Decoding LACP Port State
It’s frustrating when the output to a show command gives exactly the information needed, but in a format which is unintelligible. So it is with the Partner Port State field in the NXOS show lacp neighbor interface command which reports the partner port state as a hexadecimal value. To help with LACP troubleshooting, here’s a quick breakdown of the port states reported on by LACP, and how they might be seen in Junos OS and NXOS.
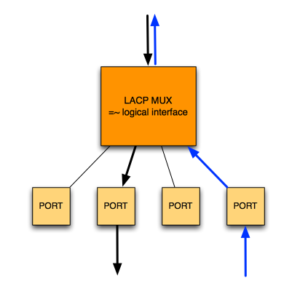
LACP Port State
The LACP port state (also known as the actor state) field is a single byte, each bit of which is a flag indicating a particular status. In this table, mux (i.e. a multiplexer) refers to the logical unit which aggregates the links into a single logical transmitter/receiver.
The meaning of each bit is as follows:
| Bit | Name | Meaning |
|---|---|---|
| 0 | LACP_Activity | Device intends to transmit periodically in order to find potential members for the aggregate. This is toggled by mode active in the channel-group configuration on the member interfaces.1 = Active, 0 = Passive. |
| 1 | LACP_Timeout | Length of the LACP timeout. 1 = Short Timeout, 0 = Long Timeout |
| 2 | Aggregation | Will allow the link to be aggregated. 1 = Continue reading |
Cloud Native: Upgrading a Workflow Engine or Orchestrator
On a train this morning, I read Ivan Pepelnjak’s Twitter stream (because what else is there to do whilst relaxing with a coffee?), I came across this blog post on upgrading virtual-appliances.
Couldn’t agree more with the approach, but what about upgrading a workflow engine or orchestrator? I’ll call this entity a ‘wfeo’ just to make typing this article easier.
The perceived turmoil in undertaking this kind of an upgrade task is enough to make new born babies cry. Fear not. Any half decent wfeo contains it’s gubbins (workflows, drivers, logic, data) in a portable and logical data structure.
Taking StackStorm as an example, each integration (official parlance; ‘pack’), is arranged into a set of directories.
Within each directory are more directories with special names and a set of files like READMEs, configuration schemas and pack information. These top level directories that contain the pack, are portable between install bases of StackStorm giving us the power to easily clone installations, repair logic in case of a troubled upgrade and install logic freshly for new installations.
As with any platform, some syntax might change so always read the release notes for the platform and packs.
Ivan’s point is that you Continue reading
The Flawed Hunt for IT Talent
IT leaders often rely on lengthy job descriptions to fill openings, overlooking latent talent.
The Flawed Hunt for IT Talent
IT leaders often rely on lengthy job descriptions to fill openings, overlooking latent talent.
IETF 100 Hackathon: Bringing Innovation and Running Code to the IETF
Interested in contributing running code to the Internet Engineering Task Force (IETF)? Do you see a problem with DNS, DNSSEC, IPv6, TLS, or something else that you want to help fix?
The IETF is holding its next meeting in Singapore in November. Just before IETF 100, on 11-12 November, is a Hackathon to encourage developers to discuss, collaborate and develop utilities, ideas, sample code and solutions that show practical implementations of IETF standards.
Check out the Hackathon Wiki to learn more about how to register, get involved in a project, add your own topic of interest, or even participate remotely if you can’t make it to Singapore next month. You can also read more about a past Hackathon in this IETF Journal article.
As an added bonus, there are some prizes on the line! A panel of judges announces winners in several categories at the end of the event, with winners choosing from sponsor-donated prizes.
Remember, the IETF needs operational expertise to make sure its protocols and standards actually work in real life networks.
The post IETF 100 Hackathon: Bringing Innovation and Running Code to the IETF appeared first on Internet Society.
Upgrading Virtual Appliances
In every SDDC workshop I tried to persuade the audience that the virtual appliances (particularly per-application instances of virtual appliances) are the way to go. I usually got the questions along the lines of “who will manage and audit all these instances?” but once someone asked “and how will we upgrade them?”
Short answer: you won’t.
Read more ...Qualcomm Says Mobile 5G Will Be Real in First Half of 2019
 San Diego firm says it has a 5G smartphone reference design ready for testing.
San Diego firm says it has a 5G smartphone reference design ready for testing.
NSX Real World Use Cases for Pivotal Cloud Foundry
Pivotal cloud foundry is the leading PaaS solution for enterprise customers today, providing a fast way to convert their ideas from conception to production. This is achieved by providing a platform to run their code in any cloud and any language taking care of all the infrastructure stuff for them.
From building the container image, compiling it with the required runtime, deploying it in a highly available mode and connecting it to the required services, PCF allows dev shops to concentrate on developing their code.
While the platform is providing developers with the most simplified experience conceivable, under the hood there are many moving parts that make that happen and plumbing all these parts can be complex. That’s where customers are really enjoying the power of VMware’s SDDC, and the glue between the PaaS and SDDC layers is NSX, it is the enabler that makes it all work.
In this blog post, I detail some of the main uses cases customers has already deployed NSX for PCF on top of vSphere and how PCF and NSX are much better together in the real world.
The use cases customers are deploying with NSX for PCF are varied and ill divide them Continue reading
Hyperledger Stitches in Another Blockchain Project
 The Quilt project focuses on transactions across ledgers.
The Quilt project focuses on transactions across ledgers.
WPA2 KRACK Fallout in the Enterprise
WiFi networking pros sort out details about the security flaws and take steps to shore up business WLANs.
WPA2 KRACK Fallout in the Enterprise
WiFi networking pros sort out details about the security flaws and take steps to shore up business WLANs.
KRACK proves we need more encryption on the Internet
A serious weakness in Wi-Fi security was made public earlier today. The Key Reinstallation Attack (KRACK) can break Wi-Fi encryption, opening your data up to eavesdropping. This, combined with issues in Linux and Android, make it possible for attackers to change websites you view. This is a serious problem for Wi-Fi Protected Access 2 (WPA2), a protocol used in millions of networks worldwide.
Luckily, the use of Transport Layer Security (TLS) is on the rise. Mozilla’s data shows that over 60% of pages loaded in Firefox use TLS. More and more companies are using encryption for all traffic and removing the ability to connect to unencrypted versions of their sites. When connecting to these sites, KRACK isn’t as big of a deal, because the data is encrypted before it’s sent across Wi-Fi. Even if WPA2 is broken, the data is still secure.
Unfortunately there are still millions of sites that don’t provide this security. Their users are vulnerable to eavesdropping, fake content, malware injection, and more. We need more companies and operators to use TLS and HTTP Strict Transport Security (HSTS) to mitigate the potential impact of KRACK.
Internet traffic exists in layers, which makes it possible to use more Continue reading
KRACK proves we need more encryption on the Internet
A serious weakness in Wi-Fi security was made public earlier today. The Key Reinstallation Attack (KRACK) can break Wi-Fi encryption, opening your data up to eavesdropping. This, combined with issues in Linux and Android, make it possible for attackers to change websites you view. This is a serious problem for Wi-Fi Protected Access 2 (WPA2), a protocol used in millions of networks worldwide.
Luckily, the use of Transport Layer Security (TLS) is on the rise. Mozilla’s data shows that over 60% of pages loaded in Firefox use TLS. More and more companies are using encryption for all traffic and removing the ability to connect to unencrypted versions of their sites. When connecting to these sites, KRACK isn’t as big of a deal, because the data is encrypted before it’s sent across Wi-Fi. Even if WPA2 is broken, the data is still secure.
Unfortunately there are still millions of sites that don’t provide this security. Their users are vulnerable to eavesdropping, fake content, malware injection, and more. We need more companies and operators to use TLS and HTTP Strict Transport Security (HSTS) to mitigate the potential impact of KRACK.
Internet traffic exists in layers, which makes it possible to use more Continue reading
IS-IS Multi Instance: RFC8202
Multi-Instance IS-IS
One of the nice things about IS-IS is the ability to run IPv6 and IPv4 in the same protocol, over a single instance. So long as the two topologies are congruent, deploying v6 as dual stack is very simply. But what if your topologies are not congruent? The figure below illustrates the difference.

In this network, there are two topologies, and each topology has two different set of level 1/level 2 flooding domain boundaries. If topology 1 is running IPv4, and topology 2 is running IPv4, it is difficult to describe such a pair of topologies with “standard” IS-IS. The actual flooding process assumes the flooding domain boundaries are on the same intermediate systems, or that the two topologies are congruent.
One way to solve this problem today is to use IS-IS multi-topology, which allows the IPv6 and IPv4 routing information to be carried in separate TLVs so two different Link State Databases (LSDBs), so each IS can compute a different Shortest Path Tree (SPT), one for IPv4, and another for IPv6. Some engineers might find the concept of multi-topology confusing, and it seems like it might be overkill for other use cases. For instance, perhaps you do Continue reading
Capgemini Cites Biz Model, Pricing as Hurdles to Serverless Adoption
 Confusion in the serverless market could push out broad adoption by two years.
Confusion in the serverless market could push out broad adoption by two years.
Why leave a vendor job….twice?
Over the past few months I’ve been working hard on my new start-up company PeakFactory, it’s going really well, but for this post I want to focus on the reason why I chose to leave the companies I used to work for. I thought this was relevant, as many people have asked me why, but also in general there is a lot of discussion how to advance your career in different directions.
Why leave a comfortable and good job at all?
Back in 2013 I was working in a very good position, where I had a lot of freedom in choosing the customers I’d like to work on and was involved in all technical aspects of a project (pre-sales, proof of concepts, implementation and support). Still I had this feeling that I wanted to explore more an different areas for a wider audience. Which is why I decided to start working for a networking vendor. My main reason for choosing a vendor is that I could leverage my experience in the technology and apply it for a wider audience (maybe even worldwide)
Why work for Cisco and Juniper?
In early 2014 I got in touch with Cisco and I left Continue reading
It’s the ‘Telecom’ Infra Project, Not the ‘Facebook’ Infra Project
 The open optical group has been the most prominent work of TIP, so far.
The open optical group has been the most prominent work of TIP, so far.