Spectre Next Gen Bugs Hit Intel CPUs, Cisco Catches Cryptojacking Threats
 Intel classified four of the new flaws as “high risk” and four as “medium,” and it's working on patches.
Intel classified four of the new flaws as “high risk” and four as “medium,” and it's working on patches.
Arista Predicts 20% Growth for the Remainder of 2018, But Stock Drops
 Arista reported excellent earnings for its Q1 2018, but Wall Street, with its insatiable appetite, is concerned the company's growth rates are slowing.
Arista reported excellent earnings for its Q1 2018, but Wall Street, with its insatiable appetite, is concerned the company's growth rates are slowing.
SDxCentral’s Weekly Roundup — May 4, 2018
 Google releases workflow creation beta; Deutsche Telekom puts 5G technology on German soil; HPE and Red Hat collaborate on containers.
Google releases workflow creation beta; Deutsche Telekom puts 5G technology on German soil; HPE and Red Hat collaborate on containers.
Show 388: The Future Of Networking With Kyle Mestery
The Future of Networking series continues with guest Kyle Mestery.
Kyle is well known to many corners of the networking community including the open source community. He recently re-joined Cisco as a Distinguished Engineer.
We talk with Kyle to get his take on where the packets are flowing over the next several years, including the tech conference scene, open-source networking, the proliferation of open-source networking OSs, what’s inside Open Network Linux (ONL), and cloud-native network functions virtualization.
Sponsor: ThousandEyes
ThousandEyes gives you performance visibility from every user to every app over any network, both internal and external, so you can smoothly migrate to the cloud, transform your WAN, troubleshoot faster and deliver exceptional user experiences. Sign up for a free account at thousandeyes.com/packetpushers and choose a free ThousandEyes t-shirt.
Show Links:
Silicon Loons.com – Kyle’s blog
Network Service Mesh – GitHub
Three Years On: Open Standards, Open Source, Open Loop – Cisco Systems
Verizon Launches Virtual Service Bundles – Light Reading
The post Show 388: The Future Of Networking With Kyle Mestery appeared first on Packet Pushers.
Dogfooding Cloudflare Workers
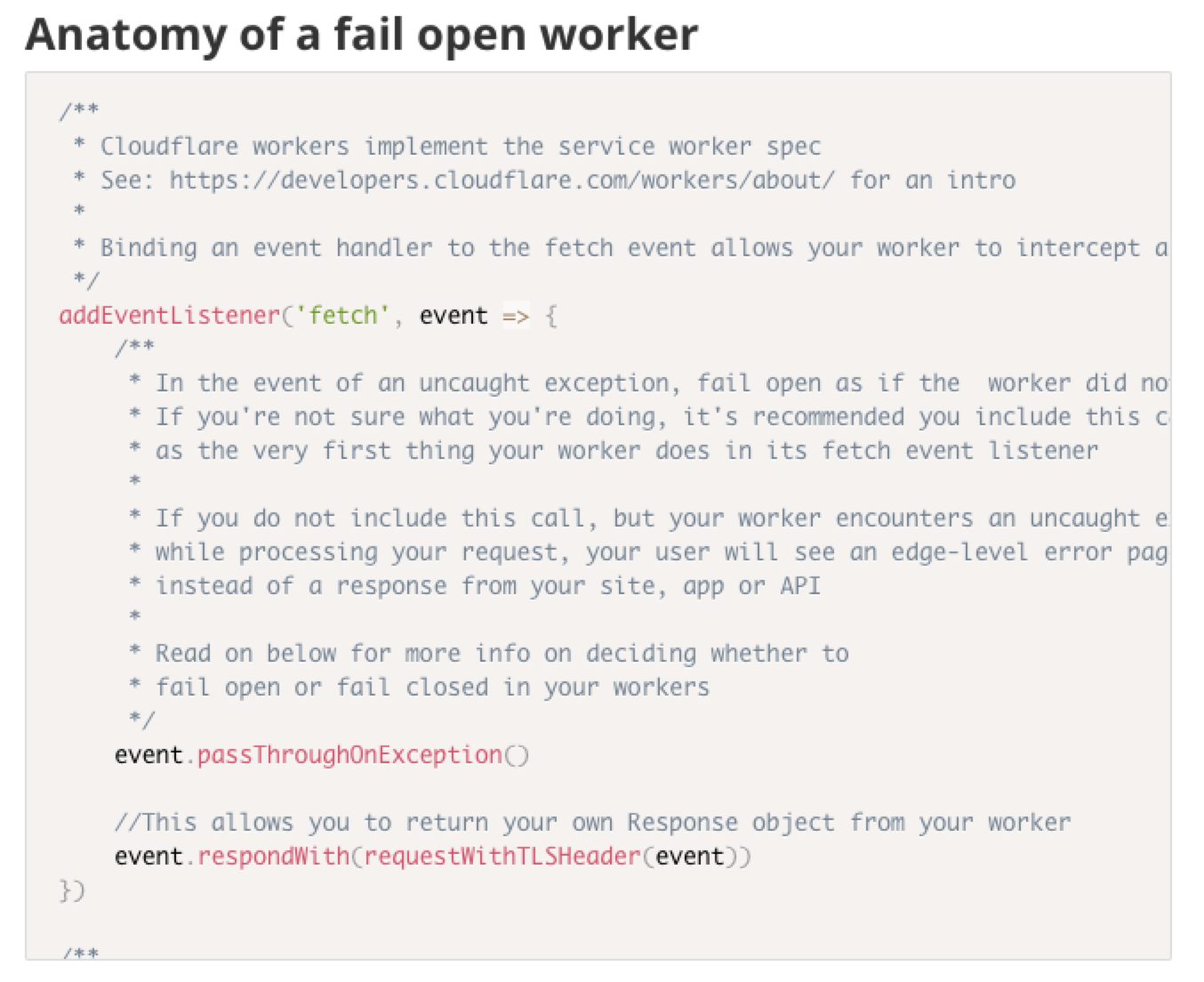
On the WWW team, we’re responsible for Cloudflare’s REST APIs, account management services and the dashboard experience. We take security and PCI compliance seriously, which means we move quickly to stay up to date with regulations and relevant laws.
A recent compliance project had a requirement of detecting certain end user request data at the edge, and reacting to it both in API responses as well as visually in the dashboard. We realized that this was an excellent opportunity to dogfood Cloudflare Workers.
Deploying workers to www.cloudflare.com and api.cloudflare.com
In this blog post, we’ll break down the problem we solved using a single worker that we shipped to multiple hosts, share the annotated source code of our worker, and share some best practices and tips and tricks we discovered along the way.
Since being deployed, our worker has served over 400 million requests for both calls to api.cloudflare.com and the www.cloudflare.com dashboard.
The task
First, we needed to detect when a client was connecting to our services using an outdated TLS protocol. Next, we wanted to pass this information deeper into our application stack so that we could act upon it and Continue reading
The Future is About the Business, Not the Technology
There has been plenty of change throughout the evolution of information technology. Now it's time for the corporate world to catch up and reshape how they do business and serve their customers.
Don’t Miss Keith Bogart’s May CCNA Kickoff!
It’s that time again! Tune in on May 7 at 10 am PST/ 1 pm EST for our monthly CCNA Kickoff session with expert instructor Keith Bogart.
This is a FREE session in which Keith (CCIE #4923) will present everything you need to know to get started on your CCNA journey.
What Keith will cover in this months webinar:
- How to get started by making a study schedule
- Strategies to prevent you from becoming overwhelmed throughout the exam process
- CCNA certification test format
- Which topics to study, and how in depth
- What study tools will be the most useful
- What to expect when you walk into the testing center
You can view this, and all of our other webinars here.
Oracle Cloud Drives The Factory’s Car Marketplace Into the Digital Age
 The pre-owned car marketplace app sometimes processes upwards of 20,000 vehicles in a busy weekend.
The pre-owned car marketplace app sometimes processes upwards of 20,000 vehicles in a busy weekend.
European Agenda on Digital for Development: Can the Multistakeholder Approach Help?
The year 2017 was an important milestone in moving forward the European agenda for Digital for Development (D4D). The European Commission (EC) paper on mainstreaming digital technologies into EU development policy and the European Council conclusions on Digital for Development have activated the European development community to share opinions and ideas on how to help bridge the global digital divide.
In the past month, we have had a couple of open events in Brussels to discuss this important issue. The European Parliament’s EPP group hosted a public hearing on Digitalisation for Development to collect ideas and to push for more progress. Two weeks later, the EC held the first multistakeholder meeting for Digital4Development with a focus on Africa.
Building a Balanced Agenda
There are a number of pillars of activities that most stakeholders agree on. These include Internet access with a focus on last mile; Internet as an enabler across different sectors; skills; and entrepreneurship. During the recent meetings, the EC, the national development agencies and the private sector showcased impressive and innovative digitalisation programmes.
However, several stakeholders pointed out that while it is important to continue to invest in Internet access, this is no longer enough. We need Continue reading
Short Take – Cisco Field Area Networking
In this Network Collective Short Take, guest commentator Nick Buraglio shares his thoughts on field area networking after watching Cisco’s presentation on the topic at Networking Field Day 17. You can see the original NFD17 presentation here: https://vimeo.com/253197120
The post Short Take – Cisco Field Area Networking appeared first on Network Collective.
Network Automation with Brigade on Software Gone Wild
David Barroso was sick-and-tired of using ZX Spectrum of Network Automation and decided to create an alternative with similar functionality but a proper programming language instead of YAML dictionaries masquerading as one. The result: Brigade, an interesting network automation tool we discussed in Episode 90 of Software Gone Wild.
Notes:
- If you want to test-drive Brigade, start here;
- To get the references at the end of our chat, watch this and this;
- David will talk about Brigade in autumn 2018 session of Building Network Automation Solutions online course.
Software-Defined Storage: The 5 Must-Haves You Need in Your Toolkit
 Software-defined storage is rising to the top of the storage market, but before selecting a solution, it’s important to determine the features and capabilities for your specific set of needs.
Software-defined storage is rising to the top of the storage market, but before selecting a solution, it’s important to determine the features and capabilities for your specific set of needs.
Radware Reports Third Consecutive Quarter of Double Digit Growth
 The company’s recent transition to a SaaS subscription model proves favorable as it reported an 11 percent increase in revenue year over year, along with several deals in the first quarter of 2018.
The company’s recent transition to a SaaS subscription model proves favorable as it reported an 11 percent increase in revenue year over year, along with several deals in the first quarter of 2018.
NetQ + Kubernetes: bringing container visibility with the leading container orchestrator
Businesses today have to get applications to market faster than ever, but with the same or less budget. Because of this requirement, modern data centers are evolving to support a change in application delivery. In order to get applications to market faster and increase revenue, applications that were once built as one monolithic entity are becoming segmented and deployed separately, communicating amongst themselves. The pieces of applications, sometimes referred to as microservices, are often deployed as containers. This results in much faster deployment and a quicker update cycle. However, the network teams operating the infrastructure supporting the applications often have no visibility into how their networks are being utilized, and thus are making design, operations and troubleshooting decisions blindly. Now, Cumulus NetQ provides this visibility from container deployments all the way to the spine switches and beyond — accelerating operations and providing the crucial information to efficiently design and operate the networks running containers.
Understanding the challenges of container management
Traditionally, the new application design and deployment method using containers makes operating and managing the infrastructure to support them very challenging. The containers often have to talk with each other within or across data centers or to the outside world. An Continue reading
