Dell EMC Expands Server Capabilities for Software-defined, Edge and High-Performance Computing
 Launches highly capable enterprise-class single- and dual-socket servers Breaks down the cost barrier for deployment of emerging workloads Offers up to 20% better TCO per four-node cluster for vSAN deployments at the edge and are now available as vSAN Ready Nodes Dell EMC announced three new servers designed for software-defined environments, edge and high-performance computing... Read more →
Launches highly capable enterprise-class single- and dual-socket servers Breaks down the cost barrier for deployment of emerging workloads Offers up to 20% better TCO per four-node cluster for vSAN deployments at the edge and are now available as vSAN Ready Nodes Dell EMC announced three new servers designed for software-defined environments, edge and high-performance computing... Read more →
Tune Into Our CCIE SPv4.1 Advanced Technologies Course This Wednesday and Thursday!
Join 5 time CCIE Rohit Pardasani for our new online live sessions, CCIE Service Provider v4.1 Advanced Technologies. These live sessions are available to All Access Pass members via our live classroom interface, which you can access through your members account. For those who are not All Access Pass members, you can view and purchase AAP packages here. Read on to learn more about this online live class.
When: Wednesday, February 7th & Thursday, February 8th at 8 am PDT
Why You Should Watch: This SPv4.1 class will complete the SPv4.1 courses and bring us current for the Cisco Service Provider Blueprints.
Instructor info: Rohit Pardasani, CCIE #21282, CCSI #34999
About the Instructor:
Rohit has been in the networking industry for more than 17 years, with a focus on Cisco networking for the past 15 years. Rohit not only brings his years of teaching experience to the classroom, but also years of real-world enterprise and service provider experience. Rohit has assisted hundreds of engineers in obtaining their CCIE certification, and has been conducting CCIE RS, CCIE SEC, CCIE SP and CCIE Collaboration for Cisco Systems worldwide. Rohit currently holds 5xCCIE’s (Routing Switching, Service Provider, Security, Voice and Continue reading
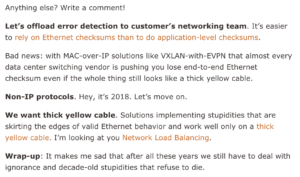
Response: The Need For Stretched VLANs (@ioshints)
A recent post from Ivan Pepelnjak entitled Revisited: The Need For Stretched VLANs
made me smile rather bitterly as Ivan dug into the apparent continued desire for stretched layer 2 networks and the reasons
people give for the solution’s requirement and validity. I love a good bit of snark as much as the next nerd, so as you can imagine, I’m all over that post.

However, I confess I did wince slightly – in the way one might do when an old wound is poked with a sharp stick – as Ivan made a passing sarcastic reference to Microsoft’s amazing Network Load Balancing technology:
My mind was thrown back to the heady days of 2009 when I stumbled across another post from Mr Pepelnjak, this time entitled Turn a switch into a hub … the Microsoft Way
which bemoaned the unadulterated stupidity of Microsoft’s attempt to use layer 2 network flooding to accomplish clustering. I had discovered the nature of this behavior at a previous client and had my mind blown by the very stupid and non-standards-compliant way in which this had been implemented.
The reason my mind went to that post, however, is because if I recall correctly it’s Continue reading
Some Market Thoughts on the Broadcom SDKLT
Broadcom, to much fanfare, has announced a new open source API that can be used to program and manage their Tomahawk set of chips. As a general refresher, the Tomahawk chip series is the small buffer, moderate forwarding table size hardware network switching platform on which a wide array of 1RU (and some chassis) routers (often called switches, but this is just a bad habit of the networking world) used in large scale data centers. In fact, I cannot think of a single large scale data center operating today that does not somehow involve some version of the Tomahawk chip set.
What does this all mean? While I will probably end up running a number of posts on SDKLT over time, I want to start with just some general observations about the meaning of this move on the part of Broadcom for the overall network engineering world.
This is a strong validation of a bifurcation in the market between disaggregation and hyperconvergence in the networking world. Back when the CCDE was designed and developed, there was a strong sense among the folks working on the certification that design and operations were splitting. This trend is still ongoing, probably ultimately resulting Continue reading
Open Source Storage System Vitess Joins CNCF
 YouTube developed Vitess because it needed to scale massive amounts of traffic.
YouTube developed Vitess because it needed to scale massive amounts of traffic.
Broadcom Increases Qualcomm Takeover Bid to $121 Billion
 The semiconductor firm says this is its “best and final” offer.
The semiconductor firm says this is its “best and final” offer.
Response: Intent-based networking portends the future of infrastructure management
 Kurt Marko does a great job of explaining Intent Based Networking as an overall trend. I broadly agree with this perspective. Intent based networks are the new hotness among those needing a response to network complexity. We provide the 101 along with a reality check on what is available today. Intent-based networking portends the future […]
Kurt Marko does a great job of explaining Intent Based Networking as an overall trend. I broadly agree with this perspective. Intent based networks are the new hotness among those needing a response to network complexity. We provide the 101 along with a reality check on what is available today. Intent-based networking portends the future […]SDxCentral’s Top 10 Articles — January 2018
 Verizon boards the ONAP train; Huawei has yet another U.S. setback; and AWS and Salesforce want to say goodbye to Oracle.
Verizon boards the ONAP train; Huawei has yet another U.S. setback; and AWS and Salesforce want to say goodbye to Oracle.
Related Stories
Network Break 170: Broadcom Opens SDK; Cisco Launches Container Platform
The Network Break analyzes Broadcom open-sourcing its SDK, Cisco announces a container platform & other new products, Dell considers an IPO & more. Eyvonne Sharp is our guest. The post Network Break 170: Broadcom Opens SDK; Cisco Launches Container Platform appeared first on Packet Pushers.ONF Gears Up for Large-Scale CORD Demo at MWC
 The ONF admits work is still needed before CORD is ready for deployments.
The ONF admits work is still needed before CORD is ready for deployments.
Connecting the Internet of Things: 4 Steps
Follow these guidelines to streamline the deployment and management of IoT devices on the network.
Cisco Cloud Index: Data Center SDN to Skyrocket by 2021
 More than two-thirds of all data centers will fully or partially adopt SDN by 2021.
More than two-thirds of all data centers will fully or partially adopt SDN by 2021.