D2C237: Managing Medical IoT Devices on AWS
In this podcast episode, Randy Horton from Orthogonal and Ian Sutcliffe from AWS discuss the complexities of supporting regulated medical devices in the cloud. They explore the challenges of adhering to regulations, the importance of security, and the need for robust frameworks. The conversation highlights the non-prescriptive nature of regulations, encouraging best practices rather than... Read more »Bring Network and Security Teams Together by Asking the Right Questions
Finding the balance point of performance and security that best serves the organization can only be done when both the networking and security teams work together.NAN058: The Story of containerlab with Roman Dodin (Part 2)
Welcome back for Part 2 of Eric’s interview with Roman Dodin, co-creator of containerlab. Roman describes containerlab as a “lab as code” tool that quickly and easily creates virtual networking topologies. With increased automation and containerization in network engineering, the tool’s popularity has exploded. We talk about how folks contribute to containerlab’s development and what... Read more »Nile Bets on AI Networking with Performance Guarantees
Nile offers consumption-based pricing, masks all the legacy complexity of operating a network, and makes use of AI to bring the benefits of the cloud delivery model to the network.How Anycast VTEP Broke My Lab And What I Learned
I’m preparing a massive blog post on vPC in the context of VXLAN/EVPN and while doing so I accidentally broke my lab. What a great learning experience! I thought I would share it with you and how to perform troubleshooting of this scenario.
My topology looks like this:
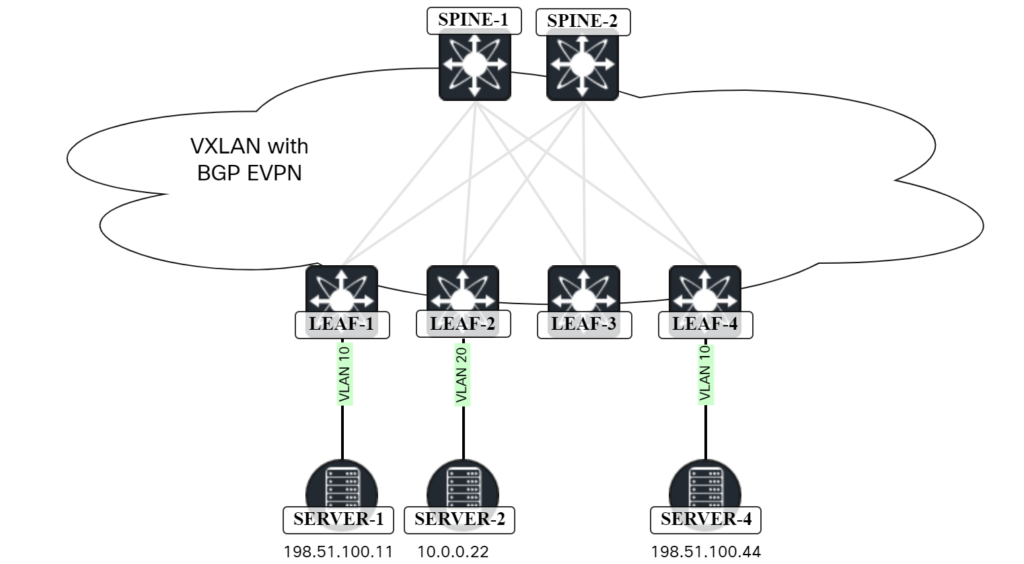
Before I made any changes, there was full connectivity between these hosts, meaning that both bridging and routing was working. I then changed the loopback1 (NVE source interface) configuration of Leaf-1 and Leaf-2 to add a secondary IP. This was the initial configuration:
! Leaf-1 interface loopback1 description VTEP ip address 203.0.113.1/32 ip router ospf UNDERLAY area 0.0.0.0 ip pim sparse-mode ! Leaf-2 interface loopback1 description VTEP ip address 203.0.113.2/32 ip router ospf UNDERLAY area 0.0.0.0 ip pim sparse-mode
This then changed to:
! Leaf-1 interface loopback1 description VTEP ip address 203.0.113.1/32 ip address 203.0.113.12/32 secondary ip router ospf UNDERLAY area 0.0.0.0 ip pim sparse-mode ! Leaf-2 interface loopback1 description VTEP ip address 203.0.113.2/32 ip address 203.0.113.12/32 secondary ip router ospf UNDERLAY area 0.0.0.0 ip pim Continue reading
FRRouting RIB and FIB
This is how we described the interactions between routing protocol tables, RIB, and FIB in the ancient times:
- Routing protocols compute the best paths to all known prefixes.
- These paths compete for entry in the routing table. The path(s) with the lowest administrative distance win.
- The entries from the routing table are fully evaluated (in particular, their next hops) and entered in the forwarding table.
Let’s use a simple BGP+OSPF network to illustrate what I’m talking about:
FRRouting RIB and FIB
This is how we described the interactions between routing protocol tables, RIB, and FIB in the ancient times:
- Routing protocols compute the best paths to all known prefixes.
- These paths compete for entry in the routing table. The path(s) with the lowest administrative distance win.
- The entries from the routing table are fully evaluated (in particular, their next hops) and entered in the forwarding table.
Let’s use a simple BGP+OSPF network to illustrate what I’m talking about:
HS068: What’s the Point of Having a Tech Strategy?
What does having a tech strategy actually do for an organization? In today’s episode, Greg and Johna highlight how a good tech strategy benefits a company: creates a foundation of first principles, reduces bias in vendor decisions, better allocates human resources, kills bad ideas, sunsets projects, and makes meetings a little more enjoyable and harmonious.... Read more »My Experience with IP Fabric Automated Network Assurance Platform

I've been following IP Fabric for some time now, checking out their updates and reading their blog posts. It made me curious to want to give their platform a try myself. So, I did just that and thought it'd be helpful to share my thoughts and experiences with you.
If you're curious about IP Fabric too, they offer a 90-day lab license, which is a great way to get hands-on with the platform. The nice people over at IP Fabric set me up with a trial license and I found the setup process to be very straightforward. In fact, it took me less than an hour to get everything up and running.
What we will cover?
- What is IP Fabric?
- Installation
- Automated Network Discovery
- What is a Snapshot?
- Topology Visualization
- Intent-based Verification
- Compliance and Security Checks
- Other Useful Features
- Closing thoughts
What is 'IP Fabric Automated Continue reading
PP006: Effective Security for Small IT Shops
This episode is for IT professionals who work in small- to medium-sized businesses and are expected to handle cybersecurity on top of issues like “my camera isn’t working on Zoom.” Guest Joe Stern has been filling this role for an 80-person company for almost 30 years. We talk about how he prioritizes risks, security tools... Read more »3GPP Standards for Satellite IoT – Catalyst for Progression?
With low earth orbit (LEO) satellites fast becoming the norm and 3GPP unifying telecom standards around the globe, the satellite IoT and machine-to-machine (M2M) sector ought to be looking at a bright horizon. But is this the case?Interface EBGP Sessions on Arista EOS
Arista EOS and Cisco Nexus OS got interface EBGP sessions years after Cumulus Linux. While they’re trivially easy to configure on FRRouting (the routing daemon used by Cumulus Linux), getting them to work on Arista EOS is a bit tricky.
To make matters worse, my Google-Fu failed me when I tried to find a decent step-by-step configuration guide; all I got was a 12-minute video full of YouTube ads. Let’s fix that.
Interface EBGP Sessions on Arista EOS
Arista EOS and Cisco Nexus OS got interface EBGP sessions years after Cumulus Linux. While they’re trivially easy to configure on FRRouting (the routing daemon used by Cumulus Linux), getting them to work on Arista EOS is a bit tricky.
To make matters worse, my Google-Fu failed me when I tried to find a decent step-by-step configuration guide; all I got was a 12-minute video full of YouTube ads. Let’s fix that.
Tech Bytes: Protecting Connected Medical Devices With Palo Alto Networks IoT Security (Sponsored)
Medical devices are an essential element of patient care. They’re also network-connected devices that need resilient connectivity and security. On today’s Tech Bytes we examine the challenges of supporting and securing connected medical devices, including threats, vulnerabilities, and regulatory frameworks. We’ll also discuss strategies and best practices to manage medical device risks and ensure the... Read more »NB470: NetBox Labs Adds On-Prem Support; ASML Vs. The Netherlands
This week on Network Break we discuss a new on-prem version of NetBox Labs’ source-of-truth software with enterprise support, why Selector AI is adding an LLM to its operations and observability product, and whether a new Web application firewall from Cloudflare can protect LLMs against malicious prompts. Viavi Solutions consolidates the network testing space with... Read more »AI Assistants

I have written elsewhere about the danger of AI assistants leading to mediocrity. Humans tend to rely on authority figures rather strongly (see Obedience to Authority by Stanley Milgram as one example), and we often treat “the computer” as an authority figure.
The problem is, of course, Large Language Models—and AI of all kinds—are mostly pattern-matching machines or Chinese Rooms. A pattern-matching machine can be pretty effective at many interesting things, but it will always be, in essence, a summary of “what a lot of people think.” If you choose the right people to summarize, you might get close to the truth. Finding the right people to summarize, however, is beyond the powers of a pattern-matching machine.
Just because many “experts” say the same thing does not mean the thing is true, valid, or useful.
AI assistants can make people more productive, at least in terms of sheer output. Someone using an AI assistant will write more words per minute than someone who is not. Someone using an AI assistant will write more code daily than someone who is not.
But is it just more, or is it better?
Measuring the mediocratic effect of using AI systems, even as Continue reading
Running netlab and BGP Labs on Apple Silicon
I usually say that you cannot run netlab on Apple silicon because the vendors don’t provide ARM images. However, when I saw an ARM version of the FRRouting container, I started wondering whether I could run the BGP labs (admittedly only on FRR containers) on my M2 MacBook Pro.
TL&DR: Yes, you can do that.
Now for the recipe:
Running netlab and BGP Labs on Apple Silicon
I usually say that you cannot run netlab on Apple Silicon because the vendors don’t provide ARM images. However, when I saw an ARM version of the FRRouting container, I wondered whether I could run the BGP labs (admittedly only on FRR containers) on my M2 MacBook Pro.
TL&DR: Yes, you can do that.
Now for the recipe: