Google Pays $50M for IoT Firm Xively
 The deal will give Google more IoT firepower.
The deal will give Google more IoT firepower.
Network Engineer Certification in 2018
Last week I was in Mountain View, in a room full of senior Network Engineers, and we were talking about the skills that need to be developed by more junior Network Engineers. Suddenly someone shouted from the back "CCIE!" and the whole room started laughing.
So CCIE is a laughing stock now?
No need to get offended. You have to understand the context here:
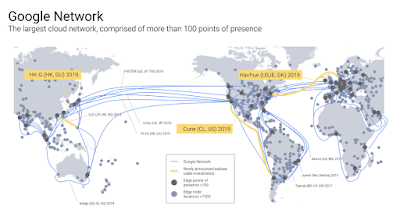
These group of people have been working for the best company in the world. They have been working on the most advanced network infrastructure. The company's undersea cables connect all contingents, to delivers 25% of worldwide Internet traffic.
These people didn't develop their skill through certification. They developed their skills by building the real stuff. When these group of Network Engineers realized the network capacity in the company's data centers has grown so fast that conventional routers and switches can't keep up to meet the requirements of its distributed systems, they decided to build its own instead. These Network Engineers build and operate software-defined networking, before the world invented that terminology. They've been automating network operation in Data Center, WAN, Internet Peering, all the way to Wifi and Enterprise networking, to support 7 company's Continue reading
Show 377: SD-WAN Use Cases With Silver Peak (Sponsored)
We explore real-world SD-WAN use cases, including service chaining and SaaS performance improvement, with sponsor Silver Peak in our latest Weekly Show podcast. The post Show 377: SD-WAN Use Cases With Silver Peak (Sponsored) appeared first on Packet Pushers.Celebrating the 25th Anniversary of NDSS
 This year we are celebrating the 25th anniversary of the Network and Distributed System Security Symposium (NDSS). NDSS is a premier academic research conference addressing a wide range of topics associated with improving trust in the Internet and its connected devices. A key focus of the Internet Society has long been improving trust in the global open Internet. In order to promote this trust, we need new and innovative ideas and research on the security and privacy of our connected devices and the Internet that connects them together.
This year we are celebrating the 25th anniversary of the Network and Distributed System Security Symposium (NDSS). NDSS is a premier academic research conference addressing a wide range of topics associated with improving trust in the Internet and its connected devices. A key focus of the Internet Society has long been improving trust in the global open Internet. In order to promote this trust, we need new and innovative ideas and research on the security and privacy of our connected devices and the Internet that connects them together.
NDSS 2018 is about to get underway in San Diego, CA (18-21 February). It will be the biggest NDSS symposium yet, featuring 71 peer-reviewed papers, 20 posters, 4 workshops, 2 keynotes, and a co-located research group meeting. Record registration numbers are a key indicator that NDSS 2018 is featuring vital and timely topics. Below are some of the highlights expected in the coming week.
Workshops
This year’s program officially starts with four workshops on Sunday, 18 February. NDSS workshops are organized around a single topic and provide an opportunity for greater dialogue amongst researchers and practitioners in the area. Each of this year’s workshop have dynamic agendas.
SDxCentral’s Weekly Roundup — February 15, 2018
 Qualcomm board meets Broadcom; Google releases Beta test of its Cloud TPUs; Tech Mahindra and VMware partner.
Qualcomm board meets Broadcom; Google releases Beta test of its Cloud TPUs; Tech Mahindra and VMware partner.
Making Alexa Tech Demos Useful

Technology always marches on. People want to see the latest gadgets doing amazing things, whether it be flying electric cars or telepathic eyeglasses. Our society is obsessed with the Jetsons and the look of the future. That’s why we’re developing so many devices to help us get there. But it’s time for IT to reconsider how they are using one of them for a purpose far from the original idea.
Speaking For The People
By all accounts, the Amazon Echo is a masterful device. It’s a smart speaker that connects to an Amazon service that offers you a wider variety of software programs, called skills, to enhance what you can do with it. I have several of these devices that were either given out as conference attendance gifts or obtained from other giveaways.
I find the Echo speaker a fascinating thing. It’s a good speaker. It can play music through my phone or other Bluetooth-connected devices. But, I don’t really use it for that purpose. Instead, I use the skills to do all kinds of other things. I play Jeopardy! frequently. I listen to news briefings and NPR on a regular basis. I get weather forecasts. My son uses Continue reading
Cisco Gives Cloud-Based Endpoint Security Products an MSSP Makeover
 Cisco will “actively pursue” MSSP customers across its entire portfolio, SVP says.
Cisco will “actively pursue” MSSP customers across its entire portfolio, SVP says.
Short Take – Broadcom SDKLT
In this Short Take from Network Collective, Russ White shares his thoughts on the recently released Broadcom SDKLT and the impact it will have on the networking industry.
The post Short Take – Broadcom SDKLT appeared first on Network Collective.
Why IT Dashboards Fail
Most dashboards today don't tell the story behind the data.
[Video] Configure Data Center Devices with PowerShell
PowerShell started as a tool to automate Windows servers. It was picked up by VMware (and others) as a platform on which they built their own solutions (PowerCLI and PowerNSX)… but did you know you can use it to configure data center infrastructure, including NX-OS switches, SAN networks, and Cisco UCS?
In the Configuring Data Center Devices with PowerShell video, Mitja Robas described how to do that, and provided source code for all his examples.
You’ll need at least free ipSpace.net subscription to watch the video.
Musical Chairs Playing Tetris
Introduction ASERT has discovered new command-and-control infrastructure controlled by the APT actors behind the Musical Chairs campaign. The security research community has associated these actors with significant campaigns in the past, including the pivotal Night Dragon campaign reported on by McAfee in 2011. The actors […]Musical Chairs Playing Tetris
February 20, 2018: This blog has been amended since it was originally published on February 15, 2018. This version removes the association with the APT group responsible for the Night Dragon campaign that we had incorrectly made. We thank the research team at Palo Alto […]BiB 035: ReSTNSX Makes NSX Easier To Operate
Ethan Banks had a briefing with ReSTNSX, and they demoed their VMware NSX-enhancing platform to him. Have a listen for Ethan's impressions of the demo.
The post BiB 035: ReSTNSX Makes NSX Easier To Operate appeared first on Packet Pushers.