Tangoe State of IT Spending: A Look Back and Ahead
Tangoe’s annual IT Trends and Savings Recommendation report recaps IT spending in 2023 and provides savings tips for 2024.Making Networking Cool Again? (2)
Network engineering is not “going away.” Network engineering is not less important than it was yesterday, last year, or even a decade ago.
But there still seems to be a gap somewhere. There are fewer folks interested than we need. We need more folks who want to work as full-time network engineers, and more folks with network engineering skills diffused within the larger IT community. More of both is the right answer if we’re going to continue building large-scale systems that work. The real lack of enthusiasm for learning network engineering is hurting all of IT, not just network engineering.
How do we bridge this gap? We’re engineers. We solve problems. This seems to be a problem we might be able to solve (unlike human nature). Let’s try to solve it.
As you might have guessed, I have some ideas. These are not the only ideas in the world—feel free to think up more!
If you walk into a robotics class, even an introductory robotics class, you see people … building robots. If you walk into a coding class, even an introductory one, you see people … writing software. If you walk into a network network engineering class you Continue reading
Fulton County Schools: Five Lessons From a Massive Digital Transformation
Fulton County Schools CIO Dr. Emily Bell shares advice and lessons learned from the school’s major digital transformation that are applicable to organizations of all types.BGP Graceful Restart Considered Harmful
A networking engineer with a picture-perfect implementation of a dual-homed enterprise site using BGP communities according to RFC 1998 to select primary- and backup uplinks contacted me because they experienced unacceptably long failover times.
They measured the failover times caused by the primary uplink loss and figured out it takes more than five minutes to reestablish Internet connectivity to their site.
BGP Graceful Restart Considered Harmful
A networking engineer with a picture-perfect implementation of a dual-homed enterprise site using BGP communities according to RFC 1998 to select primary- and backup uplinks contacted me because they experienced unacceptably long failover times.
They measured the failover times caused by the primary uplink loss and figured out it takes more than five minutes to reestablish Internet connectivity to their site.
IP Addresses through 2023
Time for another annual roundup from the world of IP addresses. Let’s see what has changed in the past 12 months in addressing the Internet and look at how IP address allocation information can inform us of the changing nature of the network itself.IP Addresses through 2023
Time for another annual roundup from the world of IP addresses. Let’s see what has changed in the past 12 months in addressing the Internet and look at how IP address allocation information can inform us of the changing nature of the network itself.NB462: HPE Spends $14 Billion For Juniper Networks; Starlink Tests SMS Via Satellite
Take a Network Break! On today’s show we spend most of the episode talking about HPE’s $14 billion bid for Juniper Networks. We discuss reasons for the deal, product overlap, potential upsides, challenges to integrating these two companies and their product lines, and more. We also talk about a successful test by Starlink to send... Read more »Leveraging Network Support with Non-IT Personnel
As networks move to the edge, IT can’t always move with them. How do you maintain them? Here are tips to enlist paraprofessionals to help.Raspberry Pi 5 network emulation with Containerlab
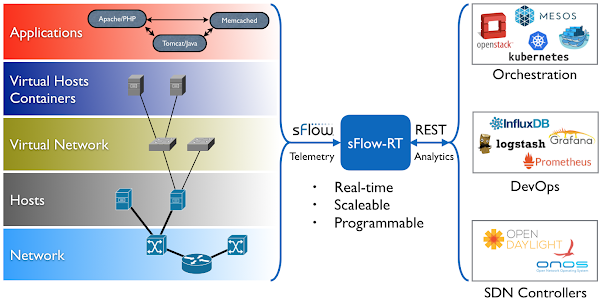
The GitHub sflow-rt/containerlab project contains example network topologies for the Containerlab network emulation tool that demonstrate real-time streaming telemetry in realistic data center topologies and network configurations. The examples use the same FRRouting (FRR) engine that is part of SONiC, NVIDIA Cumulus Linux, and DENT network operating systems. Containerlab can be used to experiment before deploying solutions into production. Examples include: tracing ECMP flows in leaf and spine topologies, EVPN visibility, and automated DDoS mitigation using BGP Flowspec and RTBH controls. Raspberry Pi 5 real-time network analytics describes how to install Docker on a Raspberry Pi 5.docker run hello-worldRun the hello-world container to verify that Docker in properly installed and running before proceeding.
git clone https://github.com/sflow-rt/containerlab.gitDownload the sflow-rt/containerlab project from GitHub.
cd containerlab ./run-clabStart Containerlab.
containerlab deploy -t clos5.ymlStart the 5 stage leaf and spine topology shown at the top of this page. The initial launch may take a couple of minutes as the container images are downloaded for the first time. Once the images are downloaded, the topology deploys in around 10 seconds.
./topo.py clab-clos5Push the topology to the sFlow-RT analytics software. An instance of the sFlow-RT Continue reading
Weekend Reads 011224
Yes, the weekend has pretty much already passed, but still …
The Atomic Stealer, also known as “AMOS,” first Continue reading
Public Videos: Large Language Models (AI/ML)

All the Large Language Models videos from the AI/ML in Networking webinar with Javier Antich are now public. Enjoy!
BGP in 2023 – BGP Updates
the scalability of BGP as the Internet’s routing protocol is not just dependant on the number of prefixes carried in the routing table. BGP protocol behaviour in the form of dynamic routing updates are also part of this story. If the update rate of BGP is growing faster than we can deploy processing capability to match, then the routing system will lose coherence, and at that point the network will head into periods of instability. This report looks at the profile of BGP updates across 2023 to assess whether the stability of the routing system, as measured by the level of BGP update activity, is changing.BGP in 2023 – BGP Updates
the scalability of BGP as the Internet’s routing protocol is not just dependant on the number of prefixes carried in the routing table. BGP protocol behaviour in the form of dynamic routing updates are also part of this story. If the update rate of BGP is growing faster than we can deploy processing capability to match, then the routing system will lose coherence, and at that point the network will head into periods of instability. This report looks at the profile of BGP updates across 2023 to assess whether the stability of the routing system, as measured by the level of BGP update activity, is changing.New Processors Help Modernize the Data Center for AI
Enterprise and cloud data centers are using new compute and networking processors to run and speed up today’s more complex AI workloads.Cloud Risk Management’s Time Has Come
The risks and stakes are growing as companies transfer more IT to the cloud. But are those companies really ready?HN716: Design-Driven Network Automation And Assurance
At AutoCon0 in November 2023, guest Jeremy Schulman delivered a talk from the main stage about delivering network assurance. If the term “network assurance” doesn’t mean anything to you, think about how you prove after an install or a change that the network is doing what it’s supposed to be doing. If you’re doing it... Read more »Where is all of the fediverse?
Where is all of the fediverse?
Spurred on by the problems at Twitter, a lot of my social media timeline has “moved out” of Twitter/“X” on to what people mostly describe as mastodon or
VXLAN/EVPN – Host routing
In an previous post Advertising IPs In EVPN Route Type 2, I described use cases for advertising IP addresses in EVPN route type 2. Host ARP and host mobility I already covered so today we will focus on host routing.
To be able to show this scenario, I have added another server (SERVER-2) and will be using the topology below:
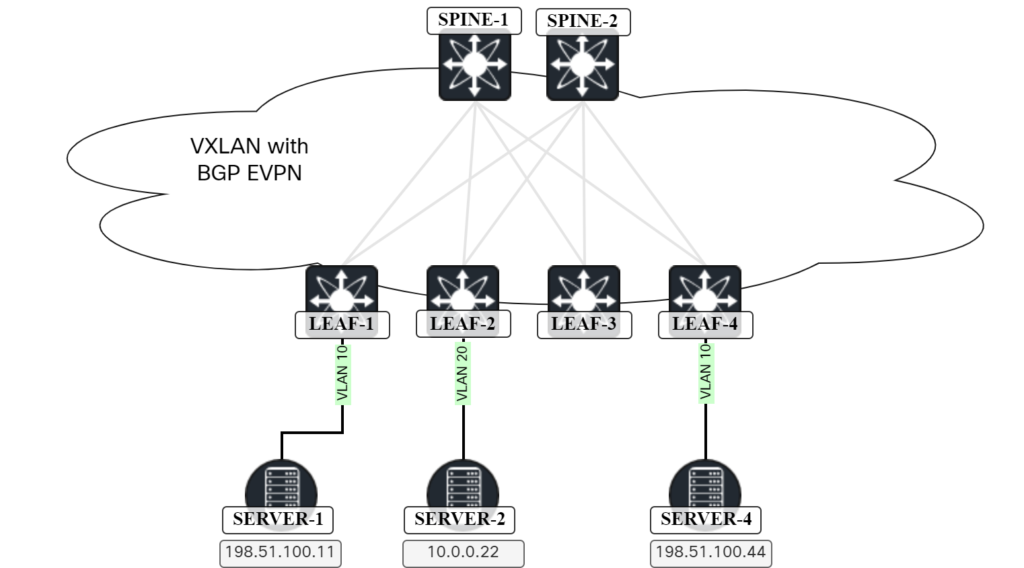
There is already existing configuration for VLAN 10 (L2 VNI) and for VLAN 100 (L3 VNI) which is shown below:
vrf context Tenant1
vni 10001
rd auto
address-family ipv4 unicast
route-target both auto
route-target both auto evpn
!
interface Vlan10
no shutdown
vrf member Tenant1
ip address 198.51.100.1/24
fabric forwarding mode anycast-gateway
!
interface Vlan100
no shutdown
mtu 9216
vrf member Tenant1
ip forward
To get SERVER-2 connected the following is needed:
- Configure VLAN 20 and map it to L2 VNI (VNI 10002).
- Make the L2 VNI a member of the NVE.
- SVI for VLAN 20.
- Configure port towards SERVER-2 in VLAN 20.
This is shown below:
vlan 20
vn-segment 10002
!
interface nve1
member vni 10002
ingress-replication protocol bgp
!
interface Vlan20
no shutdown
vrf member Tenant1
ip address 10.0.0.1/24
fabric forwarding mode anycast-gateway
!
interface Ethernet1/3
Continue reading
Is It The End, Or Can You Do Something in 2024?
David Bombal invited me for another annual chat last December, focusing on (what else) networking careers in 2024. The results were published a few days ago, and I was amazed at how good it turned out. I always love chatting with David; this time, his editing team did a masterful job.