of one of its most important security protocols: Transport Layer Security (TLS). TLS is used to secure the web (and much more!), providing encryption and ensuring the authenticity of every HTTPS website and API. The latest version of TLS, TLS 1.3 (RFC 8446) was published today. It is the first major overhaul of the protocol, bringing significant security and performance improvements. This article provides a deep dive into the changes introduced in TLS 1.3 and its impact on the future of internet security.
An evolution
One major way Cloudflare provides security is by supporting HTTPS for websites and web services such as APIs. With HTTPS (the “S” stands for secure) the communication between your browser and the server travels over an encrypted and authenticated channel. Serving your content over HTTPS instead of HTTP provides confidence to the visitor that the content they see is presented by the legitimate content owner and that the communication is safe from eavesdropping. This is a big deal in a world where online privacy Continue reading
Check Out Our Newest VMware Course: VMware NSX 6.4 Network Design
This course is taught by Atindra Chaturvedi and is 6 hours and 38 minutes long. You view the video on our streaming site, or purchase it at ine.com.
The VMware NSX 6.4 product release expands the capabilities of VMware in the Software Defined Data Center (SDDC) domain. This will be primarily a whiteboard discussion based course with some labs to set the context for the design discussion. Design aspects, limitations and good practice for the overlay network provided by NSX 6.4 will be covered. The latest advances in the data center network provided by Cisco with BGP EVPN and other technologies will be covered from the design perspective as an underlay for the NSX virtualized network. The course is geared to networking and virtualization professionals proficient at a CCNA or CCNP level of experience and knowledge.
H3C Among Top Data Center Ethernet Switch Vendors, Says IHS Markit
 Respondents to IHS Markit’s survey indicated they expect a 1.5x increase in the average number of physical servers in their data centers by 2019.
Respondents to IHS Markit’s survey indicated they expect a 1.5x increase in the average number of physical servers in their data centers by 2019.
Network disaggregation facilitates datacenter and IT modernization [Whitepaper]
We recently partnered with DellEMC to bring you a new IDC whitepaper focused on one of the most critical and relevant considerations for today’s data center leaders and operators. In How Network Disaggregation Facilitates Datacenter and IT Modernization, IDC discusses how digital transformation and the prioritization and modernization of applications are putting pressure on business infrastructure, specifically the network, to modernize and optimize for the digital era.
In brief, the IT world has changed rapidly around the network, demanding automation, scalability and agility. But the network has remained unchanged — monolithic, stagnant and inflexible. The implications for businesses now are not just technological support but economical as well. An inflexible network becomes expensive to scale at the speed of customer expectations and business innovation. Business innovation puts pressure on data centers to offer extensive automation of the entire network life cycle, from provisioning and deployment to day-to-day management and upgrades.
With IT transformation initiatives taking place everywhere to support application needs, the time is now to leverage those initiatives to reassess network architectures and operational models. Network disaggregation is a key architectural step forward to help organizations meet these challenges by offering unprecedented flexibility and agility to support end-to-end Continue reading
Weekly Show 402: Building A Network Automation Framework
On today's Weekly Show we talk about how to build a network automation framework. Scripting repeatable tasks is just the beginning. Guest Ken Celenza joins us to get into the details about automation principles, data models and schemas, testing code, and more.
The post Weekly Show 402: Building A Network Automation Framework appeared first on Packet Pushers.
Civil War in Yemen Begins to Divide Country’s Internet

The latest development in Yemen’s long-running civil war is playing out in the global routing table. The country’s Internet is now being partitioned along the conflict’s battle lines with the recent activation of a new telecom in government-controlled Aden.
Control of YemenNet
The Iranian-backed Houthi rebels currently hold the nation’s capital Sana’a in the north, while Saudi-backed forces loyal to the president hold the port city of Aden in the south (illustrated in the map below from Al Jazeera). One advantage the Houthis enjoy while holding Sana’a is the ability to control Yemen’s national operator YemenNet. Last month, the Houthis cut fiber optic lines severing 80% of Internet service in Yemen.

Launch of AdenNet
In response to the loss of control of YemenNet, the government of President Hadi began plans to launch a new Yemeni telecom, AdenNet, that would provide service to Aden without relying on (or sending revenue to) the Houthi-controlled incumbent operator. Backed with funding from UAE and built using Huawei gear, AdenNet (AS204317) went live in the past week exclusively using transit from Saudi Telecom (AS39386), as depicted below in a view from Dyn Internet Intelligence.

The new Aden-based telecom Continue reading