Precedence of Ansible Extra Variables
I stay as far away from Ansible as possible these days and use it only as a workflow engine to generate device configurations from Jinja2 templates and push them to lab devices. Still, I manage to trigger unexpected behavior even in these simple scenarios.
Ansible has a complex system of variable (fact) precedence, which mostly makes sense considering the dozen places where a variable value might be specified (or overwritten). Ansible documentation also clearly states that the extra variables (specified on the command line with the -e keyword) have the highest precedence.
Now consider these simple playbooks. In the first one, we’ll set a fact (variable) and then print it out:
Precedence of Ansible Extra Variables
I stay as far away from Ansible as possible these days and use it only as a workflow engine to generate device configurations from Jinja2 templates and push them to lab devices. Still, I manage to trigger unexpected behavior even in these simple scenarios.
Ansible has a complex system of variable (fact) precedence, which mostly makes sense considering the dozen places where a variable value might be specified (or overwritten). Ansible documentation also clearly states that the extra variables (specified on the command line with the -e keyword) have the highest precedence.
Now consider these simple playbooks. In the first one, we’ll set a fact (variable) and then print it out:
NX-OS Forwarding Constructs For VXLAN/EVPN
In this post we will look at the forwarding constructs in NX-OS in the context of VXLAN and EVPN. Having knowledge of the forwarding constructs helps both with understanding of the protocols, but also to assist in troubleshooting. BRKDCN-3040 from Cisco Live has a nice overview of the components involved:
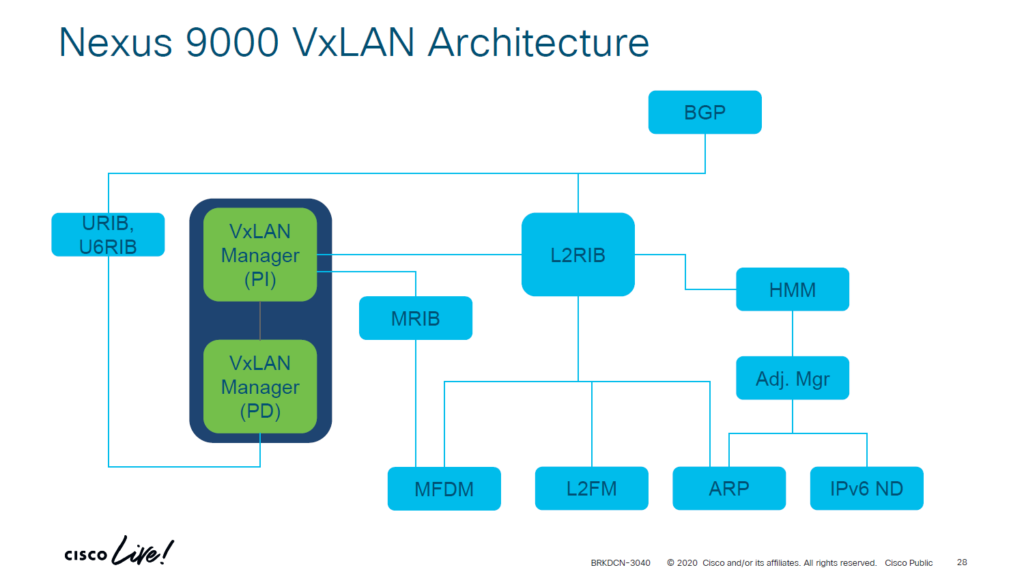
There are components that are platform independent (PI) and platform dependent (PD). Below I’ll explain what each component does:
- ARP – Information from ARP requests/responses is needed to build adjacencies. The information learned from ARP is used to populate IP address field in RT2 and hence also to populate the ARP suppression cache.
- IPv6 ND – ND fills the role of ARP, but for IPv6.
- Adjacency Manager – Resolves directly attached hosts MAC addresses.
- Host Mobility Manager – Tracks the endpoints and their movements.
- L2FM – The Layer2 Forwarding Manager. A platform dependent component that programs ASICs for L2 forwarding. Keeps track of MAC addresses, their placement and moves, and synchronizes this information across ASICS, line cards, and vPC peers when vPC is in use.
- MFDM – Multicast Forwarding Database Manager. A platform dependent component that programs ASICs with information to perform multicast forwarding.
- L2RIB – The component that handles Continue reading
NetFlow data and its fields vs packet capture
The post NetFlow data and its fields vs packet capture appeared first on Noction.
Hull and cabin
When it comes to working with steel it is a bit outside my comfort zone so I got the professionals in to do the blacking of the hull and a few different things to the cabin shell.
ICANN Launches 10-Year, $200 Million Program to Expand and Protect Internet Ecosystem
The grant program will support the next phase of global Internet growth and will emphasize digital inclusivity.BGP Labs: Override Neighbor AS Number in AS Path
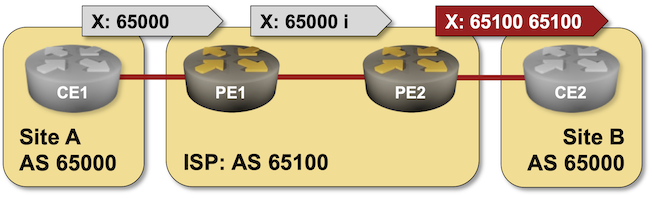
When I described the need to turn off the BGP AS-path loop prevention logic in scenarios where a Service Provider expects a customer to reuse the same AS number across multiple sites, someone quipped, “but that should be fixed by the Service Provider, not offloaded to the customer.”
Not surprisingly, there’s a nerd knob for that (AS override), and you can practice it in the next BGP lab exercise: Fix AS-Path in Environments Reusing BGP AS Numbers.
BGP Labs: Override Neighbor AS Number in AS Path
When I described the need to turn off the BGP AS-path loop prevention logic in scenarios where a Service Provider expects a customer to reuse the same AS number across multiple sites, someone quipped, “but that should be fixed by the Service Provider, not offloaded to the customer.”
Not surprisingly, there’s a nerd knob for that (AS override), and you can practice it in the next BGP lab exercise: Fix AS-Path in Environments Reusing BGP AS Numbers.

Understanding SASE Architecture
SASE converges the functions of network and security point solutions into a unified, global, cloud-native service. Such capabilities provide enterprises with a number of benefits.Tech Bytes: Building An Automation-Ready Service Catalog With NetOrca (Sponsored)
Let’s say you’ve built a set of automations for your network infrastructure, and now you want teams or departments within your organization to use those automations. Our Tech Bytes sponsor NetOrca offers a service catalog that provides a simple front-end to make it easy for internal customers to come and consume those capabilities you’ve worked... Read more »NB464: Juniper Begins AI Push Into The Data Center; VMware Customers Confront Higher Prices
This week we discuss new products from Juniper including synthetic testing software for its Mist wireless networks and its first step toward integrating its Apstra data center software with AI. VMware clarifies its product strategy as customers face rising prices, and undersea cables in the Red Sea face potential threats. Nokia and Chinese mobile device... Read more »Understanding Why Contact Center Agent Empowerment is Critical to a Great Customer Experience
Contact center leaders from 8x8, Awaken Intelligence, and 360insight discuss the importance of agent experience.AI Drives the Ethernet and InfiniBand Switch Market
AI may force enterprises to rewire parts of their data centers so they are fully optimized to run such workloads. The question is do you use Ethernet or InfiniBand?VPP Python API
About this series
Ever since I first saw VPP - the Vector Packet Processor - I have been deeply impressed with its performance and versatility. For those of us who have used Cisco IOS/XR devices, like the classic ASR (aggregation service router), VPP will look and feel quite familiar as many of the approaches are shared between the two.
You’ll hear me talk about VPP being API centric, with no configuration persistence, and that’s by
design. However, there is this also a CLI utility called vppctl, right, so what gives? In truth,
the CLI is used a lot by folks to configure their dataplane, but it really was always meant to be
a debug utility. There’s a whole wealth of programmability that is not exposed via the CLI at all,
and the VPP community develops and maintains an elaborate set of tools to allow external programs
to (re)configure the dataplane. One such tool is my own [vppcfg] which takes a YAML specification that describes the dataplane configuration, and applies it
safely to a running VPP instance.
Introduction
In case you’re interested in writing your own automation, this article is for you! I’ll provide a deep dive into Continue reading
HN718: Prisma SASE Gets Clever With TCP For Better App And User Experiences (Sponsored)
Remote and hybrid work means network engineers have to grapple with lossy residential networks such as home wireless that your work-from-home folks are using to access company resources. Their Wi-Fi sucks, and so their use of corporate resources sucks. Sure, you’ve got them plumbed into a SASE fabric, but that doesn’t fix their user experience... Read more »Hedge 210: Eric Chou and Technical Publishing
Have you ever thought about publishing a book or recording a professional video? It’s not as simple as proposing an idea, doing the work, and becoming famous (or infamous, as the case might be). Eric Chou joins Rick Graziani and Russ to talk about the ins and outs of technical publishing. We are planning a part 2 of this in a few months to cover things we left on the table for later discussion.
Public Videos: Kubernetes Container Network Interface (CNI)

All the Container Network Interface videos from the Kubernetes Networking Deep Dive webinar with Stuart Charlton are now public. Enjoy!
Cyber attacks targeting Jewish and Holocaust educational websites surge by 872% in 2023

Tomorrow is the International Holocaust Remembrance Day, a mournful occasion to remember those who perished at the hands of the Nazis and their collaborators. The Holocaust, a catastrophic event in human history, resulted in the extermination of one-third of the Jewish population in Europe — totaling six million Jews during the Second World War. It also claimed the lives of countless others from minority and disability groups targeted under the Nazis' brutal regime of intolerance.
At Cloudflare, through Project Galileo, we are committed to safeguarding Jewish and Holocaust educational websites. This initiative offers complimentary protection to vulnerable groups worldwide. You can apply for the project using this form.
Combating antisemitism with education and cyber defense
Today more than ever, it’s important to ensure educational websites about the Holocaust are protected and available. Education about the Holocaust helps communities understand the dangers of prejudice and dehumanization, and can play an important role in combating antisemitism. As only 13 countries worldwide have mandated Holocaust education, publicly available resources play an important role in ensuring access to information.
According to the Anti-Defamation League, over 1 billion people globally are reported to hold antisemitic attitudes. In the United States, the Continue reading