Arista’s New Switch Features Barefoot’s Programmable Tofino Chip
 The switches are not only programmable, they're re-programmable, making them available for future use cases, using the same device.
The switches are not only programmable, they're re-programmable, making them available for future use cases, using the same device.
Reaction: The Power of Open APIs
Disaggregation, in the form of splitting network hardware from network software, is often touted as a way to save money (as if network engineering were primarily about saving money, rather than adding value—but this is a different soap box). The primary connections between disaggregation and saving money are the ability to deploy white boxes, and the ability to centralize the control plane to simplify the network (think software defined networks here—again, whether or not both of these are true as advertised is a different discussion).
But drivers that focus on cost miss more than half the picture. A better way to drive the value of disaggregation, and the larger value of networks within the larger network technology sphere, is through increased value. What drives value in network engineering? It’s often simplest to return to Tannenbaum’s example of the station wagon full of VHS backup tapes. To bring the example into more modern terms, it is difficult to beat the bandwidth of an overnight box full of USB thumb drives in terms of pure bandwidth.
In this view, networks can primarily be seen as a sop to human impatience. They are a way to get things done more quickly. In the Continue reading
OutSystems Raises $360M to Expand Low-Code Development Platform
 The company partnered with Microsoft, AWS, Pivotal, and Docker to determine how to take its low-code philosophy to containers.
The company partnered with Microsoft, AWS, Pivotal, and Docker to determine how to take its low-code philosophy to containers.
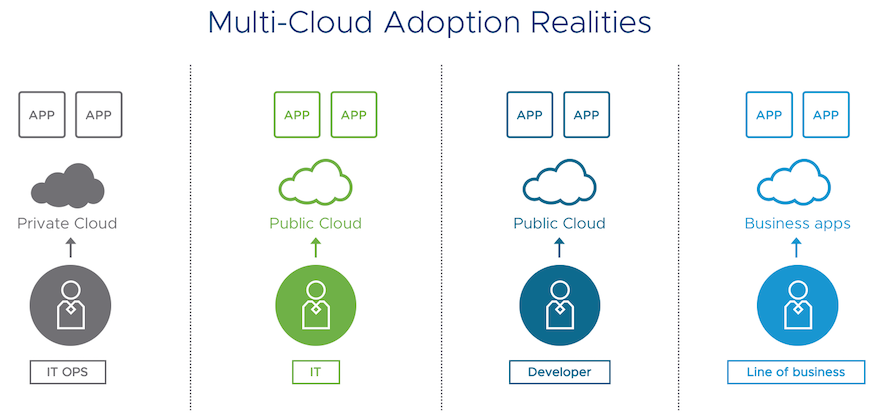
NSX Cloud: A New and Improved Model for Multi-cloud Networking and Security
Remember the headlines years ago, asking what would win: public cloud or private cloud? Or hybrid cloud? And everyone had different definitions for each? Of course, as it often is with technology trends, our “or” questions have “and” answers. Let’s imagine current day, where you might see one group running an application on-premises with absolutely zero plans for it to go anywhere. In a far-away land, several desks or cubes away, some savvy developers are building a new innovation – it could be a new service type, a new app, a new feature on a website – directly in AWS. A few desks further, and someone indeed may believe that AWS app belongs back on premises. Finally, in the same organization, an IT group is looking at how Microsoft Azure is offering a compelling alternative to hosting an app they’re just not interested in maintaining anymore.
This is just one example of a potential multi-cloud scenario. Each organization’s specific needs are different, yet this array of parallel cloud uses is not a foreign one to many organizations. In fact, in this year’s “State of the Cloud” report, RightScale found that organizations use five clouds on average.
White Paper: Secure and Cost-Effective Digital Transformation
 A new white paper from Zscaler introduces a powerful solution for providing an efficient and secure experience between users and cloud/SaaS.
A new white paper from Zscaler introduces a powerful solution for providing an efficient and secure experience between users and cloud/SaaS.
Related Stories
Introducing DNS Resolver for Tor


In case you haven’t heard yet, Cloudflare launched a privacy-first DNS resolver service on April 1st. It was no joke! The service, which was our first consumer-focused service, supports emerging DNS standards such as DNS over HTTPS:443 and TLS:853 in addition to traditional protocols over UDP:53 and TCP:53, all in one easy to remember address: 1.1.1.1.
As it was mentioned in the original blog post, our policy is to never, ever write client IP addresses to disk and wipe all logs within 24 hours. Still, the exceptionally privacy-conscious folks might not want to reveal their IP address to the resolver at all, and we respect that. This is why we are launching a Tor hidden service for our resolver at dns4torpnlfs2ifuz2s2yf3fc7rdmsbhm6rw75euj35pac6ap25zgqad.onion and accessible via tor.cloudflare-dns.com.
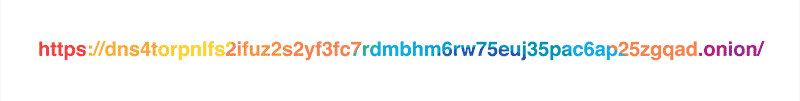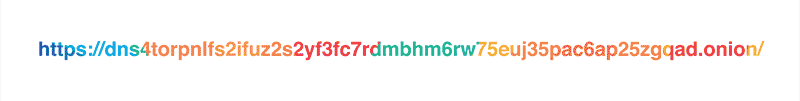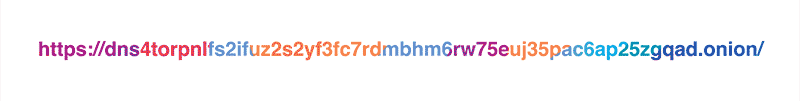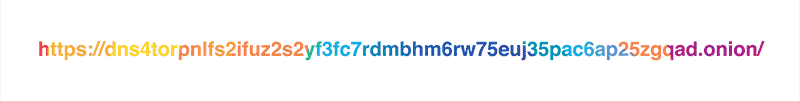
NOTE: the hidden resolver is still an experimental service and should not be used in production or for other critical uses until it is more tested.
Crash Course on Tor
What is Tor?
Imagine an alternative Internet where, in order to connect to www.cloudflare.com, instead of delegating the task of finding a path to our servers to your internet provider, you had to go through the following Continue reading
The Internet of Food is on the table
The food sector is one of the few large remaining sectors that have not been radically transformed by new technologies yet. Up to now, the Internet in particular was not involved as much as other sectors. However, in a not-too-distant future, the everyday question “what’s for dinner?” will be answered by algorithms managed by the next generation of food companies. When these algorithms are governing the food industry, they will also be governing people as well as their health and well-being.
As food is online, we will start realizing how important network design has become for our existence. The question “what’s for dinner?” will be replaced by “who decides what we eat?”. The Internet Society members, Johan Jörgensen, Michael Daun and Patrik Fältström, assure that this is the most profound question that the tech revolution has asked so far. That is the reason why they created a Special Interest Group on Internet of Food to focus on general discussions around the future infrastructure and standards for the digital world of food.
 The project leader Johan Jörgensen explains: “The initial work in the SIG has been about discussing which standards already exist in the food Continue reading
The project leader Johan Jörgensen explains: “The initial work in the SIG has been about discussing which standards already exist in the food Continue reading
Watch live – June 6 panel on “Innovation, security, and the Internet of Things (IoT)” in Ottawa
As a side event before the 2018 G7 Summit this week in Canada, tomorrow, 6 June 2018, the Internet Society will hold a panel to not only talk about the risks and opportunities the Internet of Things (IoT) brings, but also what policy makers can do to build a connected future for everyone.
The panel, Innovation, security, and the Internet of Things, will take place in Ottawa Ontario. If you’re in Ottawa, you can join us from 7:30 to 9:30 a.m. on Wednesday, 6 June, at the Alt Hotel Ottawa at 185 Slater St. If you’re somewhere else, the event will be
livestreamed.
Moderator David Akin (Global News) will facilitate a discussion between:
- Jeff Wilbur, Director, Online Trust Alliance
- Katie Watson, Policy Advisor, Internet Society
- Jacques Latour, Chief Technology Officer, Canadian Internet Registration Authority
- Mike Hoye, Engineering Community Manager, Mozilla
While the opportunities these connected devices can bring us are virtually unprecedented, the steps we must go through to protect ourselves online can feel overwhelming. At the Internet Society, we believe in a future where manufactures, software developers and service providers put people first and ensure user’s privacy and security is their top priority.
To understand Continue reading
Amazon, Google Vulnerable to Zip Slip, Says Snyk Security Research
 The security startup maintains a massive database of vulnerabilities in open source libraries.
The security startup maintains a massive database of vulnerabilities in open source libraries.
Druva Buys CloudRanger, Grows Its AWS-Native Backup and Disaster Recovery Tech
 The acquisition follows an $80 million funding round and signals a growth trajectory for the SD-storage company.
The acquisition follows an $80 million funding round and signals a growth trajectory for the SD-storage company.
Inside the Beach House Connecting the World’s Internet
Video shows just how boring networking is.
