2017 Internet Intelligence Roundup

With 2017 drawing to a close, year-end lookbacks litter media and the blogosphere like so many leaves on the ground. (Or piles of snow, depending on where you are.) Many tend to focus on pop culture, product/movie/music releases, or professional sports. However, given the focus of Oracle Dyn’s Internet Intelligence team on monitoring and measuring the Internet, we’re going to take a look back at significant Internet “events” of the past year, and how they have impacted connectivity for Internet users around the world.
Hurricanes Harvey, Irma, and Maria Cause Internet Disruptions
In late August, and through September, an active Atlantic hurricane season spawned a number of destructive storms that wreaked havoc across the Caribbean, as well as Florida and Texas in the United States. On the Caribbean islands that were hardest hit by the storms, the resulting physical damage was immense, severely impacting last-mile Internet infrastructure across the whole country. This was also the case in Florida and Texas, though on a much more localized basis. On September 25, we looked at the impacts of these hurricanes on Internet connectivity in the affected areas, noting that while some “core” Internet components remained available during these storms thanks to Continue reading
AT&T, Comcast Pledge Bonuses, CapEx Boost Tied to Tax Reform
 5G could benefit from AT&T's planned $1 billion CapEx increase.
5G could benefit from AT&T's planned $1 billion CapEx increase.
SD-WAN Vendor TELoIP Names Former AT&T Exec as CEO
 TELoIP’s Founder Pat Saavedra has resigned from the company.
TELoIP’s Founder Pat Saavedra has resigned from the company.
Amazon Web Services Gives in to Blockchain Craze
 If you can’t beat ’em, join ’em.
If you can’t beat ’em, join ’em.
Ericsson, Qualcomm Achieve 5G Interoperability Using New Standard
 The demo used Ericsson pre-commercial base stations and Qualcomm prototype devices.
The demo used Ericsson pre-commercial base stations and Qualcomm prototype devices.
2018 and the Internet: our predictions
At the end of 2016, I wrote a blog post with seven predictions for 2017. Let’s start by reviewing how I did.
 Public Domain image by Michael Sharpe
Public Domain image by Michael Sharpe
I’ll score myself with two points for being correct, one point for mostly right and zero for wrong. That’ll give me a maximum possible score of fourteen. Here goes...
2017-1: 1Tbps DDoS attacks will become the baseline for ‘massive attacks’
This turned out to be true but mostly because massive attacks went away as Layer 3 and Layer 4 DDoS mitigation services got good at filtering out high bandwidth and high packet rates. Over the year we saw many DDoS attacks in the 100s of Gbps (up to 0.5Tbps) and then in September announced Unmetered Mitigation. Almost immediately we saw attackers stop bothering to attack Cloudflare-protected sites with large DDoS.
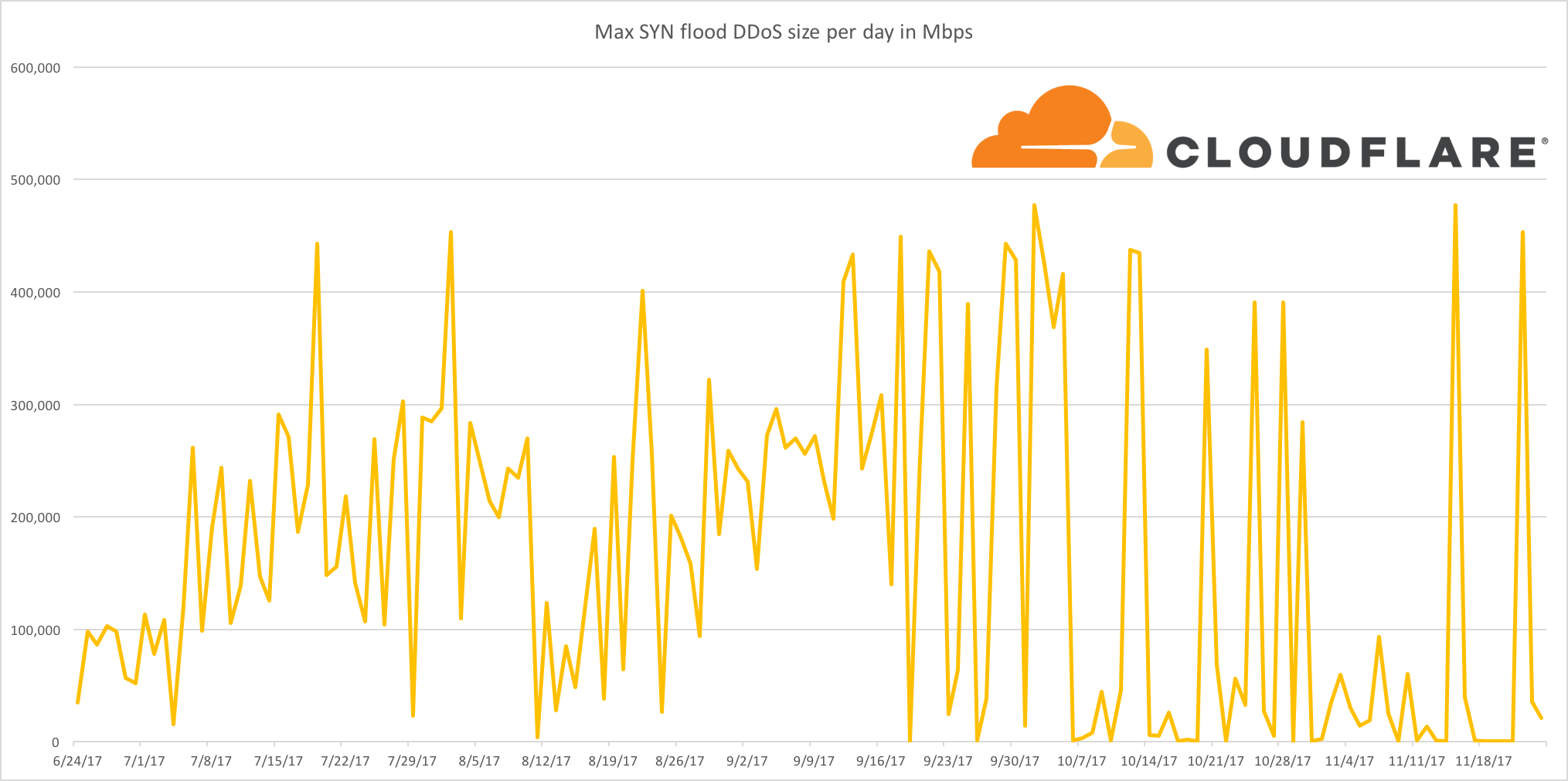
So, I’ll be generous and give myself one point.
2017-2: The Internet will get faster yet again as protocols like QUIC become more prevalent
Well, yes and no. QUIC has become more prevalent as Google has widely deployed it in the Chrome browser and it accounts for about 7% of Internet traffic. At the same time the protocol is working its Continue reading
2018 and the Internet: our predictions
At the end of 2016, I wrote a blog post with seven predictions for 2017. Let’s start by reviewing how I did.

Public Domain image by Michael Sharpe
I’ll score myself with two points for being correct, one point for mostly right and zero for wrong. That’ll give me a maximum possible score of fourteen. Here goes...
2017-1: 1Tbps DDoS attacks will become the baseline for ‘massive attacks’
This turned out to be true but mostly because massive attacks went away as Layer 3 and Layer 4 DDoS mitigation services got good at filtering out high bandwidth and high packet rates. Over the year we saw many DDoS attacks in the 100s of Gbps (up to 0.5Tbps) and then in September announced Unmetered Mitigation. Almost immediately we saw attackers stop bothering to attack Cloudflare-protected sites with large DDoS.

So, I’ll be generous and give myself one point.
2017-2: The Internet will get faster yet again as protocols like QUIC become more prevalent
Well, yes and no. QUIC has become more prevalent as Google has widely deployed it in the Chrome browser and it accounts for about 7% of Internet traffic. At the same time the protocol is working its Continue reading
BiB 022: CloudPassage Adds Container Security To Halo Platform
CloudPassage talked with the Packet Pushers about Container Secure, a product announcement they made at AWS re:Invent earlier this year. Ethan Banks shares his impressions.
The post BiB 022: CloudPassage Adds Container Security To Halo Platform appeared first on Packet Pushers.
GDPR: Looking Beyond the Burden
All companies can learn something from the EU data protection regulation.
Wow, another Year Swooshed By…
Could you believe it? Another year swooshed by… and it’s high time to stop being snarky and cynical, disconnect from the Internet, and spend a few days with people who really matter – our families.
For me, there’s another large group of people that matter: my users.
Read more ...3GPP Approves First 5G Specification
 The 5G NR specification is a stepping stone on the path to a global 5G standard.
The 5G NR specification is a stepping stone on the path to a global 5G standard.