Deploy360 at IETF 100, Day 5: Zaìjiàn from the Lion City
There’s a couple of sessions of interest on the last day of IETF 100 before we wrap up for the week. Friday is only a half-day, but still manages to fit in sessions on human rights considerations and encryption. Human rights is not a topic that Deploy360 typically covers, but we have been increasingly asked to discuss the IRTF initiative on Human Rights Protocols Considerations. (There’s also a recent IETF Journal article on Human Rights Protocol Considerations.)
HRPC is researching the human rights threats on the Internet, whether standards and protocols can enable or threaten these, and is developing recommendations on developing Internet protocols around this. It recently published RFC 8080 outlining human rights threats on the Internet, and will be meeting at 09.30 SGT/UTC+8 to discuss three other drafts relating to Freedom of Association on the Internet, the Politics of Standards, and Unrequested Communications. There will also be a presentation on Chainiac: end-to-end software supply chain security and transparency, plus the next steps forward will be discussed.
NOTE: If you are unable to attend IETF 100 in person, there are multiple ways to participate remotely.
PERC is also meeting at the same time, and has three drafts up for discussion. Continue reading
IPv6 Migration: 5 Best Practices
Follow these expert tips to smooth the process of adopting the new Internet Protocol standard.
Pluribus Networks… 2 Years Later
I first met Pluribus Networks 2.5 years ago during their Networking Field Day 9 presentation, which turned controversial enough that I was advised not to wear the same sweater during NFD16 to avoid jinxing another presentation (I also admit to be a bit biased in those days based on marketing deja-moo from a Pluribus sales guy I’d been exposed to during a customer engagement).
Pluribus NFD16 presentations were better; here’s what I got from them:
Read more ...One Week to IPv6, Routing Security, and More at ION Belgrade
One week from today, we’ll be at ION Belgrade! Our last event of the year take place on Thursday, 23 November 2017, alongside the 3rd Republic of Serbia Network Operators’ Group (RSNOG).
As always, ION Conferences bring network engineers and leading industry experts together to discuss emerging technologies and hot technology topics. Early adopters provide valuable insight into their own deployment experiences and bring participants up to speed on new standards emerging from the IETF.
Agenda
The half-day agenda and all our great speakers for ION Belgrade will make this a great event. Here’s a quick look at the day:
- Opening Remarks
- Welcome from the ISOC Serbia Chapter
- MANRS, Routing Security, and Collaboration
- NAT64check
- What’s Happening at the IETF? Internet Standards and How to Get Involved
- Panel Discussion: IPv6 Success Stories
- Closing Remarks
Registration
ION Belgrade registration is open! Learn more about our co-host on the RSNOG main page.
Webcast
RSNOG will be live streaming the ION in the morning and RSNOG in the afternoon. The stream will be embedded on the conference main page, right above the agenda, here (Serbian) and here (English).
IPv6 Tutorial
Jordi Palet Martinez will conduct an IPv6 training session the day before the ION. Continue reading
Basics of VRF(Virtual Routing forwarding)
Cisco Security Revenue Grew 8% in Fiscal Q1 2018
 Revenue from the company's core business of routers and switches declined 4 percent.
Revenue from the company's core business of routers and switches declined 4 percent.
How to gauge your network’s openness
So, you’ve done your research, learned about the many benefits of open networking, and decided you’re interested in building an open network. Congratulations, and welcome to the future of networking! You’ve made a great first step, but maybe you’re concerned about where to begin when it comes to vendors. A lot of network providers will claim that they have open solutions…but how can you be sure you’re choosing the best one? Or how can you determine if your vendor is truly an open solution? Fortunately, there are ways to gauge if your solution is as open as you need it to be. If you don’t want to get duped by phony open vendors, make sure to keep these three things in mind:
The definition of “open networking” is not set in stone
While there are common criteria and ideologies that tend to be associated with open networks, the definition of open networking is still very fluid and can mean different things to different vendors. So, when you’re trying to decide which vendor to go with, don’t let them off easy with simple answers. Ask specific questions about what exactly “open” means to them. Simplicity, flexibility, and modularity are Continue reading
Security with Fish: My First Couple Months
In late June I wrote Security Here I Come! The transition wasn’t quite as fast as I thought it would be.  But for the past couple months I’ve been able to really start digging in.
But for the past couple months I’ve been able to really start digging in.
My initial response after watching just 2 CiscoLive VoDs? FEAR!
- Defense Against Emerging Threats – BRKSEC-1010 by Neil Lovering
- Simple Hacking Tools For Your Own Network – BRKSEC-1008 by Jerry Lin
I really enjoyed these sessions a great deal!! They were the absolute perfect eye-opener to me!
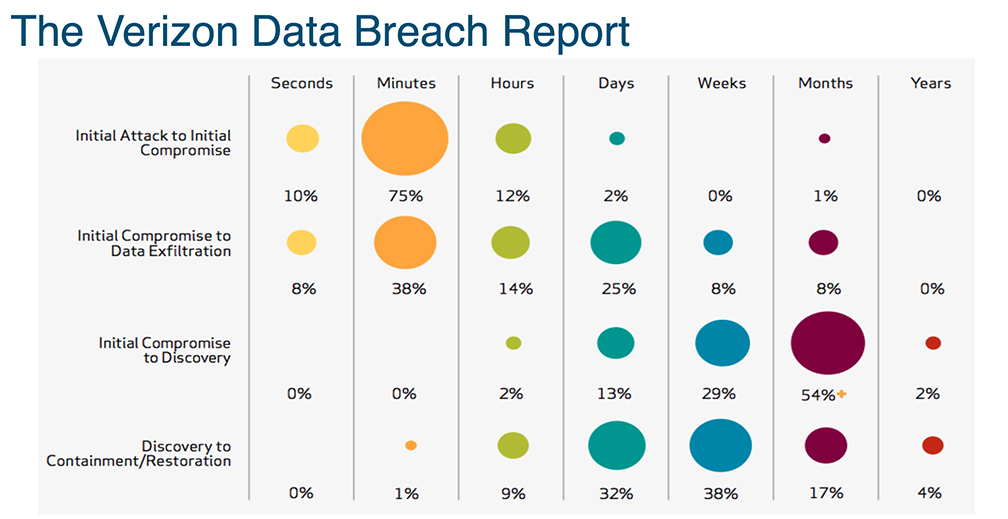
Neil Lovering had the “Verizon Data Breach Report” in his slides (below).
Its funny because I have seen it before. To be completely honest I have seen it quite a number of times. But it was just something about how he presented it. He got past my not wanting to really “hear” about the risk and the danger and the reality of the security landscape in the world around us. I paused the VoD on this slide…. paused it and just really took the time to take it all in.
My reaction to this slide? Lol. This is when the fear began. Two simple facts on the Continue reading
Security with Fish: My First Couple Months
In late June I wrote Security Here I Come! The transition wasn’t quite as fast as I thought it would be.  But for the past couple months I’ve been able to really start digging in.
But for the past couple months I’ve been able to really start digging in.
My initial response after watching just 2 CiscoLive VoDs? FEAR!
- Defense Against Emerging Threats – BRKSEC-1010 by Neil Lovering
- Simple Hacking Tools For Your Own Network – BRKSEC-1008 by Jerry Lin
I really enjoyed these sessions a great deal!! They were the absolute perfect eye-opener to me!
Neil Lovering had the “Verizon Data Breach Report” in his slides (below).
Its funny because I have seen it before. To be completely honest I have seen it quite a number of times. But it was just something about how he presented it. He got past my not wanting to really “hear” about the risk and the danger and the reality of the security landscape in the world around us. I paused the VoD on this slide…. paused it and just really took the time to take it all in.
My reaction to this slide? Lol. This is when the fear began. Two simple facts on the Continue reading
Facebook Open Sources Its Routing Platform
Social media giant aims to advance the state of networking with Open/R.
Cisco’s 2017 Buying Spree: From AppDynamics to Viptela, and More
 The company has spent at least $6.6B on software-centric companies.
The company has spent at least $6.6B on software-centric companies.
Related Stories
AT&T, Orange, and Partners Shrink the World Using MEF LSO, ONAP
 Both operators and the LSO APIs rely on ONAP.
Both operators and the LSO APIs rely on ONAP.
IHS: Cisco, VMware in SD-WAN Market ‘Two-Horse Race’
 The SD-WAN market is forecast to reach $3.3 billion in revenue by 2021.
The SD-WAN market is forecast to reach $3.3 billion in revenue by 2021.