BGP in EVPN-Based Data Center Fabrics – Take 2
My BGP in EVPN-Based Data Center Fabrics blog post generated numerous comments from engineers disagreeing with my views on using IBGP-over-EBGP.
As usual, there were three kinds of comments:
Read more ...MPLS 101 – Dynamic routing with BGP
In our last post we talked about how to make the MPLS control plane more dynamic by getting rid of static LSPs and adding in LDP to help advertise and distribute LSPs to all MPLS speaking routers. However – even once got LDP up and running, we still had to tell the routers to use a given LSP. In the last post, we accomplished this by adding recursive static routes in the inet.0 table to force the routers to recurse to the inet.3 table where the MPLS LSPs lived. In this post, we’re going to tackle getting rid of the static routes and focus on replacing it with a dynamic routing protocol – BGP.
So to start off with, let’s get our lab back to a place where we can start. To do that, we’re going to load the following configuration on each router show in the following lab topology…

interfaces {
ge-0/0/0 {
enable;
unit 0 {
family inet {
address 10.2.2.0/31;
}
}
}
ge-0/0/1 {
enable;
unit 0 {
family inet {
address 10.1.1.0/31;
}
family mpls;
}
}
lo0 {
unit 0 {
family Continue reading
Some Things I Learned About VeloCloud SD-WAN
Some things about VeloCloud I learned at #NFD17
Intel Offloads Wind River to Investment Firm TPG
 The deal ends Intel’s near decade of ownership of Wind River. The embedded software firm will keep its existing management team when it's independent.
The deal ends Intel’s near decade of ownership of Wind River. The embedded software firm will keep its existing management team when it's independent.
CEO Succession at Internet Society – Friday Deadline for Open Call for Candidates
As I informed our community in my last note, we launched the Open Call for CEO Candidates on Friday, 9 March 2018.
The deadline for applications is 23:59 UTC on Friday, 6 April 2018
This means that potential candidates interested in applying still have a few more days to do so. Candidates can apply for the position by visiting the Perrett Laver (our search firm for this process) web site using the following link:
https://candidates.perrettlaver.com/vacancies/726/ceo/
While the Candidate Pack (information about the CEO position) has been available for download on the link above during the whole open call, we have received input from our community asking us to make the Candidate Pack available also on a regular URL outside the search firm’s portal. Accordingly, for your convenience, we have now made it available on the following link as well:
https://www.internetsociety.org/wp-content/uploads/2018/04/Internet-Society-CEO-Succession.pdf
Please, distribute this call to potential candidates who may be interested so that they can apply before the upcoming deadline.
The ongoing open call for candidates will result in a long list of candidates. Taking the long list as a starting point, the whole board (at this point the search committee has already done Continue reading
Istio Keeps Digging Toward 1.0 GA Release
 The platform is increasingly popping up in conversations tied to the orchestration and management of containers in a production environment.
The platform is increasingly popping up in conversations tied to the orchestration and management of containers in a production environment.
Data Center Report Finds Cost Is Not the Big Driver for New Technology
 A big driver for using next-generation technologies was improved capabilities to configure, troubleshoot, and measure data center networks.
A big driver for using next-generation technologies was improved capabilities to configure, troubleshoot, and measure data center networks.
Mosaic NetworX Shortens Its SD-WAN Sales Process With Connected2Fiber
 Mosaic NetworX integrated Connected2Fiber’s connected world platform with its Salesforce instance to more effectively design and sell its SD-WAN service.
Mosaic NetworX integrated Connected2Fiber’s connected world platform with its Salesforce instance to more effectively design and sell its SD-WAN service.
Juniper Networks’ Security Strategy: Unify Everything, Keep it Open
 Juniper Networks security team wants to unify threat detection, automated enforcement, and mitigation in a unified platform and integrate with other technology vendors to support non-Juniper gear.
Juniper Networks security team wants to unify threat detection, automated enforcement, and mitigation in a unified platform and integrate with other technology vendors to support non-Juniper gear.
Extend your security view from the data center to the edge
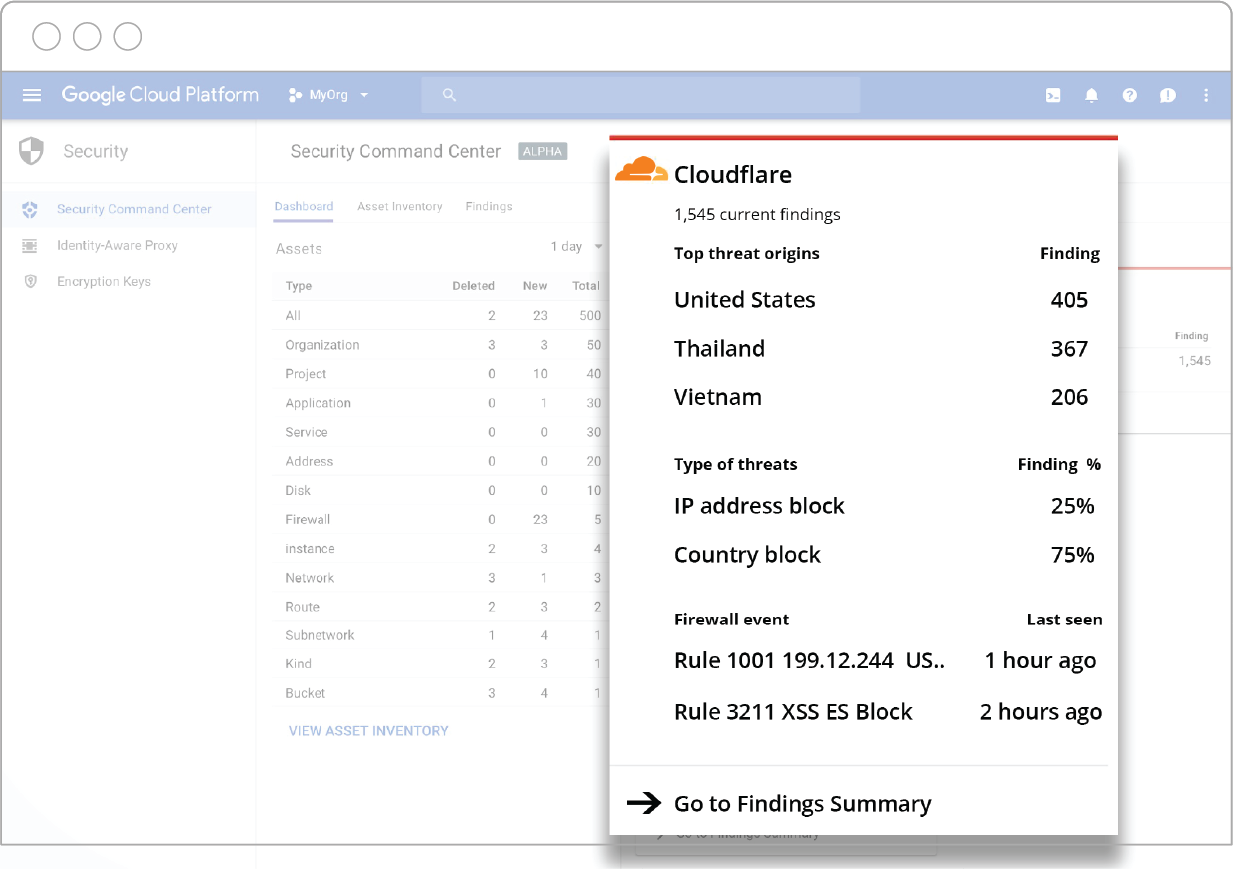
How great would it be to have a dashboard with a holistic view of threats, malicious server activity, vulnerabilities, sensitive data access levels and a daily scan of resources across all of your applications and services? Now you can.
Cloudflare is thrilled to announce its integration with Cloud Security Command Center (Cloud SCC) for Google Cloud Platform: A security and data risk platform helping enterprises gather data, identify threats, and act on them before they result in business damage or loss.
The advantage of the Cloud SCC solution is that it surfaces insights from both the Google Cloud Platform, as well as Cloudflare’s edge, in a unified dashboard.
What Cloudflare data is visible within the Cloud SCC dashboard?
Through Cloudflare’s API endpoints, data is pushed to Google’s Cloud SCC dashboard and domain name information mapped to the appropriate Google Cloud asset. Cloudflare’s branded card in the Cloud SCC dashboard is automatically populated with a summary of top theat origins, top types of threats, and latest Web Application Firewall (WAF) events.
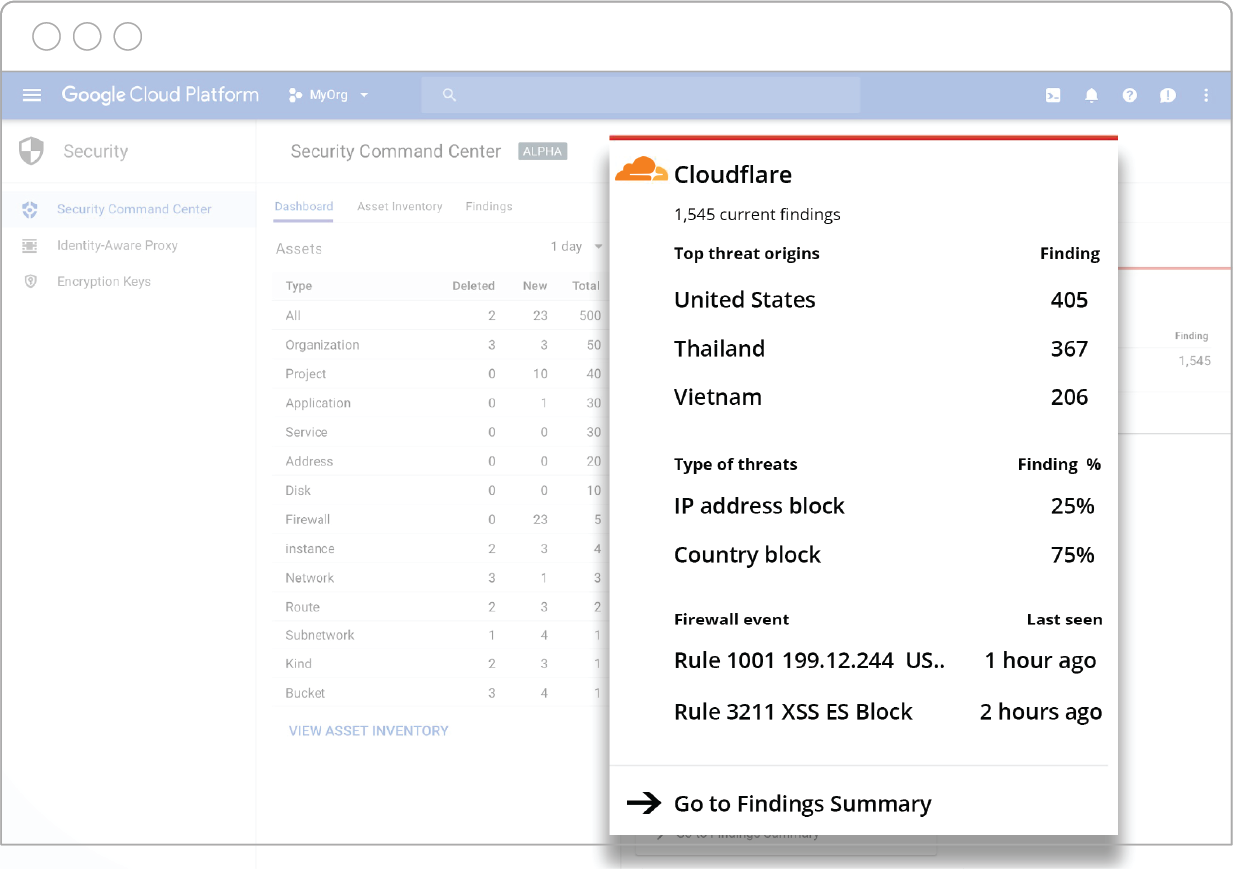
To view a full list of Cloudflare events, click on the Cloudflare card in Cloud SCC and it will take you to a “Cloudflare Findings” page. From there, you can Continue reading
Red Hat Rides Containers, Kubernetes, Hybrid Cloud Into the Future
 OpenShift, OpenStack, and Ansible were key drivers for 2018 results, with the impending acquisition of CoreOS set to bolster its container and Kubernetes position moving forward.
OpenShift, OpenStack, and Ansible were key drivers for 2018 results, with the impending acquisition of CoreOS set to bolster its container and Kubernetes position moving forward.
