Not All Content Needs the Edge
 The combination of edge computing, 5G RAN, and low latency will deliver a faster 5G experience.
The combination of edge computing, 5G RAN, and low latency will deliver a faster 5G experience.
BiB 30: Mellanox, Ixia & Cumulus At NFD17 – VXLAN & Whitebox
Mellanox, Ixia, and Cumulus Networks shared the presentation stage at Networking Field Day 17 to talk EVPN VXLAN, whitebox switching, open source, and data center design and performance validation.
The post BiB 30: Mellanox, Ixia & Cumulus At NFD17 – VXLAN & Whitebox appeared first on Packet Pushers.
Citrix Emphasizes Cloud, Networking, and Subscriptions in Q4 2017 Earnings
 Citrix said its Netscaler SD-WAN platform is beginning to see larger deployments.
Citrix said its Netscaler SD-WAN platform is beginning to see larger deployments.
Verizon Sets its Sights on a Nationwide NB-IoT Network
 T-Mobile also will have a nationwide NB-IoT network this year.
T-Mobile also will have a nationwide NB-IoT network this year.
BiB 029: Cisco At NFD17 – Automation, Telemetry & Intent
Cisco Systems presented at Networking Field Day 17. Three broad themes emerged from the presentations: intent, automation, and telemetry.
The post BiB 029: Cisco At NFD17 – Automation, Telemetry & Intent appeared first on Packet Pushers.
Coming soon to a university near you

Attention software engineering students: Cloudflare is coming to the University of Illinois at Urbana-Champaign and the University of Wisconsin–Madison, and we want to meet you! We will be attending UW–Madison’s Career Connection on Wednesday, February 7 and UIUC’s Startup Career Fair on Thursday, February 8. We’ll also be hosting tech talks at UIUC on Friday, February 2 at 6:00pm in 2405 Siebel Center and at UW–Madison on Tuesday, February 6 (time and location coming soon).

Cloudflare staff at YHack 2017. Photo courtesy Andrew Fitch.
Built in Champaign
In early 2016, Cloudflare opened an engineering office in Champaign, IL to build Argo Smart Routing. Champaign's proximity to the University of Illinois, one of the nation's top engineering schools, makes it an attractive place for high-tech companies to set up shop and for talented engineers to call home. Since graduating from UIUC in 2008, I've had opportunities to work on amazing software projects, growing technically and as a leader, all while enjoying the lifestyle benefits of Champaign (15 minute commute, anyone?).
Cloudflare has attended annual recruiting events at UIUC since the Champaign office was opened. This year, we've started to expand our search to other top engineering schools in the midwest. Continue reading
Riverbed’s SteelFusion Solves a County’s IT Backup Problem
 SteelFusion seems a little bit like hyperconverged infrastructure, but not exactly.
SteelFusion seems a little bit like hyperconverged infrastructure, but not exactly.
Red Hat and Mycom OSI Tackle Telco Cloud Assurance in NFV Environments
 It provides visibility and analysis for telcos as they move toward "cloudification."
It provides visibility and analysis for telcos as they move toward "cloudification."
Nokia Stock Surges on Strong Earnings, Positive Sentiment
 CEO Rajeev Suri cited improved conditions in North America and 5G momentum.
CEO Rajeev Suri cited improved conditions in North America and 5G momentum.
Broadcom Releases Open Source Software Development Kit for Data Center Switches
 The first version of the kit will allow customization of the company’s data center switches.
The first version of the kit will allow customization of the company’s data center switches.
AT&T CEO Says Tax Windfall Will Boost Capex by $1B in 2018
 Much of the extra investment will go toward building more fiber.
Much of the extra investment will go toward building more fiber.
Off the Cuff – NFD17 Wrap Up
Networking Field Day 17 (NFD17) was in Silicon Valley last week, with two of our co-founders participating as delegates – but the conversation doesn’t have to stop there. In this Off The Cuff episode of Network Collective, we’ve gathered a few of the delegates from the event to talk about their impressions on the information that was presented and some of the broader themes they experienced across the presentations. Vendors at the invent included Cisco, Cumulus, Extreme, Ixia, Juniper, Mellanox, Thousand Eyes, and VMware.
You can check out the event and see the presentations for yourself over at the Event Page at techfieldday.com.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post Off the Cuff – NFD17 Wrap Up appeared first on Network Collective.
Rehashing Certifications
While at Cisco Live in Barcelona this week, I had a chat with someone—I don’t remember who—about certifications. The main point that came out of the conversation was this:
One of the big dangers with chasing a certification is you will end up chasing knowledge about using a particular vendor feature set, rather than chasing knowledge about a technology.
At some point I’m going to edit a post a video short on engineering versus meta-engineering (no, it won’t be next week), but the danger is real. For instance, in an article I’ve had in my bookmarks pile for a long while, the author says—
I’m not going to name the author, because this is his description of thinking through a certification many years ago, rather than his current thinking on certifications—but the example is telling. I know a lot of folks studying for certifications. They mostly spend their time labbing up various protocols and… features. The temptation to Continue reading
Cloudflare Workers is now on Open Beta
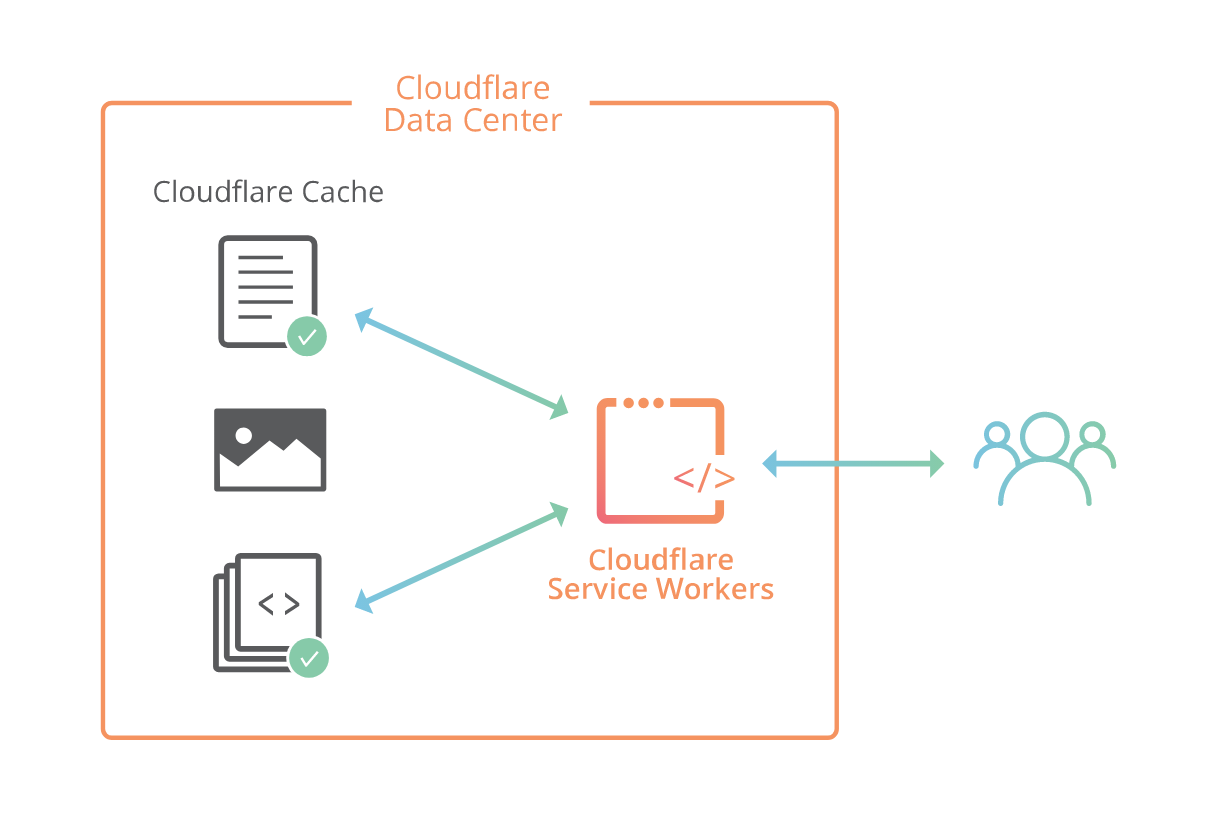
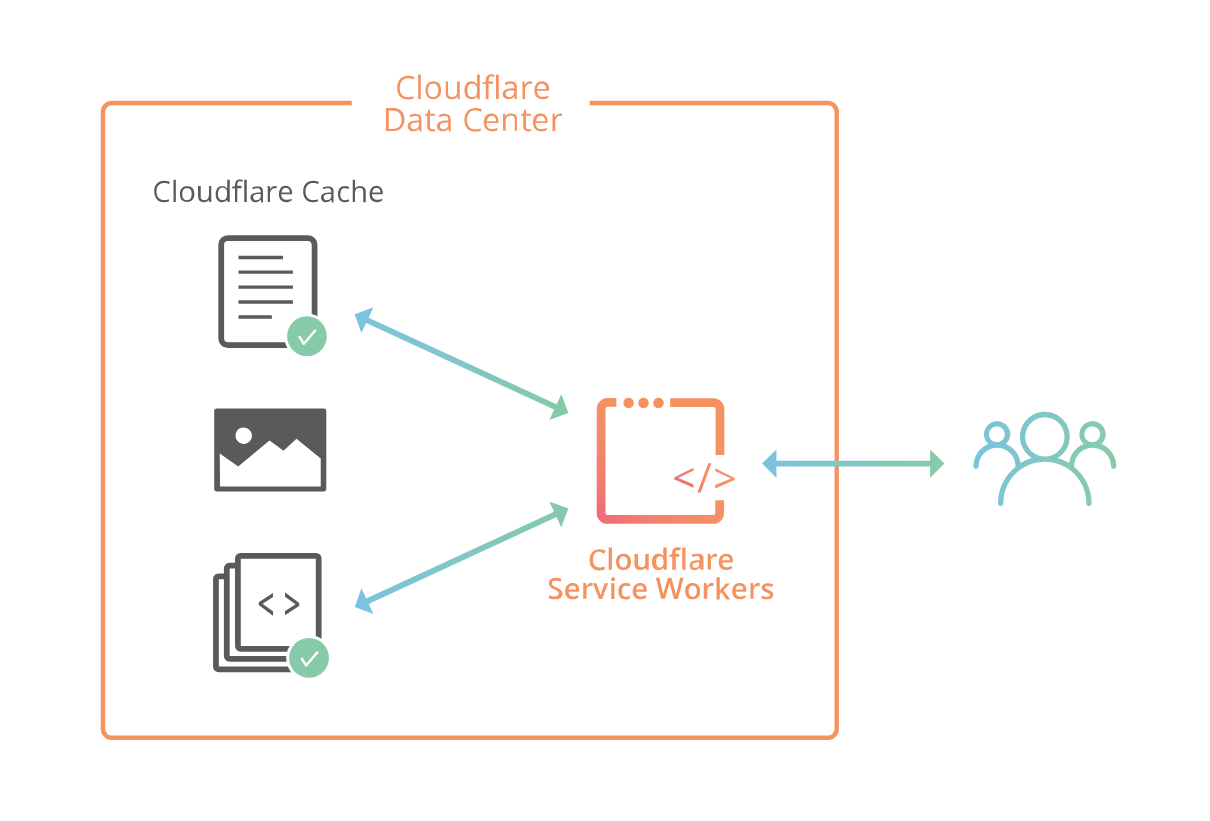
Cloudflare Workers Beta is now open!
Cloudflare Workers lets you run JavaScript on Cloudflare’s edge, deploying globally to over 120+ data centers around the world in less than 30 seconds. Your code can intercept and modify any request made to your website, make outbound requests to any URL on the Internet, and replace much of what you might need to configure your CDN to do today. Even better, it will do this from all our edge locations around the world, closer to many of your users than your origin servers can ever be. You will have a fully functional Turing-complete language in your fingertips which will allow you to build powerful applications on the edge. The only limit is your imagination.
To get started:
- Sign in to your account on cloudflare.com.
- Visit the Workers tab.
- Launch the editor.
- Write some code and save it.
- Go to the routes tab and prescribe on what requests you want to run Workers for
That’s it!
You can start by writing a simple ‘hello world’ script, but chances are that you are going write Workers that are more complicated. You can check out our page with recipes to:
Heptio Sideswipes Other Container Distros with ‘True’ Kubernetes Platform
 The HKS container platform is targeted at technically sophisticated organizations.
The HKS container platform is targeted at technically sophisticated organizations.
3 Bad Habits NetOps Should Avoid
Don't make these mistakes when adopting DevOps for production network automation and orchestration.



