FRRouting Software with EIGRP Support
In September 2016 I wrote the article about EIGRP support in Quagga network routing suite. More than one year later, I am going to check the progress of development EIGRP in Linux again. To do so, I have installed a fork of Quagga - FRRouting (FRR) with EIGRP support on Linux Core. EIGRP routing daemon included inside FRR benefits from active development brought by Cumulus employees. For the purpose of FRR testing, I have created a minimalistic Linux Core Pure64 virtual machine with FRR suite compiled as frr extension. Meanwhile, I have submitted FRR extension so it will be available in the next few days in Tinycore repository.
Content of Disk - CorePure64-frr_3-1.vmdk:
- Linux Core Pure 64 version 8.2,kernel 4.8.17
- FRRouting 3.1dev
- OpenSSL 1.0.2l 25 May 2017
- OpenSSH_7.2p2
- GNU bash, 4.4.0(1)
- iproute2-ss140411
- iptables v1.4.21
- tcpdump 4.7.4
- Nmap 7.12
- mtr 0.86
- hping 3.0.0-alpha-1
- iperf 3.1b3
- D-ITG 2.8.1 (r1023)
Software:
- Host OS - Ubuntu 16.04.3 LTS x64
- GNS3 2.0.3
- QEMU x64 emulator version 2.8.0
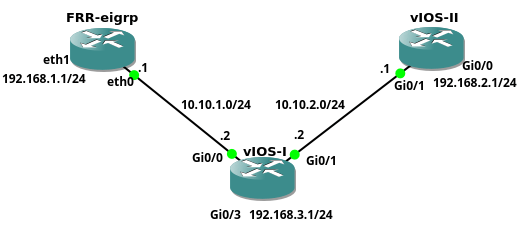 Picture 1 - Network Topology
Picture 1 - Network Topology
The FRR EIGRP instance with attached CorePure64-frr_3-1.vmdk Continue reading
PQ 134: Meet ZeroTier – Open Source Networking
Today's Priority Queue dives into ZeroTier, an open source project for building virtual networks including VPNs, SDN, and SD-WAN. Our guest is founder Adam Ierymenko. The post PQ 134: Meet ZeroTier – Open Source Networking appeared first on Packet Pushers.Abstract, Automate & Secure — From Data Center to Cloud to Edge
By Milin Desai, Vice President of Products, NSBU
It feels like only yesterday when we started our journey into networking at VMware. Even from the early beginnings in 2011, it became clear to some of us that the abstraction and operations model of virtualization for compute and memory, which completely transformed the modern data center, was something we needed to extend to networking. We understood that that a network based on software and abstraction in the long run would extend beyond our customers’ data centers to public clouds and ultimately to the Edge.
We’ve been executing on this vision for almost eight years; reinventing data center networking and enabling our customers to be smarter about how they secure, manage and connect their applications and users.
Starting with the Data Center
The Nicira acquisition, alongside our internal innovations, resulted in the release of VMware NSX in 2013. VMware NSX made network virtualization a mainstream possibility for the data center. The goal was simple — abstract the application from the physical network and deliver the networking attributes in software at machine speeds. After four years, multiple thousands of customers and the creation of a billion-dollar run rate business, we have transformed the Continue reading
Network Optimization for Cloud Access
With the growth of cloud services, enterprises need to ensure users don't run into network bottlenecks.
Network Optimization for Cloud Access
With the growth of cloud services, enterprises need to ensure users don't run into network bottlenecks.
Where Does Automation Fit into Enterprise IT?
One of my readers coming from system development area asked a fundamental question about the role of automation in enterprise IT (somewhat paraphrased):
[In system development] we automate typical tasks from the pre-defined task repository, so I would like to understand broader context as the automation (I guess) is just a part of the change we want to do in the system. Someone needs to decide what to do, someone needs to accept the change and finally the automation is used.
Of course he’s absolutely right.
Read more ...Docker Networking Tip – Troubleshooting
Debugging Container and Docker Networking issues can be daunting at first considering that containers do not contain any debug tools inside the container. I normally see a lot of questions around Docker networking issues in Docker and stackoverflow forum. All the usual networking tools can be used to debug Docker networking, it is just that … Continue reading Docker Networking Tip – TroubleshootingPTT – Push To Talk
When was the last time you were looking for the unmute button in Webex and it took you more than two seconds to find it?When was the last time you thought you are on mute but actually everyone can hear you snore?
I spend a lot of time in conference calls. This mute thing happens to me a lot.
PTT stands for Push To Talk like we used in walkie-talkies. The computer mic would be normally muted and as long as I press the PTT button, it will unmute the mic.
I couldn't find any such off the shelf device, so I decided to create one on my own.
To do so I had to integrate few components. Here is the flow of things:
When I press a button on my special device, it will send the key combination of "PrintScreen+F11". Then a special program called AutoHotKey will intercept that key combination and execute an application I wrote that controls the computer mic.
The PTT button
IBM Cloud Private Bets on Containers to Bridge Hybrid Clouds
 The software platform is built on open source Kubernetes-based container architecture.
The software platform is built on open source Kubernetes-based container architecture.

