Check Out Our Newest Course: CCNA Cyber Ops Technology: SECFND 210-250
Last week we added a new CCNA Cyber Ops Course. This course is available to AAP members through your members and to everyone else through ine.com
Why You Should Watch:
Cisco’s CCNA Cyber Ops certification provides individuals with the knowledge to identify and respond to security incidents. This certification provides a path to working in a Security Operations Center (SOC) and security positions. As a CCNA level certification, Cyber Ops provides introductory knowledge so one may be aware of the security landscape, understand security concepts and general networking.
About the Course:
This course will cover the exam topics of the Understanding Cisco Cybersecurity Fundamentals (SECFND 210-250) Exam.This course is taught by Andrew Crouthamel and is 7 hours and 32 minutes long.
What You’ll Learn:
We will dive into topics such as networking concepts and IP addressing, as well as security concepts including access control models, risk assessment and the CIA triad. We will also review cryptography methods and host-based analysis details, as well as security monitoring tools and attack methods used by threat actors.
About the Author:
Andrew is a seasoned IT engineer with over 12 years of experience. He started out in IT as an assistant Continue reading
AT&T to Release “dNOS” Software Framework Into Open Source to Accelerate Network White Box Adoption
 dNOS goes to Linux Foundation to be Open (instead of half closed)
dNOS goes to Linux Foundation to be Open (instead of half closed)OpenCT’s Blockchain Platform Aims to Transform Telcos
 A new white paper from OpenCT features detailed technical examples of OpenCT’s two telco solutions: Blockchain as a Transport (BaaT) and Blockchain-Defined Wide Area Networks (BD-WAN).
A new white paper from OpenCT features detailed technical examples of OpenCT’s two telco solutions: Blockchain as a Transport (BaaT) and Blockchain-Defined Wide Area Networks (BD-WAN).
Context-Aware Micro-segmentation – an innovative approach to Application and User Identity Firewall
Summary: With Context-awareness, NSX for vSphere 6.4 enables customers to enforce policy based on Application and Protocol Identification and expands the Identity Firewall support to Multiple User Sessions.
A few weeks ago, VMware released version 6.4 of NSX for vSphere. The 6.4 release brings many new features, with Context-awareness being key from a security perspective. Micro-segmentation enables East-West security controls, and is a key building block to a secure datacenter. Context-awareness builds-on and expands Micro-segmentation by enabling customers even more fine-grained visibility and control. NSX has supported the use infrastructure or application-centric constructs such as Security Groups based on criteria like VM name or OS version, or Dynamic Security Tags describing things like the workload function, the environment it’s deployed in, or any compliance requirements the workload falls under, enabling fine-grained control and allowing customers to automate the lifecycle of a security policy from the time an application is provisioned to the time it’s decommissioned. Prior to 6.4, rules with infrastructure or application-centric grouping constructs on the Management plane, are eventually translated to 5-tuple based rules in the dataplane.
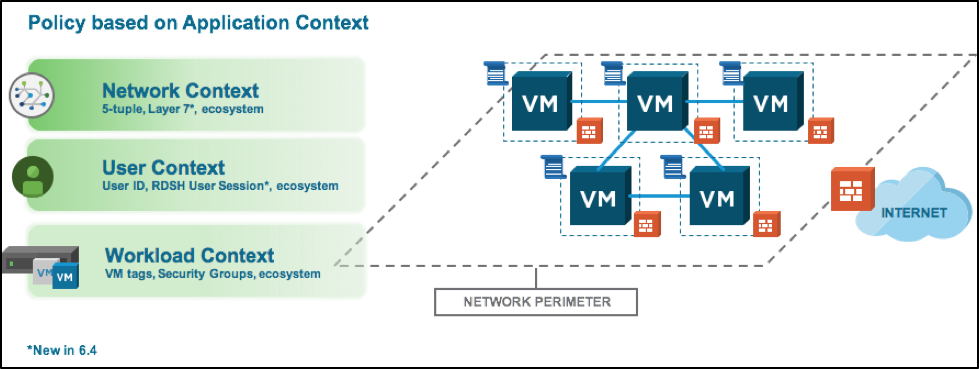 Figure: NSX drives policy based on Network, User and Workload Context
Figure: NSX drives policy based on Network, User and Workload Context
A crucial aspect of Context-awareness Continue reading
Fortinet Stock Pops on Robust 2017 Q4 Results, Modest Forecasts
 The company will also welcome a new CFO.
The company will also welcome a new CFO.
Episode 21 – Tools For Network Engineers
In this episode of Network Collective, Hank Yeomans and Jonathan Davis join us to take a look at some of our favorite tools as network engineers. Whether it’s hardware or software, tools are the things that help us do our jobs well, and if used correctly, can help set you apart.
 We would like to thank Cumulus Networks for sponsoring this episode of Network Collective. Cumulus invites you to find out more about how Linux is changing the data center networking space by downloading their free ebook “Linux Networking 101” here: http://cumulusnetworks.com/NetworkCollectiveLinux
We would like to thank Cumulus Networks for sponsoring this episode of Network Collective. Cumulus invites you to find out more about how Linux is changing the data center networking space by downloading their free ebook “Linux Networking 101” here: http://cumulusnetworks.com/NetworkCollectiveLinux
Show Notes:
- Text Editer
- It sounds simple, but a good text editor saves a lot of time
- Regex search and replace is incredibly powerful once you know how to use it well
- Standard features as well, like tabbed interfaces
- Good options – Sublime Text, Notepad++
- Terminal Software
- Options
- Secure CRT
- Term colorization
- Hank’s colorization file: https://thenetworkcollective.com/wp-content/uploads/2018/02/CiscoWords.zip
- Saved session management
- Secure credential management w/ auto login
- Dynamic logging
- Term colorization
- iTerm2
- Similar feature set as Secure CRT
- Replacement shell on mac
- Putty
- Very good go-to on jump boxes and other systems
- Session managers make putty better for long term use
- Secure CRT
- Good monowidth fonts make Continue reading
- Options
The Network Architect Part 2
I got some great comments from my readers on the first part of this post. I love engaging with readers! So I thought I would write a part two to explain some of my thinking which I described in some of the comments.
Does a network architect need to be technical?
Yes, he/she needs to be technical but what does that mean? Let’s say that two datacenters need to be connected. Layer two needs to be stretched between the two DCs. The architect should be able to know different solutions to the problem such as using fibres between the two DCs, clustering technologies, TRILL, OTV and so on. Does the architect need to be able to configure OTV off the bat? Nope. Does the architect need to know what different timers OTV uses? Nope. Those are not things that need to be considered at that point in time. Now, often the architect is involved in the actual design as well and in that case the architect is involved in creating the design and documenting what commands are needed and so on. So the architect needs to be technical but not super technical.
Does the network architect need operational experience?
Preferably Continue reading
Help Five Projects Connect the World
At Bilkent University in Ankara, students sit at desks littered with bookbags and bottles of water. It looks like a typical classroom, except for the makeup of the students – school-age girls – and when the instructor asks a question, the room comes alive. “Who wants to code again after today?”
The hands shoot up.
The students are participating in Coding Sisters, a program that teaches coding to girls. Soon they are grinning as they raise their certificates of completion into the air. They yell in unison, “Hello world!”
The project was funded by the Internet Society’s “Digital schools!” Chapterthon 2017, in partnership with Wikimedia Foundation. From October to November 2017, 30 projects from around the world came together to bring educational opportunities to children, especially girls. Chapterthon has been nominated for a series of prizes to be given out at the World Summit on the Information Society (WSIS), an annual United Nations-sponsored summit focused on the role information and communication plays in our world. TheWSIS Prizes recognize individuals and organizations that advance the Sustainable Development Goals: 17 global goals dedicated to building a better world by 2030.
Four other innovative, Internet Society-funded projects Continue reading
Explain Cisco ETA to Me in a Way That Even My Neighbor Can Understand It
Cisco Encrypted Traffic Analytics (ETA) sounds just a little bit like magic the first time you hear about it. Cisco is basically proposing that when you turn on ETA, your network can (magically!) detect malicious traffic (ie, malware, trojans, ransomware, etc) inside encrypted flows. Further, Cisco proposes that ETA can differentiate legitimate encrypted traffic from malicious encrypted traffic.
Uhmm, how?
The immediate mental model that springs to mind is that of a web proxy that intercepts HTTP traffic. In order to intercept TLS-encrypted HTTPS traffic, there’s a complicated dance that has to happen around building a Certificate Authority, distributing the CA’s public certificate to every device that will connect through the proxy and then actually configuring the endpoints and/or network to push the HTTPS traffic to the proxy. This is often referred to as “man-in-the-middle” (MiTM) because the proxy actually breaks into the encrypted session between the client and the server. In the end, the proxy has access to the clear-text communication.
Is ETA using a similar method and breaking into the encrypted session?
In this article, I’m going to use an analogy to describe how ETA does what it does. Afterwards, you should feel more comfortable about how Continue reading
Meltdown, Spectre Create Data Center Dilemma
CPU flaws raise capacity and cost concerns for data center operators.
Automation Win: Cleanup Checkpoint Configuration
Gabriel Sulbaran decided to tackle a pretty challenging problem after watching my Ansible for Networking Engineers webinar: configuring older Checkpoint firewalls.
I had no idea what Ansible was when I started your webinar, and now I already did a really simple but helpful playbook to automate changing the timezone and adding and deleting admin users in a Checkpoint firewall using the command and raw modules. Had to use those modules because there are no official Checkpoint module for the version I'm working on (R77.30).
Did you automate something in your network? Let me know!
Explain Cisco ETA to Me in a Way That Even My Neighbor Can Understand It
Cisco Encrypted Traffic Analytics (ETA) sounds just a little bit like magic the first time you hear about it. Cisco is basically proposing that when you turn on ETA, your network can (magically!) detect malicious traffic (ie, malware, trojans, ransomware, etc) inside encrypted flows. Further, Cisco proposes that ETA can differentiate legitimate encrypted traffic from malicious encrypted traffic.
Uhmm, how?
The immediate mental model that springs to mind is that of a web proxy that intercepts HTTP traffic. In order to intercept TLS-encrypted HTTPS traffic, there's a complicated dance that has to happen around building a Certificate Authority, distributing the CA's public certificate to every device that will connect through the proxy and then actually configuring the endpoints and/or network to push the HTTPS traffic to the proxy. This is often referred to as “man-in-the-middle” (MiTM) because the proxy actually breaks into the encrypted session between the client and the server. In the end, the proxy has access to the clear-text communication.
Is ETA using a similar method and breaking into the encrypted session?
In this article, I'm going to use an analogy to describe how ETA does what it does. Afterwards, you should feel more comfortable about how Continue reading
It’s Hard To Change The Keys To The Internet And It Involves Destroying HSM’s


The root of the DNS tree has been using DNSSEC to protect the zone content since 2010. DNSSEC is simply a mechanism to provide cryptographic signatures alongside DNS records that can be validated, i.e. prove the answer is correct and has not been tampered with. To learn more about why DNSSEC is important, you can read our earlier blog post.
Today, the root zone is signed with a 2048 bit RSA “Trust Anchor” key. This key is used to sign further keys and is used to establish the Chain of trust that exists in the public DNS at the moment.
With access to this root Trust Anchor, it would be possible to re-sign the DNS tree and tamper with the content of DNS records on any domain, implementing a man-in-the-middle DNS attack… without causing recursors and resolvers to consider the data invalid.
As explained in this blog the key is very well protected with eye scanners and fingerprint readers and fire-breathing dragons patrolling the gate (okay, maybe not dragons). Operationally though, the root zone uses two different keys, the mentioned Trust Anchor key (that is called the Key Signing Key or KSK for Continue reading
Palo Alto Networks Stretches Security Posture Across Big 3 Public Clouds
 The new features and additional cloud support aim to provide stronger security and simplified management.
The new features and additional cloud support aim to provide stronger security and simplified management.
The Network Architect
What’s the difference between a network architect and a network designer? What is network architecture and what is network design? These are questions I asked myself a couple of years ago and that I get asked frequently from others. The reason I wanted to write this post is to help people that want to be network architects understand what it is about. I also wanted to help people that are studying for the CCDE to get into the right mindset. If you go in to the practical with the mindset of a designer, you will fail. You need to think like an architect.
This post is not about if an architect is more advanced than a designer. They are both needed and often they are the same person. I work as both but my title is network architect. Some people use the title to indicate it’s a senior role although the role might not be heavily geared towards design.
So what does a network architect do? And how is that different from the network designer?
The network architect is the one that is fronting the business. What does this mean? The network architect is the one that is meeting stakeholders Continue reading