Show 379: Grappling With Promise Theory
Mark Burgess, who developed the principles of Promise Theory as a way to model distributed systems, joins the Packet Pushers to explore how his ideas connect to networking and information systems. The post Show 379: Grappling With Promise Theory appeared first on Packet Pushers.Riverbed Gains Revenue Share in SD-WAN
 Cisco and VMware change the SD-WAN playing field.
Cisco and VMware change the SD-WAN playing field.
Nutanix Reports Strong Revenue, Buys Minjar, Plans Hyperconverged Cloud Domination
 Minjar sells a service that compares costs across public clouds.
Minjar sells a service that compares costs across public clouds.
NSX Layer 2 VPN: Deploying for datacentre migrations
In my previous post, NSX Layer 2 VPN: Migrating workloads between Datacentres, I described the process and theory behind using an NSX Layer 2 VPN (L2VPN) to migrate workloads from a soon-to-be-retired VLAN backed datacentre, to an NSX Managed logical switch backed datacentre. In this post I will take you through the deployment of the L2VPN in my lab environment, following these high-level steps:
- Prepare the NSX Managed Site
- Deploy the Layer 2 VPN Server
- Prepare the Standalone Site
- Deploy the Layer 2 VPN Client
- Validate the Layer 2 VPN connectivity
Current lab environment
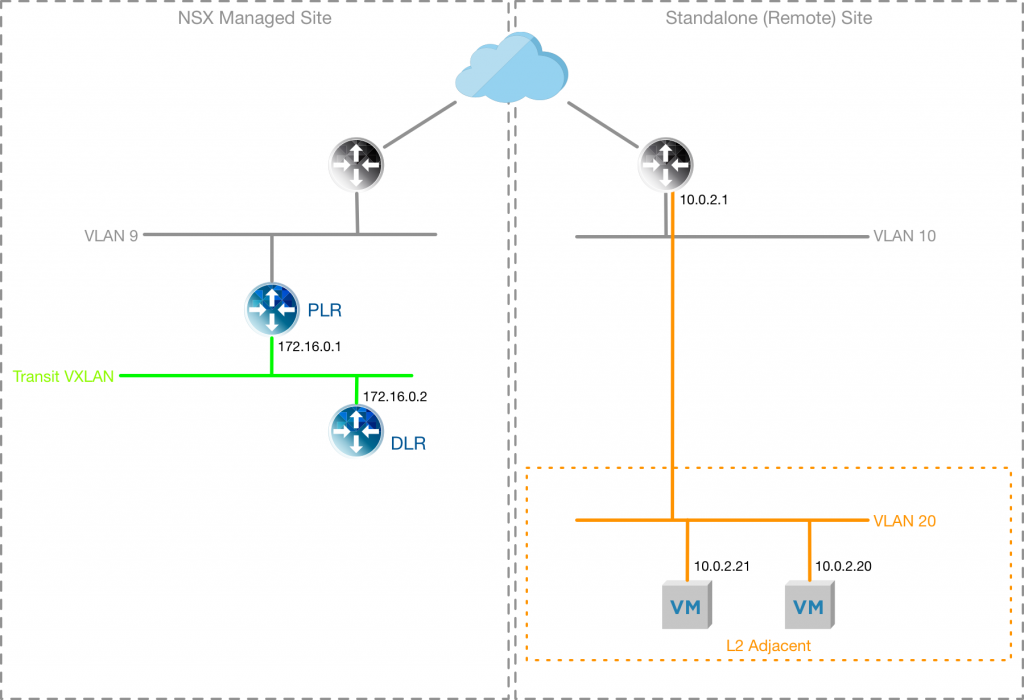
The Lab environment I am using currently reflects the diagram below, with two VMs deployed onto VLAN 20 within my “remote” site (my remote site is actually just a separate cluster from my “NSX Managed Site”, which is my workload cluster). In my NSX Managed site I have a Provider Logical Router (PLR) and Distributed Logical Router (DLR) configured.
Configure the NSX Managed Site
To prepare the NSX Managed Site the L2VPN-Server needs to be connected to a “trunk” interface, which allows multiple VLAN or Logical Switches to be configured as sub-interfaces, rather than having an interface in each VLAN/Logical Switch.
The Continue reading
When Will BGP Become Unfashionable? – Video
If we're ever going to find a replacement for BGP, we'll need to build a community that draws interest and attention. Where will the next fashion come from?Is NAT a Bad Thing?
Peter Welcher examines the pros and cons of Network Address Translation and describes design scenarios.
Vodafone Finds Containers Drastically More Efficient Than VMs
 Resource savings with containers is pegged at around 40 percent.
Resource savings with containers is pegged at around 40 percent.
Engineering versus Metaengineering
In my latest short take over at the Network Collective, I explain the difference between engineering and metaengineering.
The Modern Telco is Open Series, Part 1: Open Telco Framework Q&A
 Thanks to all who joined us for the first of The Modern Telco is Open Series, The Open Telco Framework. During the webinar, we saw how Red Hat’s open 5G architecture foundation helps modern telcos deploy new services (MEC apps, vRAN, IoT) – faster, economically and at massive scale. After the webinar, we had a live Q&A with... Read more →
Thanks to all who joined us for the first of The Modern Telco is Open Series, The Open Telco Framework. During the webinar, we saw how Red Hat’s open 5G architecture foundation helps modern telcos deploy new services (MEC apps, vRAN, IoT) – faster, economically and at massive scale. After the webinar, we had a live Q&A with... Read more →
SDxCentral’s Weekly Roundup — March 2, 2018
 Cisco forms IoT, 5G, and smart city partnerships; Softbank and Affirmed Networks strike an IoT agreement; VMware launches edge technology.
Cisco forms IoT, 5G, and smart city partnerships; Softbank and Affirmed Networks strike an IoT agreement; VMware launches edge technology.
Enterprise Network on GNS3 – Part 7 – DMZ
This is the last article from the series of the articles discussing configuration of the enterprise network. The article explains the configuration of Demilitarized Zone (DMZ). Our DMZ consists of three devices - ASAv-DMZ-I, a multilayer switch vIOS-DMZ-I and Serv-DMZ-I. All the devices in DMZ are run by Qemu hypervisor. The ASAv_DMZ-I device is Cisco Adaptive Security Appliance Software version 9.6.1 and it has assigned 2048 MB RAM by GNS3. The device vIOS-DMZ-I is Cisco vIOS-L2 version 15.2 and it has assigned 512 MB RAM by GNS3. And finally, the device Serv-DMZ-I is Linux Ubuntu 16.04.3 LTS with 1024 MB RAM assigned by GNS3. The server Serv-DMZ-I provides DNS, NTP, Syslog services for devices in DMZ and a public web service for all hosts in the Internet.
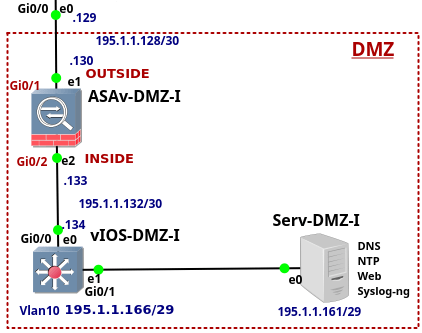
Picture 1 - Demilitarized Zone - DMZ
All devices located in DMZ have their IP addresses assigned from the subnet 195.1.1.128/25. The subnet 195.1.1.128/27 is further divided with /30 mask, creating 8 subnets suitable for point-to-point link configuration . Servers located in DMZ are assigned to different VLANs. Currently, there is only server Serv-DMZ-I deployed in DMZ and configured with the IP addresses Continue reading
Enterprise Network on GNS3 – Part 7 – DMZ
This is the last article from the series of the articles discussing configuration of the enterprise network. The article explains the configuration of Demilitarized Zone (DMZ). Our DMZ consists of three devices - ASAv-DMZ-I, a multilayer switch vIOS-DMZ-I and Serv-DMZ-I. All the devices in DMZ are run by Qemu hypervisor. The ASAv_DMZ-I device is Cisco Adaptive Security Appliance Software version 9.6.1 and it has assigned 2048 MB RAM by GNS3. The device vIOS-DMZ-I is Cisco vIOS-L2 version 15.2 and it has assigned 512 MB RAM by GNS3. And finally, the device Serv-DMZ-I is Linux Ubuntu 16.04.3 LTS with 1024 MB RAM assigned by GNS3. The server Serv-DMZ-I provides DNS, NTP, Syslog services for devices in DMZ and a public web service for all hosts in the Internet.

Picture 1 - Demilitarized Zone - DMZ
All devices located in DMZ have their IP addresses assigned from the subnet 195.1.1.128/25. The subnet 195.1.1.128/27 is further divided with /30 mask, creating 8 subnets suitable for point-to-point link configuration . Servers located in DMZ are assigned to different VLANs. Currently, there is only server Serv-DMZ-I deployed in DMZ and configured with the IP addresses Continue reading
Short Take – Metaengineering
What’s the difference between being an engineer or a metaengineer? In this Network Collective Short Take, Russ White differentiates between the two and explores when it makes sense to be one or the other.
The post Short Take – Metaengineering appeared first on Network Collective.
Memcached DDoS – There’s Still Time to Save Your Mind

In case you haven’t heard, there’s a new vector for Distributed Denial of Service (DDoS) attacks out there right now and it’s pretty massive. The first mention I saw this week was from Cloudflare, where they details that they were seeing a huge influx of traffic from UDP port 11211. That’s the port used by memcached, a database caching system.
Surprisingly, or not, there were thousands of companies that had left UDP/11211 open to the entire Internet. And, by design, memcached responds to anyone that queries that port. Also, carefully crafted packets can be amplified to have massive responses. In Cloudflare’s testing they were able to send a 15 byte packet and get a 134KB response. Given that this protocol is UDP and capable of responding to forged packets in such a way as to make life miserable for Cloudflare and, now, Github, which got blasted with the largest DDoS attack on record.
How can you fix this problem in your network? There are many steps you can take, whether you are a system admin or a network admin:
- Go to Shodan and see if you’re affected. Just plug in your company’s IP address ranges and have it Continue reading
IT Automation: Not Just for the Big Dogs
Hyperscale companies like AWS have led the way on automation, but enterprise IT can close the gap by following these steps.