The Week in Internet News: WhatsApp Looks to Combat the Spread of Fake News
Fake messaging: WhatsApp, the popular messaging tool, will pay researchers up to $50,000 to study the spread of fake news through its platform, notes Mashable.com. The announcement came after reports of mob lynchings in India fueled by false information spread on WhatsApp, reports the Washington Post. India’s government asked the app maker to take immediate action to stop the spread of fake news.
Defining fake news: While we’re still on the topic of fake news, Cambodia’s recent crackdown on false information is raising concerns about press freedom in the country, reports The Guardian. A new directive aimed at fake news on websites and social media allows for violators to be jailed for two years and fined US$1,000, but civil rights groups said the new rules could give “authorities the power to silence individuals at the click of a button.”
Fired by a computer: A Los Angeles worker was recently shown the door by an automated process that seemed to assume he was let go after his original manager was laid off, the BBC reports. The case could raise questions about artificial intelligence processes, but the real fix would be a more intelligent machine, The Conversation says.
AI manages Continue reading
Goodbye, content.ipspace.net
It turns out that while I cannot bring myself to writing or creating other content during the summer break, it feels perfectly fine to be a janitor and fix small things on the web site.
One of the long-outstanding items: get rid of the free content web site that never went where I wanted it to go… one can do only so much in 24 hours. All the features available on content.ipspace.net are now part of the main ipSpace.net web site including pointers to free content and list of free presentations.
During the summer break, I’m publishing blog posts about the projects I’m working on. Regular blog posts will return in autumn.
Scales Tip in Cisco-Arista Legal Battle
In the long-running legal dispute between fierce networking rivals, Arista appears to be successfully fending off Cisco's patent and copyright claims.
Rough Guide to IETF 102
Starting next weekend, the Internet Engineering Task Force will be in Montreal for IETF 102, where over 1,000 engineers will discuss open Internet standards and protocols. The week begins on Saturday, 14 July, with a Hackathon and Code Sprint. The IETF meeting itself begins on Sunday and goes through Friday. We’ll be providing our rough guides on topics of mutual interest to both the IETF and the Internet Society as follows:
- Overview of ISOC @ IETF (this post)
- Internet Infrastructure Resilience
- Internet of Things
- IPv6
- DNSSEC, DANE and DNS Security
- Identity, Privacy, and Encryption
For more general information about IETF 102 see:
Immediately prior to the IETF meeting, ICANN are hosting a DNS Symposium on the theme “Attention, Domain Name System: Your 30-year scheduled maintenance is overdue.” The ICANN DNS Symposium will take place in the same venue as the IETF 102 meeting on Friday 13th July.
Here are some of the activities that the Internet Society is involved in during the week.
Applied Networking Research Workshop (ANRW 2018)
The ACM, IRTF and ISOC Applied Networking Research Workshop will take place on the Monday of IETF week, Continue reading
Using JUNOS Firewall Filters for Troubleshooting & Verification | QFX5110
The Junos firewall filter feature can be a really useful tool for troubleshooting and verification scenarios. I was recently troubleshooting a packet loss fault and I was fairly sure it was an asymmetrical routing issue but I needed a quick way of verifying. And then a colleague said, “hey, how about a firewall filter?”. Of course, assuming IP traffic, we can use a Junos firewall filter to capture specific traffic flows.
Overview
In this scenario, we have a pair of Juniper QFX5110 switches that are both connected to an upstream IP transit provider. They are also connected to a local network via a VMware NSX edge. We’re going to use a firewall filter on QFX1 and QFX2 to identify which QFX is being used for egress traffic and which QFX is being used for ingress traffic. More specifically, the flow is an ICMP flow between a host on 212.134.79.62 and Cloudflare’s DNS service.
Topology
Firewall Filter
So we’re essentially going to create a firewall filter to count specific egress traffic and apply as an import filter on both QFX switches. We’re also going to create another firewall filter to count the return traffic and apply Continue reading
Registration Open for “Cyber Diplomacy Meets InfoSec and Technology” Alongside IETF 102
As we recently announced, the Global Commission on the Stability of Cyberspace (GCSC) will host a lunch panel on “Cyber Diplomacy Meets InfoSec and Technology” alongside IETF 102 on Tuesday, 17 July. Registration opens today in two time slots for global time zone fairness, at 08:00 UTC and 20:00 UTC. Register here.
The Global Commission on the Stability of Cyberspace is developing norms and policy initiatives that intend to counter the risk to the overall security and stability of cyberspace due to rise of offensive cyber-activities, and especially those by states. During this session, the Commission wants to inform and engage with the IETF community on its work so far and the work that is in the pipeline.
The Internet Society is assisting with logistics. Internet Society Chief Internet Technology Officer and GCSC Commissioner Olaf Kolkman will moderate the panel. The panelists are:
- Irina Rizmal, researcher at the DiploFoundation specialized in policy analysis in matters pertaining to national security and defense.
- Bill Woodcock, Commissioner and Executive Director at Packet Clearing House, the non-profit agency that supports critical Internet infrastructure.
- Jeff Moss, Commissioner, founder of Black Hat and Defcon, member of the DHS security council, Continue reading
Comparing Serverless Performance for CPU Bound Tasks
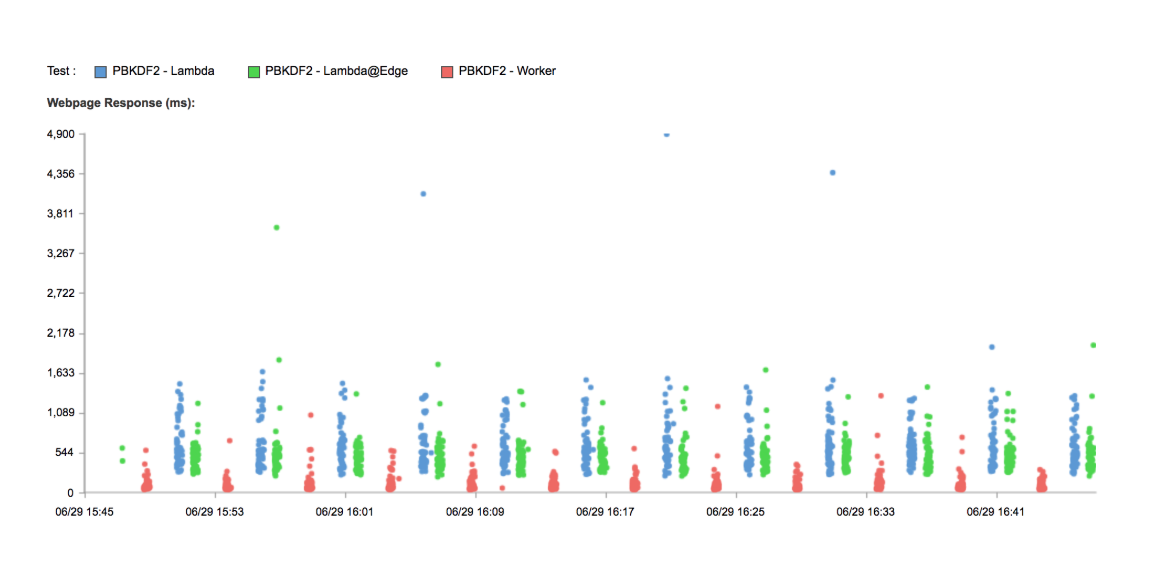
This post is a part of an ongoing series comparing the performance of Cloudflare Workers with other Serverless providers. In our past tests we intentionally chose a workload which imposes virtually no CPU load (returning the current time). For these tests, let's look at something which pushes hardware to the limit: cryptography.
tl;dr Cloudflare Workers are seven times faster than a default Lambda function for workloads which push the CPU. Workers are six times faster than Lambda@Edge, tested globally.
Slow Crypto
The PBKDF2 algorithm is designed to be slow to compute. It's used to hash passwords; its slowness makes it harder for a password cracker to do their job. Its extreme CPU usage also makes it a good benchmark for the CPU performance of a service like Lambda or Cloudflare Workers.
We've written a test based on the Node Crypto (Lambda) and the WebCrypto (Workers) APIs. Our Lambda is deployed to with the default 128MB of memory behind an API Gateway in us-east-1, our Worker is, as always, deployed around the world. I also have our function running in a Lambda@Edge deployment to compare that performance as well. Again, we're using Catchpoint to test from hundreds of locations around Continue reading
How To Minikube + Cloudflare

The following is a guest blog post by Nathan Franzen, Software Engineer at StackPointCloud. StackPointCloud is the creator of Stackpoint.io, the leading multi-cloud management platform for cloud native workloads. They are the developers of the Cloudflare Ingress Controller for Kubernetes.
Deploying Applications on Minikube with Argo Tunnels
This article assumes basic knowledge of Kubernetes. If you're not familiar with Kubernetes, visit https://kubernetes.io/docs/tutorials/kubernetes-basics/ to learn the basics.
Minikube is a tool which allows you to run a Kubernetes cluster locally. It’s not only a great way to experiment with Kubernetes, but also a great way to try out deploying services using a reverse tunnel.
At Cloudflare, we've created a product called Argo Tunnel which allows you to host services through a tunnel using Cloudflare as your edge. Tunnels provide a way to expose your services to the internet by creating a connection to Cloudflare's edge and routing your traffic over it. Since your service is creating its own outbound connection to the edge, you don’t have to open ports, configure a firewall, or even have a public IP address for your service. All traffic flows through Cloudflare, blocking attacks and intrusion attempts before they ever make it to Continue reading
Redirecting DNS Requests to Umbrella with FTD
A few days ago I shared an article that described redirecting DNS requests with ASA. A good use case for this might be if an organization is using Cisco Umbrella but there is no way to get every host is pointed toward the correct DNS server(s) in a timely manner. In that case, a configuration of destination NAT in the ASA can force those misconfigured clients to use one of the OpenDNS addresses.
This article is very similar, but we will share a method for doing this with Firepower Threat Defence. The concept is the same but all configuration is done in Firepower Management Console. Before starting on the NAT configuration, it is important to configure the following network objects (Objects, Object Management, Network).
- obj_any – 0.0.0.0/0
- Umbrella1 – 208.67.220.220
- Umbrella2 – 208.67.222.222
It is also important to confirm the existence of two port objects (Objects, Object Management, Network).
- DNS_over_TCP – TCP Port 53
- DNS_over_UDP – UDP Port 53
Most of the configuration will be done on the NAT policy for the device we are managing (Device, NAT, select edit for the appropriate NAT policy).
We will need four rules that Continue reading
Redirecting DNS Requests to Umbrella with FTD
A few days ago I shared an article that described redirecting DNS requests with ASA. A good use case for this might be if an organization is using Cisco Umbrella but there is no way to get every host is pointed toward the correct DNS server(s) in a timely manner. In that case, a configuration of destination NAT in the ASA can force those misconfigured clients to use one of the OpenDNS addresses.
This article is very similar, but we will share a method for doing this with Firepower Threat Defence. The concept is the same but all configuration is done in Firepower Management Console. Before starting on the NAT configuration, it is important to configure the following network objects (Objects, Object Management, Network).
- obj_any – 0.0.0.0/0
- Umbrella1 – 208.67.220.220
- Umbrella2 – 208.67.222.222
It is also important to confirm the existence of two port objects (Objects, Object Management, Network).
- DNS_over_TCP – TCP Port 53
- DNS_over_UDP – UDP Port 53
Most of the configuration will be done on the NAT policy for the device we are managing (Device, NAT, select edit for the appropriate NAT policy).
We will need four rules that Continue reading
Network Notes: EIGRP
EIGRP is an 'advanced' distance vector routing protocol and is the evolution of IGRP. Originally EIGRP was a Cisco proprietary protocol but in 2013 Cisco announced its intention to make EIGRP on open standard. At the time of writing there is an only informational RFC: RFC7868. ...continue reading
We’ve Added New Dates To Our Bootcamp Calendar!

CCIE Routing & Switching:
Online Graded Practice Lab
January 2-4
April 15-18
April 16-19
May 28-31
5 Day Bootcamp
January 7-11
Written Exam Bootcamp
January 7-11
April 15-19
June 24-28
Lab Exam Bootcamp
January 28 – February 3
February 4-10
February 25 – March 3
March 25-31
May 13-19
June 10-16
June 24-30
CCIE Security:
5 Day Bootcamp
January 7-11
Written Exam Bootcamp
January 14-18
March 25-29
Lab Exam Bootcamp
January 21-27
February 25 – March 3
April 1-7
June 17-23
CCIE Data Center:
Lab Exam Bootcamp
January 7-13
February 4-10
March 18-24
April 29 – May 5
June 17-23
CCIE Service Provider:
Lab Exam Bootcamp
March 18-24
June 3-9
CCIE Collaboration:
Lab Exam Bootcamp
January 28 – February 3
March 4-10
April 8-14
CCNP Routing & Switching:
7 Day Bootcamp
January 28 – February 3
February 11-15
March 11-17
April 29 – May 5
May 13-17
CCNA Routing & Switching:
5 Day Bootcamp
February 25 – March 1
April 15-19
June 10-14
CCNA Security:
5 Day Bootcamp
April 1-5
June 24-28
Visit our Bootcamps Site to purchase your course today!
Weekend Reads 070618
The world of scholarly communication is broken. Giant, corporate publishers with racketeering business practices and profit margins that exceed Apple’s treat life-saving research as a private commodity to be sold at exorbitant profits. Only around 25 per cent of the global corpus of research knowledge is ‘open access’, or accessible to the public for free and without subscription, which is a real impediment to resolving major problems, such as the United Nations’ Sustainable Continue reading
Kernel of Truth episode 03 — Linux: the kernel, the community & beyond
Listen, you can’t name an open networking podcast “Kernel of Truth,” and NOT have an episode dedicated to the Linux kernel! So we got two of the brightest, most enthusiastic Linux experts we know into the recording booth and let them wax poetic about the language of the data center. As I soon found out, it’s harder to get Linux fans to STOP talking about Linux that it is to get them going — but hey, that just makes my job as host a lot easier! There’s nothing like listening to knowledgeable people discuss something they’re passionate about, and that’s what we’ve got in store for you.
In this episode, I’m joined by Roopa Prabhu, leader of the kernel team at Cumulus Networks, and Shrijeet Mukherjee, Cumulus’ former VP of Engineering. Specifically, our discussion revolves around the Linux kernel and Linux community. We get into some pretty interesting questions: why Linux in the data center? What has Cumulus contributed to the kernel? How has the prolific Linux community evolved? What the heck is a “boffin”?? I’m not a fan of spoilers, (thanks for ruining Avengers: Infinity War for me, Twitter!) so I’ll let you guys tune in and find Continue reading
Small Wireless Providers Defend Huawei’s Business in the U.S.
 Wireless carriers say not being able to use Huawei equipment would “gravely impair” their ability to do business. And they can’t afford to “rip and replace” their equipment.
Wireless carriers say not being able to use Huawei equipment would “gravely impair” their ability to do business. And they can’t afford to “rip and replace” their equipment.
Caring for Fibre Optic Cables. Damaged is Worse Than Broken
Why Replacing The Fibre Optic Patch Lead Often Fixes Network ProblemsNetQ is now a 2018 “New Product” Award Winner!

Cumulus NetQ is on FIRE!!
Just one year ago, Cumulus launched a new product that fundamentally changes the way organizations validate and troubleshoot not just their network, but the entire Linux ecosystem as a whole. The product was named NetQ (think Network Query). It provides deep insight on the connectivity of all network devices either now or in the past — including all switches, Linux hosts, inside Linux hosts (Containers, direct interaction with container orchestration tools like Kubernetes, VMs, Openstack environment) and any other devices running a Linux-based operating system connected to the network. No more manual box-by-box troubleshooting, no more wondering what happened last night, no more pulling cables to find where the issue was stemming from, no more finger pointing, no more human-led misconfigurations and no more frustration of not having sight past the edge of the network.
Instead, Cumulus NetQ, the agent-based technology that runs on anything Linux, changes all that. NetQ brings the efficiencies of web-scale to network operations with an algorithmic, preventive, centralized telemetry system built for the modern automated cloud network. NetQ aggregates and maintains data from across all Linux nodes in the data center in a time-series database, making the fabric-wide events, Continue reading
