Report Ranks SD-WAN Leaders Based on Q2 Revenues
 The overall SD-WAN market increased 33 percent since first quarter 2017.
The overall SD-WAN market increased 33 percent since first quarter 2017.
Will VMware-AWS Deal Rain on IBM Cloud Partnership?
 IBM was the first cloud provider to partner with VMware.
IBM was the first cloud provider to partner with VMware.
Cumulus content roundup: September
The Cumulus content roundup is back! This month, we’ve journeyed to the far-reaches of the Internet to bring you the best articles, blog posts, and videos about network automation trends. Now, the latest news about containers, clouds and configurations is a click away. Wondering what the CNCF is up to? Or are you more interested in bringing connectivity and visibility to your network? Read on to satiate your curiosities and find the answers to your burning questions. Then, let us know what you think in the comments section below.
Cumulus’ current content
Introduction to Host Pack: Are you searching for software essentials that remove the difficulties of container networking while also bringing visibility and connectivity to the entire stack? Then Host Pack is the product for you! Watch this video to learn about what Host Pack can do for you.
What is FRRouting?: FRRouting (FRR) is the open source software that makes Host Pack’s connectivity so revolutionary. This page goes into deeper, more technical detail about how FRR was developed and how it is used in Cumulus Networks’ Host Pack. Read about FRR here.
NetDevOps: important idempotence: What exactly is idempotence, and what does it have to do with Continue reading
Intel 5G Trial Platform to Support Still Undefined Standard
 The need for cloud and SDN are also linked to 5G network plans.
The need for cloud and SDN are also linked to 5G network plans.
SDxCentral Weekly News Roundup — September 8, 2017
 Security vendor Dataiku raised $28 million; ECI extends switching to metro networks.
Security vendor Dataiku raised $28 million; ECI extends switching to metro networks.
Enterprises Gearing Up for IoT
451 Research finds that companies are planning to bulk up their IT infrastructure to support IoT projects.
Worth Reading: Improving metrics in cyber resiliency
The post Worth Reading: Improving metrics in cyber resiliency appeared first on rule 11 reader.
Vertical Bridge, DataBank Team on Mobile Edge Computing
 Pushing data centers to a cell tower can reduce latency for accessing the cloud.
Pushing data centers to a cell tower can reduce latency for accessing the cloud.
Network Longevity – Think Car, Not iPhone

One of the many takeaways I got from Future:Net last week was the desire for networks to do more. The presenters were talking about their hypothesized networks being able to make intelligent decisions based on intent and other factors. I say “hypothesized” because almost everyone admitted that we aren’t quite there. Yet. But the more I thought about it, the more I realized that perhaps the timeline for these mythical networks is a bit skewed in favor of refresh cycles that are shorter than we expect.
Software Eats The World
SDN has changed the way we look at things. Yes, it’s a lot of hype. Yes, it’s an overloaded term. But it’s also the promise of getting devices to do much more than we had ever dreamed. It’s about automation and programmability and, now, deriving intent from plain language. It’s everything we could ever want a simple box of ASICs to do for us and more.
But why are we asking so much? Why do we now believe that the network is capable of so much more than it was just five years ago? Is it because we’ve developed a revolutionary new method for making chips that are ten times Continue reading
Discussion with Maldivian Operator Dhiraagu (AS7642)
I discussed the BGP Router Reflector design, Settlement Free Peering , Transit Operator choice, Internet Gateways and the Route Reflector connections, MPLS deployment option at the Internet Edge and many other things with the Operator from Maldives. Operator name is Dhiraagu. Autonomous System Number is 7642. Engineer from the ISP Core team, who is […]
The post Discussion with Maldivian Operator Dhiraagu (AS7642) appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
5 Benefits of Next-Generation Firewalls
A look at the advantages NGFWs have over traditional network firewalls.
Networking Trends Discussion with Andrew Lerner and Simon Richard
In June 2017, we concluded the Building Next Generation Data Center online course with a roundtable discussion with Andrew Lerner, Research Vice President, Networking, and Simon Richard, Research Director, Data Center Networking @ Gartner.
During the first 45 minutes, we covered a lot of topics including:
Read more ...OpenStack SDN – Building a Containerized OpenStack Lab
For quite a long time installation and deployment have been deemed as major barriers for OpenStack adoption. The classic “install everything manually” approach could only work in small production or lab environments and the ever increasing number of project under the “Big Tent” made service-by-service installation infeasible. This led to the rise of automated installers that over time evolved from a simple collection of scripts to container management systems.
Evolution of automated OpenStack installers
The first generation of automated installers were simple utilities that tied together a collection of Puppet/Chef/Ansible scripts. Some of these tools could do baremetal server provisioning through Cobbler or Ironic (Fuel, Compass) and some relied on server operating system to be pre-installed (Devstack, Packstack). In either case the packages were pulled from the Internet or local repository every time the installer ran.
The biggest problem with the above approach is the time it takes to re-deploy, upgrade or scale the existing environment. Even for relatively small environments it could be hours before all packages are downloaded, installed and configured. One of the ways to tackle this is to pre-build an operating system with all the necessary packages and only use Puppet/Chef/Ansible to change configuration files and Continue reading
Openstack SDN – Building a Containerized OpenStack Lab
I’m returning to my OpenStack SDN series to explore some of the new platform features like service function chaining, network service orchestration, intent-based networking and dynamic WAN routing. To kick things off I’m going to demonstrate my new fully-containerized OpenStack Lab that I’ve built using an OpenStack project called Kolla.
Continue readingGoogle Dedicated Interconnect Offers Private Network Connection to GCP
 AWS and Microsoft Azure already offer direct connections to their clouds.
AWS and Microsoft Azure already offer direct connections to their clouds.
The Story of Two Outages

Over the last two days, Cloudflare observed two events that had effects on global Internet traffic levels. Cloudflare handles approximately 10% of all Internet requests, so we have significant visibility into traffic from countries and networks across the world.
On Tuesday, September 5th, the government of Togo decided to restrict Internet access in the country following political protests. The government blocked social networks and rate-limited traffic, which had an impact on Cloudflare.
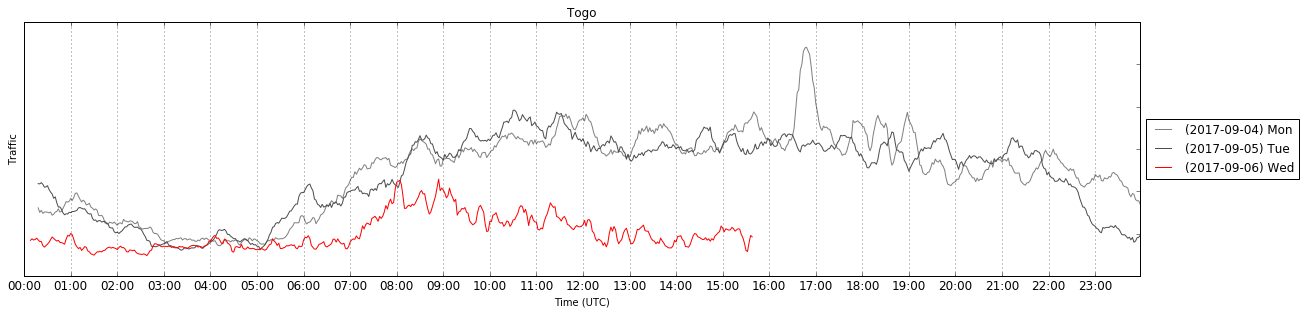
This adds Togo to the list of countries like Syria (twice), Iraq, Turkey, Libya, Tunisia, etc that have restricted or revoked Internet access.
The second event happened on Wednesday, September 6th, when a category 5 hurricane ravaged the Caribbean Islands.
The affected countries at the moment are:
- Anguilla
- Antigua and Barbuda
- British Virgin Islands
- Puerto Rico
- Saint Barthelemy
- Saint Kitts and Nevis
- Saint Martin
- Sint Maarten
- U.S. Virgin Islands
Losing the routes
Most of the network cables are buried underground or laying at the bottom of the oceans but the hardware which relies on electricity is the first one to go down.
Cell towers sometime have their own power source thus allowing local phone calls but without a backbone no outside Continue reading
